‘Thallium’ Continues Targeting South Korean Government and Key Entities
- ‘Thallium’ continues to target key South Korean entities with the AppleSeed malware.
- It all starts with a phishing email that points to well-crafted phishing sites that mimic Gmail.
- The malware can captures screenshots, log keyboard input, and exfiltrate files from hard drives.
The North Korean group of actors known as ‘Thallium,’ or otherwise the ‘Kimsuky’ APT, are continuing their active targeting of various South Korean key entities and persons. The KISA (Korean Internet and Security Agency) has published a very detailed report a couple of months back containing all the details on how the attackers move against their targets. Moreover, Malwarebytes - which is also following the particular APT - has now published its own write-up on the topic.
Based on the latest available data, the targets of Thallium are the following:
- Ministry of Foreign Affairs, Republic of Korea 1st Secretary
- Ministry of Foreign Affairs, Republic of Korea 2nd Secretary
- Trade Minister
- Deputy Consul General at Korean Consulate General in Hong Kong
- International Atomic Energy Agency (IAEA) Nuclear Security Officer
- Ambassador of the Embassy of Sri Lanka to the State
- Ministry of Foreign Affairs and Trade counselor
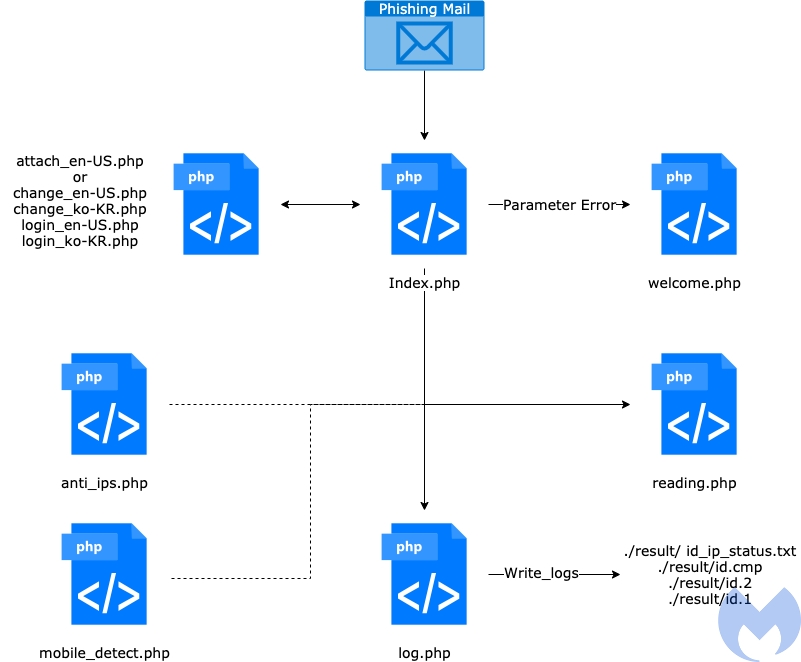
The attacks start by sending a phishing email to the target, sent from a mimicked infrastructure that appears like a legit and well-known site at a glance. Typically, we see the spoofing of Google and the Gmail service, but there’s also Hotmail, Microsoft Outlook, Telegram, and more. Example URLs include “login[.]gmail-account[.]gq”, “accounts[.]goggle[.]hol[.]es/MyAccount”, and also “ns1.microsoft-office[.]us”, but there are many more.
The goal is to collect the target’s credentials or at least their more critical email addresses. These are then used for a more sophisticated spear-phishing campaign that relies more heavily upon social engineering. Thallium targets both English and Korean-speaking victims, so they have put in the extra work to prepare their phishing pages, make them support both languages, and detect what the visitor is using to adjust automatically.
As for the infrastructure, Thallium is using several parts that have been reused in the recent past, like, for example, the AppleSeed backdoor C2 communications. Right now, the threat group is using two backdoors, one for Windows users and one for Android devices, and they are both sharing the same infrastructure.
And finally, in terms of the capabilities of this malware, there is a keylogger that captures key presses and stores them in a log.txt file, there’s a screenshot capture tool that uses API calls for the purpose, and there’s also a module that can identify the inserting of a USB drive and collect its data to send it to the C2 server at a later stage. Of course, file exfiltration from local hard disks is also included, with the relevant thread looking for txt, ppt, hwp, pdf, and doc files in the Desktop, Documents, and Downloads.