About 15% of all Android Adware Infections Reside in the System Partition
- Kaspersky estimates that a large portion of adware infections lie in the system partition and system libraries.
- This is done for persistence, and also to make it impossible for the users to remove the planted malware.
- Many vendors like Meizu and Xiaomi openly admit that they are planting adware themselves by default.
According to a report by Kaspersky, roughly 15% of all adware infections that plague the Android ecosystem are planted in the system partition. This makes them especially hard to get rid of, while even trying to do it may result in the bricking of the device. That is because these adware tools are often embedded in the code of system apps and system libraries, so fiddling with them creates a chain of negative effects over a wide spectrum of things. This adware either manages to nest in the system partition or is part of the device’s “out-of-the-box” experience due to a supply chain compromise or a business model choice.
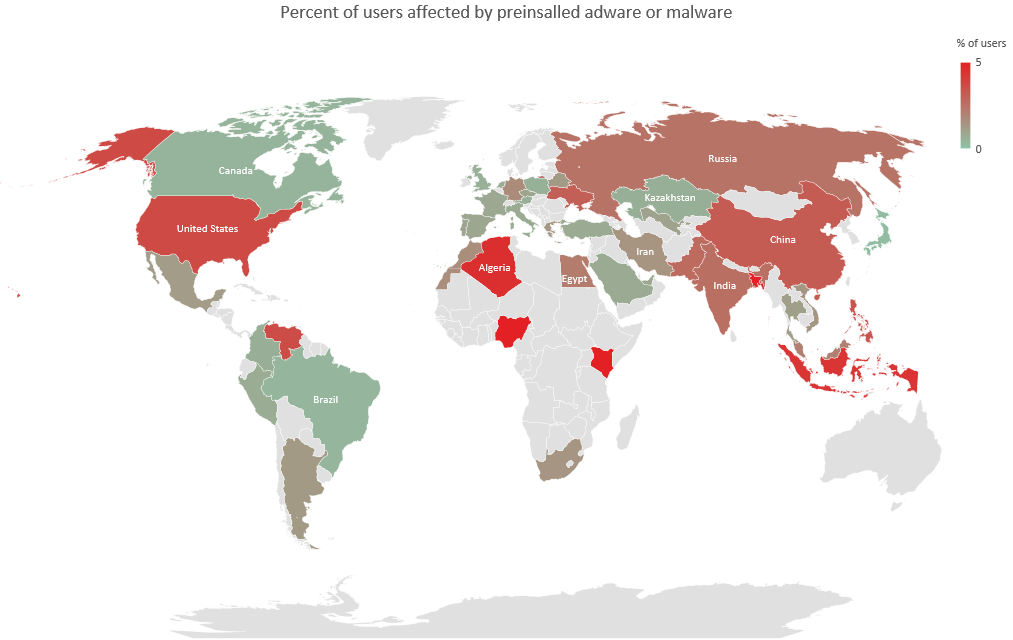
Heatmap of pre-infected devices,
Source: Kaspersky
We have seen and analyzed this type of malware through the example of the “xHelper,” which is a very persistent piece of software. The dropper and ad clicker trojan gains root access on the device, enabling it to plant a modified version of the “lib.co” library on the system partition. Even resetting the infected device won’t delete that library, so xHelper is fetched again on the refreshed OS. This is a new type of a problem, and unfortunately, it goes well beyond just the xHelper example.
In fact, Kaspersky reveals that between 1% and 5% of its customers encounter this kind of adware. As for those who are using devices that are in the lower price segment, the percentage of infections can go up to 27%. The report mentions “Lezok” and “Triada” as two of the most common types of persistent malware, but these trojans are just the tip of the iceberg, really. Kaspersky presents an entire set of system apps that come pre-infected with malware or are infected along the way. The case of having adware installed on the device by default is a particularly nasty one, as the user never did the inappropriate thing of downloading unsafe stuff from untrustworthy sources.
The researchers present the example of Meizu, which has admitted having adware preinstalled on its devices, embedding it on the default AppStore app. We have seen the same happening with Alcatel (TCL) smartphones, hiding malicious code in the default weather app, which engaged in sending data to Chinese servers. More recently, we have covered the case of Samsung’s bloatware app named “Device Care,” which many users characterized as Chinese spyware.
All that said, there’s only one thing that people can do to escape this situation: install clean OS images. Finding compatible firmware for your device and model can sometimes be tricky, so you may want to consider projects like the LineageOS system instead. Even then, your bootloader will have to be unlocked for the system to be installed. So, in summary, the best approach would be to do your research before choosing a brand or device.