Researchers Reveal that Smart TVs Send Private Data to Various Third Parties
- Smart TVs or any IoT device whatsoever is not keeping your data strictly at home.
- Researchers found that all of our smart devices communicate with various third parties.
- Most of the data that travels this way is encrypted, and what it isn’t is usually not PII.
Two studies from U.S. and U.K. universities confirm people’s fear that their smart TVs are "secretly" collecting data and send them to third parties such as Netflix, Amazon, and Facebook. The private information that is sent includes the IP address of the network that the TV is connected to, and any other location information the devices can gather. Other types of data that are shared under the table include the user’s Ad-ID, what they like to watch, and for how long they like to watch it.
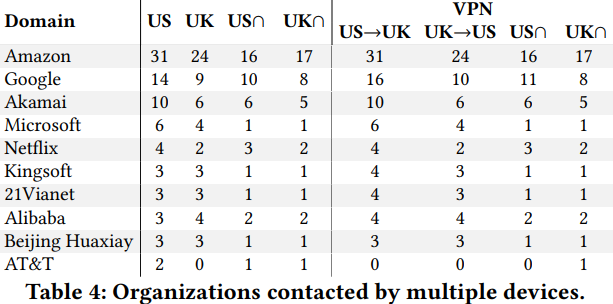
According to the currently available stats, 68% of U.S. households have connected their TVs to their home internet network. Not all of these TVs are smart, as many of them are using dongles and TV boxes such as Apple TV, Fire TV, and Roku. The researchers have collected data by monitoring the activity of all these TV sticks, and IoT devices in general, finding that almost all of them connect to several third-party destinations without giving the user any indication about it. The top of the list is occupied by Amazon, with Google and Akamai following, and Microsoft and Netflix receiving some data too.
Source: moniotrlab.ccis.neu.edu
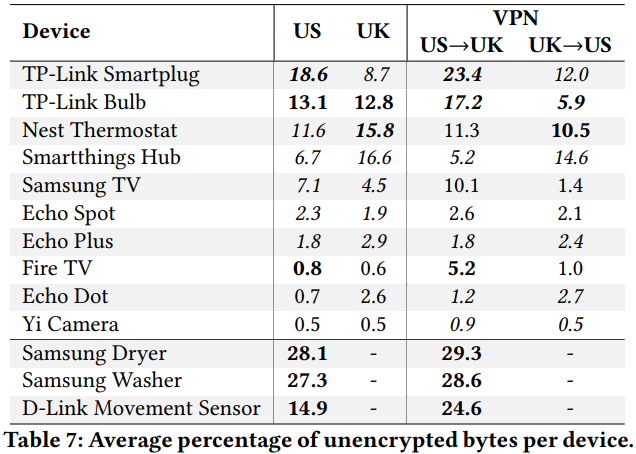
Some of this communication occurs for benign reasons such as seeking cloud hosting services. However, that doesn’t remove the privacy concerns that the users should have. If a company receives multiple data from various IoT devices, they could correlate it based on the common IP address, combine it to create a more complete set of data, and finally profile the person who is the user. One way to deal with this implication is to introduce encryption in the communication between IoT and third parties, but as the researchers point out, not all manufacturers pay attention to this factor. For example, TP-Link’s smart plug is leaving about 1/5 of all its data traffic unencrypted, Samsung TV reaches up to 10%, Samsung Dryers and Washers up to 30%, and the Nest Thermostat ranges between 10-15%.
Source: moniotrlab.ccis.neu.edu
By analyzing these unencrypted data, the researchers have found limited identifiable content like UUID, MAC address, device ID, etc. The cases were email addresses, usernames, and geolocation data was left in plaintext form was thankfully rare. In overall, the researchers measured a percentage of information disclosure of 57.45%, without requiring MITM techniques to eavesdrop this data.
Have something to comment on the above? Let us know of your opinion in the section down below, or join the discussion on our socials, on Facebook and Twitter.