A Trojanized 2FA App Is Delivering the Lazarus “Dacls” RAT on macOS
- An app called TinkaOTP or MinaOTP is actually a Lazarus creation aiming to infect macOS with a RAT.
- The RAT is “Dacls,” and it features more or less the same plugins and functionality that we’ve seen before.
- Lazarus is targeting Chinese users at this time, probably in the context of a cyber-espionage operation.
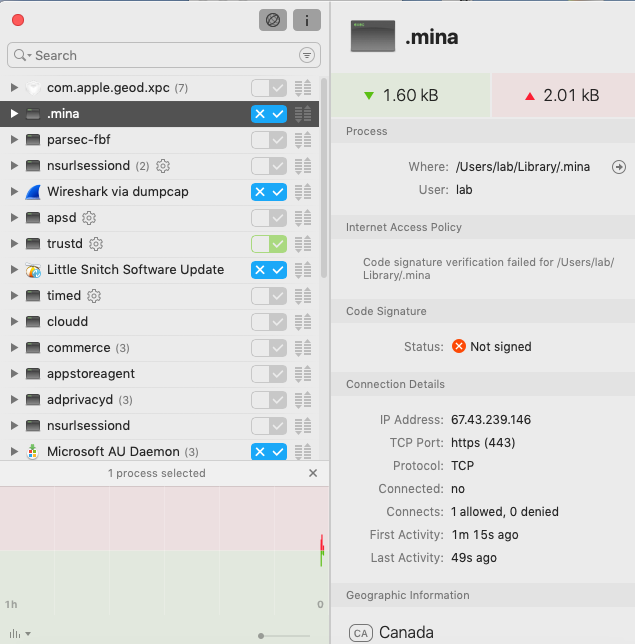
The Lazarus group (APT 38), North Korea’s most notorious and dangerous hacking team, is now deploying a novel method to infect macOS systems with its “Dacls” RAT (Remote Access Tool). More specifically, they are using a trojanized two-factor authentication application named “MinaOTP” or “TinkaOTP,” which targets Chinese speakers. This method of distribution was first spotted by Malwarebytes researchers on April 8, 2020, and at that time, VirusTotal indicated that no AV engines were spotting the danger. This is yet another example of the sophistication of the Lazarus group, and the effectiveness of their custom tools.
Source: Malwarebytes
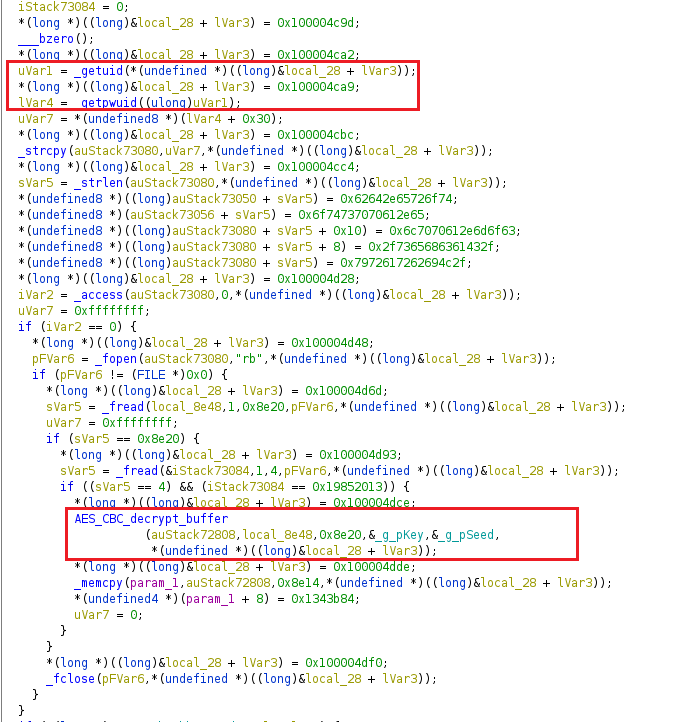
The “Dacls” RAT launches automatically with the system boot, by planting a relevant entry on the “LaunchDaemons” or the “LaunchAgents.” Upon its initiation, a plist file is created by using code that is embedded in the application itself. It means that there’s no C2 communication required for the establishment of the RAT’s persistence. From there, the malware collects information such as the Puid, Pwuid, plugins, etc., and encrypts everything by using the AES algorithm, creating a config file. The config file is named to look like an ordinary Apple Store database file, so as to avoid detection or raising user suspicions.
Source: Malwarebytes
There are three hardcoded C2 servers in the app, so once the config file initiates, it attempts to connect with them to receive commands. The loop through which “Mina” goes is uploading information to the C&C server, download new config files, uploading “getbasicinfo” data, and sending heartbeat information. These four steps are exactly the same ones that happen in the Linux version of the Dacls RAT, so the porting to macOS didn’t bring anything new on that part. Similarly, the six plugins that are present on the Linux version are here too, although there are some minor technical difference
- CMD plugin – executes commands through a reverse shell to the C2
- File plugin – read, delete, download, and search files in a directory
- Process plugin – kill, run, and get process ID
- Test plugin – check the connection to an IP and port specified by the C2
- RP2P plugin – proxy server that acts as a diversion middleman
- LogSend plugin – worm scanner, log server checker, and system commands executioner
- Socks plugin – additional plugin compared to the Linux version of the RAT, serves as an intermediary proxy, complementing the role of the RP2P
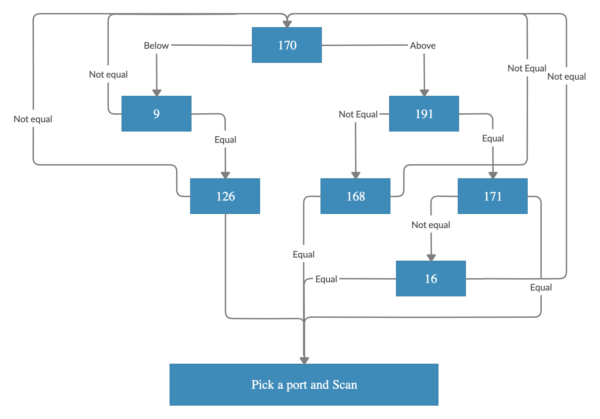
Worm scanning procedure, Source: Malwarebytes
The researchers have also got to analyze a new variant of the RAT, which downloads the malicious payload by using a curl command. They have reported everything to VirusTotal, so most AV engines are identifying the threat now. It means that you should update your security solution and its signatures, and be careful with the 2FA tools that you’re using on macOS. Lazarus is engaging in cyber espionage operations, so this RAT was made to infect specific targets. Still, this is no reason to feel any safer. Also, you shouldn’t neglect to take the appropriate protection measures.