TAG-144 (Blind Eagle) Targets South American Governments in Sustained Campaign
- Persistent operations: Blind Eagle continues its advanced spearphishing and RAT-based malware campaigns.
- Malware targets: TAG-144’s focus remains primarily on South American and particularly Colombian government entities.
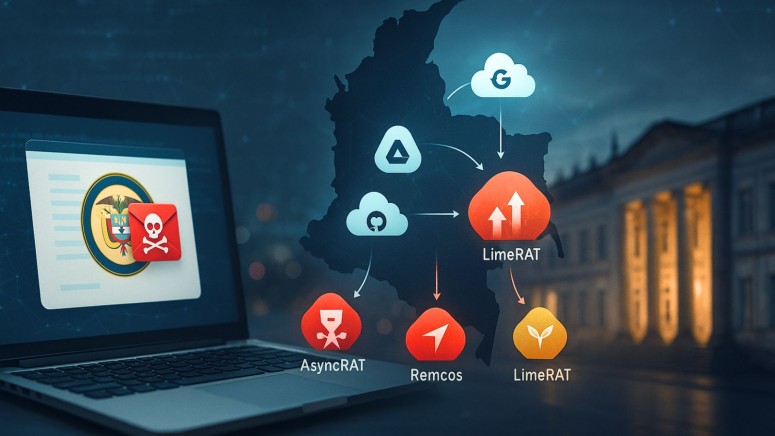
- Remote access: The threat actor deploys AsyncRAT, DcRAT, Remcos RAT, XWorm, and LimeRAT in this campaign.
A sophisticated multi-vector cyber operation orchestrated by the Blind Eagle threat group (also known as APT-C-36 and TAG-144) targets critical infrastructure across South American governmental institutions via a multi-stage infection chain that leverages an expanding set of legitimate internet services (LIS) and steganography to hide malicious content and evade detection.
The comprehensive Recorded Future's Insikt Group analysis reveals five distinct operational clusters active throughout 2024 and 2025, representing one of the most persistent South American cybersecurity threats documented in recent years.
Advanced Persistent Threat Infrastructure and TTPs
The operational methodology employs advanced spearphishing campaigns leveraging compromised governmental email accounts from entities that include Colombia's judicial branch. These campaigns utilize geofencing mechanisms that redirect non-Colombian IP addresses to legitimate government websites.
TAG-144 cyber operations demonstrate evolved tactical sophistication, utilizing an extensive infrastructure comprising Colombian ISP-hosted IP addresses and virtual private servers (VPS) such as the Russian hosting service Proton666 and VPN services like Powerhouse Management, FrootVPN, and TorGuard.
Recent reports speculated links between Blind Eagle and Proton66. Cybersecurity researchers suspect the group also uses compromised network devices repurposed as reverse proxies.
The Colombian cybercrime group maintains operational continuity through dynamic DNS services, including duckdns[.]org, noip[.]com, and con-ip[.]com.
It also deploys crypters such as HeartCrypt and PureCrypter and open-source and cracked remote access trojans (RATs) such as AsyncRAT, Remcos RAT, DcRAT, njRAT, LimeRAT, QuasarRAT, BitRAT, and a Quasar variant known as BlotchyQuasar.
Steganographic Payload Delivery and C2 Infrastructure
TAG-144's infection chains incorporate advanced steganographic techniques, which were also seen in a recent UpCrypter phishing campaign, embedding malicious PowerShell scripts within image files hosted on legitimate internet services, including Archive.org, Discord, and GitHub.
Strategic Implications for Regional Cybersecurity
The Blind Eagle threat group demonstrates a consistent focus on espionage and financially motivated attacks. The group's primary targets include Colombian government institutions at local, municipal, and federal levels, with additional victims in the healthcare, retail, and energy sectors. This sustained targeting suggests a sophisticated understanding of the regional political and economic landscape.
TAG-144's operational persistence, spanning multiple years with consistent targeting patterns, underscores the evolving nature of South American cybersecurity threats requiring enhanced regional coordination and defense capabilities.
TechNadu first reported on Blind Eagle sending phishing emails impersonating government and banking institutions in Latin America in August 2024. A March 2025 report detailed a Blind Eagle campaign targeting Colombian judicial and public sector organizations with malicious files that mimicked documents from courts and legal offices to distribute the Remcos RAT.