Nearly Half of All Business Email Attacks Request Money Transfers – Barracuda Networks
- 46.9% of BEC attacks request wire transfers
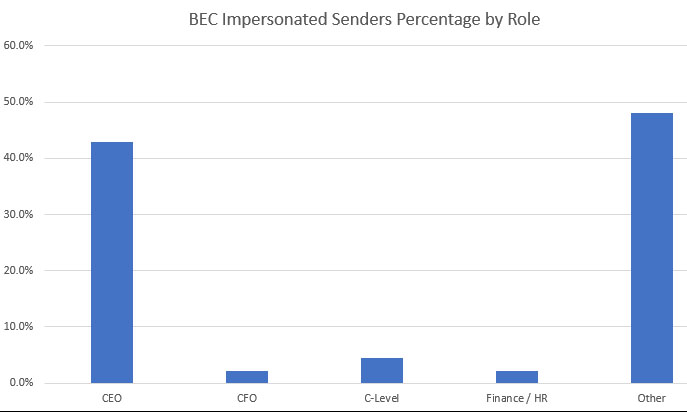
- 42.9% of attackers impersonate the CEO
Business Email Compromise (BEC) attacks are becoming more and more popular and the worst part is that they're harder to spot than ever.
According to a brand new report from IT security and data protection company Barracuda Networks, most BEC scams nowadays feature no links, which are usually easy to spot by emailing systems. Statistics compiled for 3,000 BEC attacks from the Barracuda Sentinel system show that nearly 60% of all attacks lack a link, which is one of the most common ways to trick people into sharing sensitive data.
The Barracuda report indicates that 46.9% of attacks requested the recipient do a wire transfer, 12.2% sought to establish a rapport, with 0.8% looked to straight-out steal information. Some 40% of the attacks did feature the malicious links. "The most common attack is a link to a fake login page. Oftentimes the links also take the recipient to a site that downloads malicious malware to their device," Barracuda VP for email security Asaf Cidon tells TechNadu.
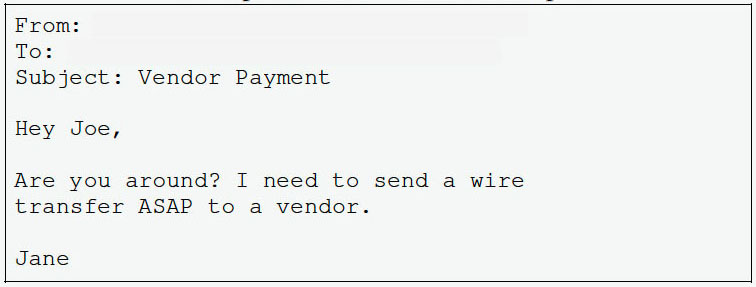
BEC attack sample - via Barracuda Networks
The CEO impersonator
The company took things a step further and randomly selected 50 companies that use their service and compiled a chart featuring the roles of the recipient of the attack, as well as the impersonated sender. Unsurprisingly, nearly 43% of all attackers tried to impersonate the CEO of the company. This means that employees need to pay extra attention to the email addresses they receive messages from and to maybe even check if the request is real by discussing directly with the CEO, especially if it seems out of place. Employees working as CFO and in the Finance and HR departments were most often targeted by attackers, which correlates with the high demand for wire transfers we've previously discussed.
BEC attackers like to impersonate important people - via Barracuda Networks
Barracuda recommends extensive training for employees, but we've seen time and time again that this won't solve all problems because mistakes happen. So, we asked Asaf Cidon what other solutions are there - better scam detection systems built into emails? A list of trusty email addresses?
"A list of trusted emails is usually not very effective, because in many organizations employees often use their personal or university email addresses (in fact the CEO is often the biggest culprit), and there are legitimate mailing systems that impersonate employees, like Salesforce, Marketo, and LinkedIn. For this reason, an AI-based approach is more effective than a rigid rule-based approach, which typically suffers from high false positives and missed attacks," the VP told us, adding that Barracuda already has an AI-based product, the aforementioned Barracuda Sentinel, that can automatically detect spear phishing.