972 Million Google Play VPN Users at Risk, Citizen Lab Warns
- Massive Risk: Google Play 20+ VPN apps with 972M installs have flaws and expose users to major privacy threats.
- Hidden Links: Providers claim independence but share code, infrastructure, and hard-coded passwords.
- Severe Flaws: Apps vulnerable to decryption, packet injection, and secret location data collection.
Researchers from Citizen Lab have revealed alarming findings about popular VPN apps on the Google Play Store. More than 20 VPN applications with a combined 972 million downloads have been found to contain serious security flaws that could compromise user privacy and allow attackers to decrypt transmitted data.
VPN Providers Linked Despite Claims of Independence
According to the Citizen Lab report, the apps appear to be distributed by companies that present themselves as independent providers but are in fact linked through shared infrastructure, code, and development practices.
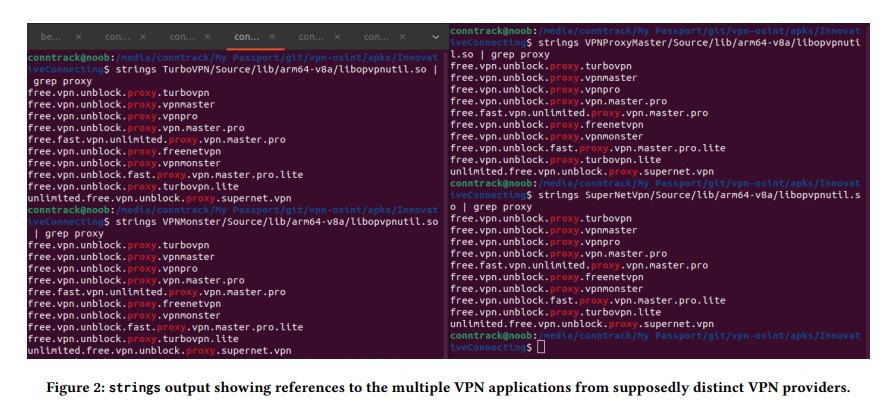
Earlier research already identified ties between three Singapore-based VPN companies: Innovative Connecting, Autumn Breeze, and Lemon Clove. These companies had been previously connected to a Chinese national, and now new evidence further links them to additional apps and developers.
Citizen Lab notes that the VPN services from these providers share common code, dependencies, and even hard-coded passwords, a major vulnerability that could allow attackers to decrypt all user traffic.
Apps With Hundreds of Millions of Downloads Affected
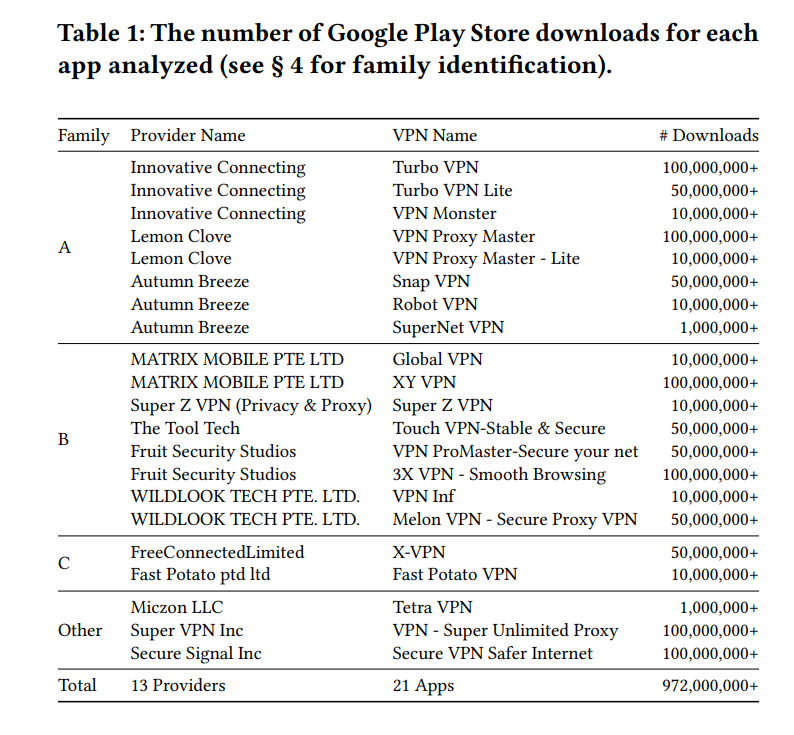
Eight applications developed by the three companies, Turbo VPN, Turbo VPN Lite, VPN Monster, VPN Proxy Master, VPN Proxy Master – Lite, Snap VPN, Robot VPN, and SuperNet VPN, were found to have major overlaps in their implementation. Collectively, these apps account for more than 330 million installs.
Researchers say the apps support IPsec and Shadowsocks protocols. Shadowsocks, originally designed to bypass the Great Firewall of China, uses symmetric encryption and outdated ciphers, making it vulnerable to multiple forms of attack. The use of hard-coded passwords further exposes users to connection tampering and packet injection.
In addition, all eight apps secretly collect user location data, apply weak encryption, and bypass automatic security controls using anti-analysis mechanisms.
Other Providers Potentially Connected
Citizen Lab also identified another group of companies, Matrix Mobile PTE LTD, ForeRaya Technology Limited, Wildlook Tech PTE LTD, Hong Kong Silence Technology Limited, and Yolo Mobile Technology Limited, that may be connected to the trio.
Their apps, which have been downloaded more than 380 million times, also showed signs of code similarities, obfuscation, and reliance on identical protocols. They too were vulnerable to connection tampering attacks and used obfuscated passwords while connecting to the same IP infrastructure.
Two additional providers, Fast Potato Pte. Ltd and Free Connected Limited, were also linked through their use of the same proprietary VPN protocol implementation. In fact, recently, the Chrome VPN Extension with more than 100K installations was exposed to spyware, resulting in major data leaks.
Risks of Google Play VPN App Flaws to Users
Citizen Lab warns that these security and privacy flaws can affect users in multiple ways:
- Exposure to traffic interception and modification
- Surreptitious collection of location data
- Loss of trust due to hidden ties between VPN providers
- Increased risk from outdated cryptographic protocols
While VPNs are typically marketed as tools to protect online privacy and secure data, these findings suggest that millions of Android users may instead be putting themselves at risk by relying on these apps.