SpeakUp Backdoor Trojan Targets Linux Servers and Threatens Critical Infrastructure
- SpeakUp Trojan has already infected 70,000 Linux servers and AWS machines.
- The Trojan is currently occupied with crypto-mining, but that is unlikely to be its real deal.
- Researchers warn that security tools are currently not catching it and that it’s a well-built piece of malicious code.
Researchers at the Check Point have discovered a new campaign of Trojan distribution that concerns Linux servers. The Trojan known as “SpeakUp” (due to its C&C domain) sports a set of vulnerability exploitation methods, indicative of the fact that the developers behind it are knowledgeable and have created it through meticulous needlecraft work. As Linux is not hugely popular as a desktop OS, its users are practically enjoying a piece of mind when it comes to viruses and malware. However, over 90% of servers worldwide run on Linux, and so do 100% of our supercomputers globally, so if you’re targeting high-profile systems, you will need to create a highly sophisticated weapon.
SpeakUp Anti-Virus Results, Source: research.checkpoint.com
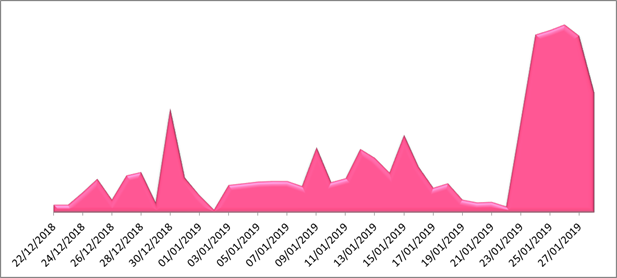
According to Check Point, SpeakUp meets these requirements, as it can evade all security vendors and search engines, exploiting remote code vulnerabilities found in six individual Linux distributions. The Trojan is already out there on 70,000 servers, getting further propagated through a Python script that scans for more Linux servers in the internal and external subnets, and arbitrarily running code that taps onto them as well. Upon the infection, the victim server is registered to the C&C and then SpeakUp just waits for the server to send the commands that it needs to run. All requests are encrypted with base64, so it stays hidden and obfuscated.
SpeakUp propagation rate, source: research.checkpoint.com
The exploitation scope comprises the following vulnerabilities:
- NoneCMS ThinkPHP Remote Code Execution (CVE-2018-20062)
- Oracle WebLogic WLS Security Component Remote Code Execution (CVE-2017-10271)
- Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-2018-2894)
- Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-2016-3088)
- JBoss Seam 2 Framework Remote Code Execution (CVE-2010-1871)
- JBoss Enterprise Application Platform Invoker Servlets Remote Code Execution (CVE-2012-0874)
As Check Point researchers point out, their analysis shows that the Trojan is comparable to the craftsmanship of the malware developer that goes by the name “Zettabit”. Further investigation of the C&C server points to a GitHub project created by a user that is also registered on Hack Forums and is possibly a Russian hacker.
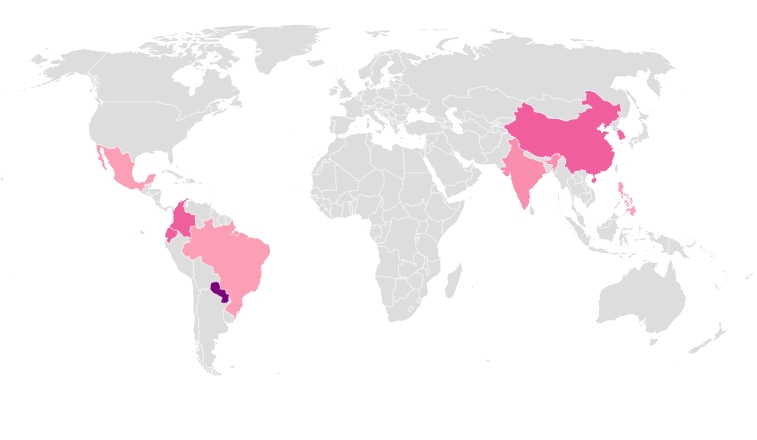
SpeakUp infection map, source: research.checkpoint.com
Discovering this threat early on is very positive as it holds the potential to evolve into a massive botnet problem for many Linux servers out there. Right now, SpeakUp is focusing on serving XMRig miners, but Check Point analysts believe that crypto-mining Monero is just a side task to keep the Trojan occupied until it gets adequately established on a worldwide scale.
Would you say that SpeakUp has silently already gotten out of hand, or is it just a minor threat? Let us know of your opinion in the comment section below, or kickstart a discussion with our socials community on Facebook and Twitter.