Hundreds of Free VPN Apps Expose User Data on Android and iOS
- Outdated Encryption: Some VPN apps use vulnerable OpenSSL versions, exposing TLS keys, credentials, and private messages.
- Excessive Permissions: Apps request dangerous privileges, enabling keylogging, GPS tracking, and unauthorized access to user data.
- Enterprise Risks: Vulnerable VPNs can bypass encryption, leak logs, and compromise corporate BYOD security without detection.
A comprehensive study by Zimperium zLabs analyzing 800 free VPN apps on Android and iOS has exposed data and led to security and privacy vulnerabilities. Many apps that promise online protection are instead exposing users to serious risks, including weak encryption, excessive permissions, and potential data leaks.
How VPN Apps Work and Where They Fail
VPNs create an encrypted tunnel between a device and a server, concealing IP addresses and securing online activity. However, Zimperium’s research shows that some VPNs use outdated libraries, fail to validate digital certificates, and request permissions far beyond their intended functionality. These flaws undermine the very privacy these apps claim to provide.
For organizations with bring-your-own-device (BYOD) policies, vulnerable VPN apps can also create enterprise-level risks, exposing sensitive business data and user credentials.
How and Why Free VPNs Expose Data
1. Outdated Cryptography
Three Android apps still use a legacy OpenSSL library vulnerable to Heartbleed (CVE-2014-0160). This flaw allows attackers to access TLS keys, passwords, and private data. Despite patches being available since 2014, these VPNs remain insecure.
2. Communications Channel Weaknesses
Around 1% of apps bypass TLS certificate validation, allowing Man-in-the-Middle (MitM) attacks. Attackers could intercept, decrypt, and read supposedly secure traffic without user awareness.
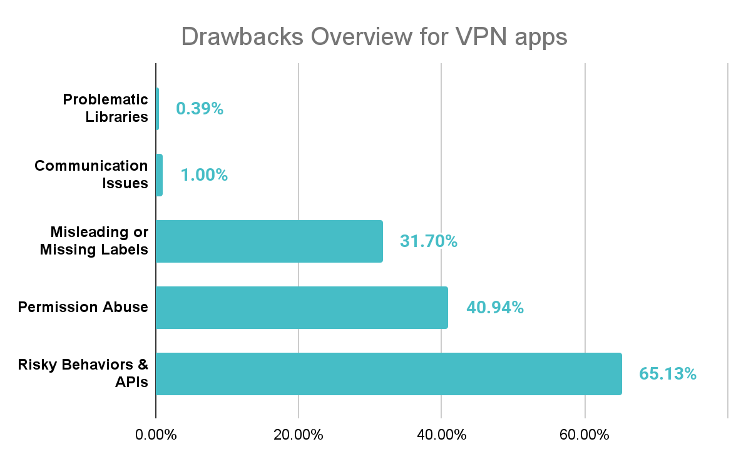
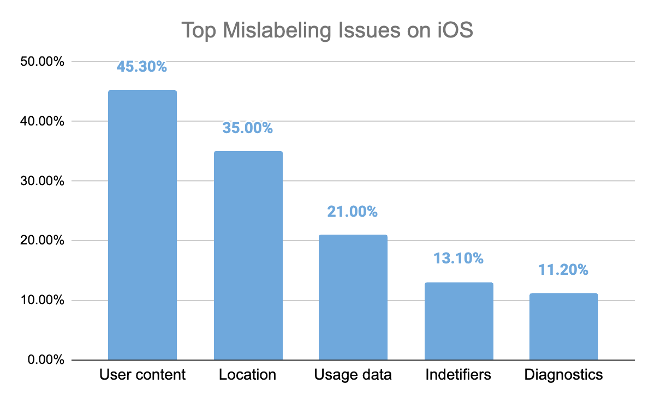
3. Misleading or Missing Labels
On iOS, 25% of VPN apps lacked a valid privacy manifest, and many misrepresented their data practices, undermining user consent and transparency.
4. Permission Abuse
Android apps often request AUTHENTICATE_ACCOUNTS and READ_LOGS, enabling account takeover, keylogging, and user behavior tracking. iOS apps request LOCATION_ALWAYS and private entitlements, allowing persistent GPS tracking and deep OS access.
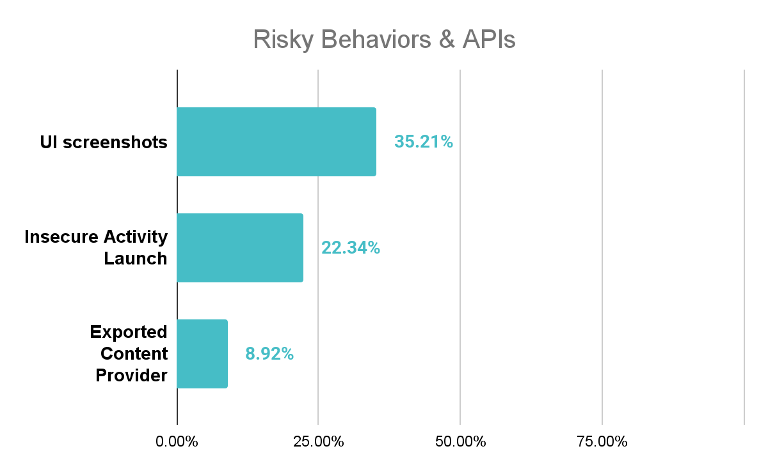
5. Risky Behaviors and Insecure APIs
Some apps expose activities or content providers without proper safeguards, enabling malicious apps to query logs, inject settings, or disable encryption. Others can capture screenshots, hijack UI components, or execute system-level commands, posing severe privacy threats.
Enterprise and Developer Implications
Vulnerable VPN apps can become a pivot point for attacks in corporate environments. Zimperium’s Mobile App Vetting platform allows organizations to:
- Detect weak cryptography, outdated SDKs, and missing jailbreak/root detection.
- Flag apps requesting excessive permissions beyond core functionality.
- Identify privacy leaks, insecure communications, and unsafe data storage.
For developers, zScan helps proactively assess apps for vulnerabilities before release, ensuring safer tools for users and enterprises.
Conclusion
While VPNs are widely trusted to protect online privacy, Zimperium’s research highlights that not all VPN apps are safe. Users and organizations must carefully evaluate apps for encryption quality, permissions, and privacy practices. Proper vetting and continuous monitoring are essential to avoid exposing sensitive personal or corporate data.