Top Ten Signs Which Indicate That You’re Reached by a BEC Scammer
- If you see your own name in your inbox, maybe you should be careful with that message.
- Agari warns that BEC scammers start to take a more personalized approach to trick their victims.
- Even the 2020 presidential candidates remain largely unsecured against BEC campaigns.
BEC (Business Email Compromise) cases are on the rise and have been for quite a while, which means that they’re working, and victims are still mostly unaware of the signs that accompany and characterize them. The FBI reported 351000 successful BEC scams last year, resulting in losses of $1.3 billion. According to the latest Q2 2019 Agari report on the matter, the situation has gotten even worse this year, with the scammers evolving their techniques at a rampaging pace. 30% of the attacks originate from compromised accounts, and 90% of high-profile companies and persons remain unprotected against this type of attacks.
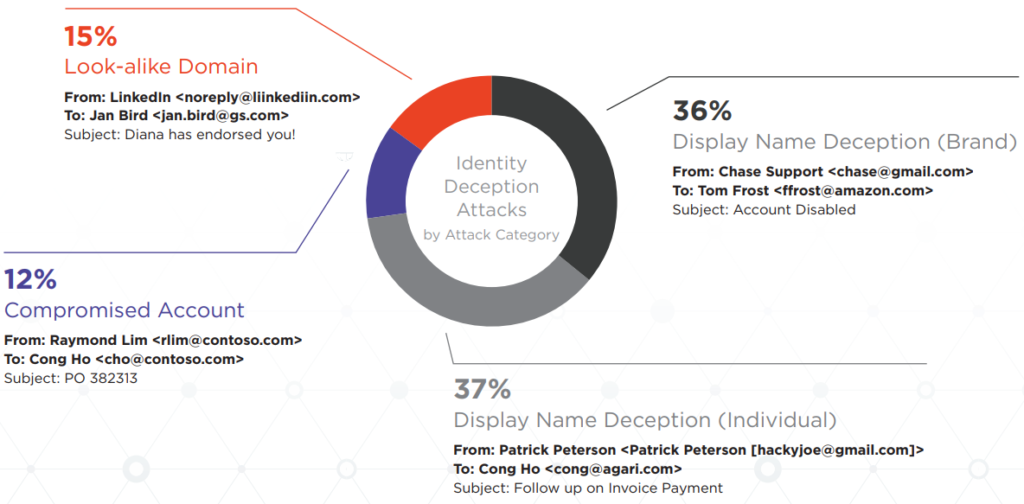
The best way to protect yourself against email threats is to identify patterns of deceit and most common signs of scam activity. First of all, 67% of the BEC attacks are launched from free webmail accounts, with the most prevalent being Roadrunner (15.3%), AOL (12.8%), and Gmail (10.4%). In all cases, the scammers will try to impersonate a senior executive or member of the higher management in the targeted company. To achieve this, they are using look-alike domains, similar display names of high-standing individuals, or the compromised account itself, which is the easiest way to convince all recipients of the fraudulent email messages.
image source: agari.com
As for the subject lines that are used in BEC scams, the following constitute the top ten list:
- Request – 7.6%
- [FIRST NAME] – 7.2%
- Task – 3.7%
- Hello [FIRST NAME] – 3.5%
- Hi [FIRST NAME] – 2.5%
- Payroll – 2.1%
- quick task – 2.1%
- [FIRST/LAST NAME] – 1.9%
- Direct Deposit – 1.7%
- Available? - 1.5%
From the above list, it becomes evident that a lot of these BEC scams are going personal, addressing the recipient with their first and/or last name. In fact, Agari reports that a total of 20% of BEC emails are personalized, which indicates a growing trend.
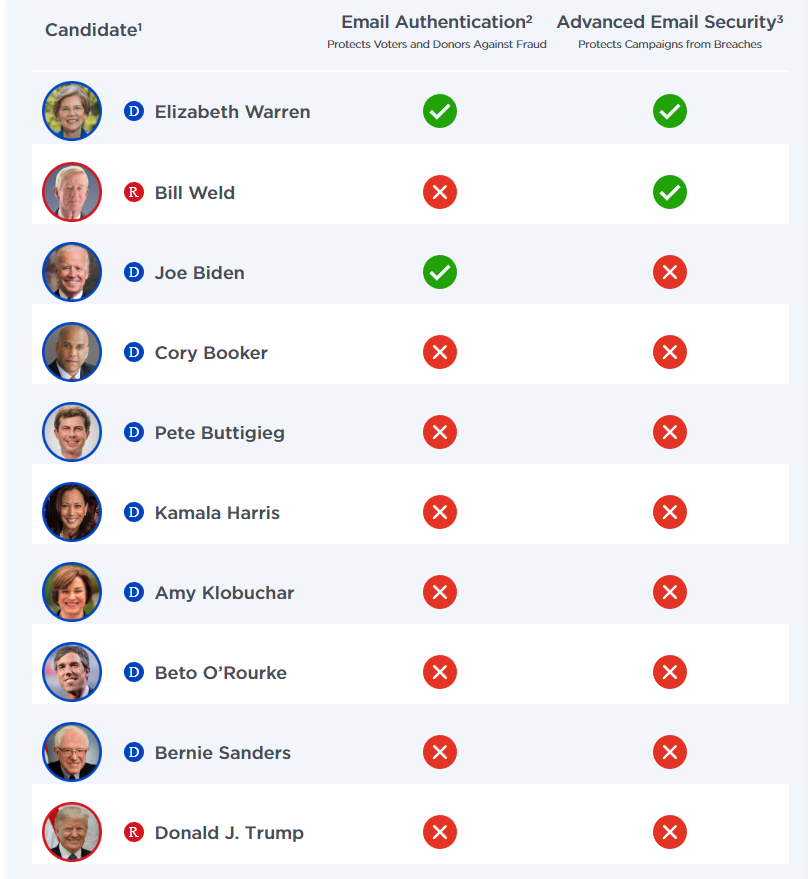
To highlight the fact that even high-profile individuals are not paying enough attention to the importance of securing their inbox, Agari is monitoring the steps that US presidential candidates have taken thus far. With Clinton’s campaign receiving a blow due to the very fact of an email account breach, one would expect that 2020 candidates would take a more cautious approach on this matter. However, this is not the case, as 90% of the current contenders do not deploy an advanced email security layer, and neither do they use sophisticated email authentication methods. This means that voters and donors can fall victims to fraudsters and that their campaigns are susceptible to a breach.
image source: agari.com
What do you think about these stats? Share your views in the comments section down below, and also on our socials, on Facebook and Twitter.