KONNI Malware Expands to South East Asia and Eurasia
- Notorious malware Konni that was active in North Korea is now spreading to South East Asia and Eurasia according to reports.
- A new iteration of the KONNI malware has been found with attacks traced back to early 2018.
- The new iteration of the malware is being called NOKKI due to the coding differences.
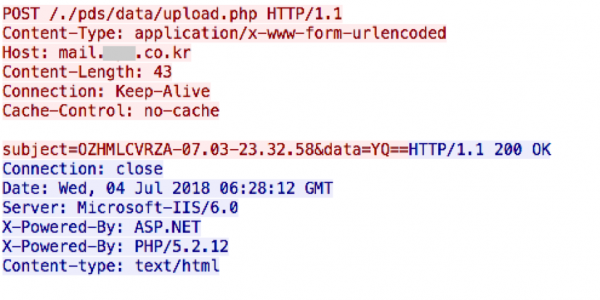
Over the last three years, a large number of malware attacks took place all over North Korea, and the malware was termed KONNI by security researchers globally. A new wave of attacks that are similar in nature was spotted recently. However, despite the similarities, security researchers at Palo Alto Networks have spotted a number of differences leading them to believe that they have not been developed by the same cyber attackers.
Palo Alto Networks has renamed the malware from KONNI to NOKKI internally to reflect the similarities while classifying them as unique to each other. There is a sizeable overlap between the code in both malware. However, security researchers have identified a tenuous relationship between a known hacker group that goes by the name of ‘Reaper.’
Image Courtesy of Palo Alto Security
The latest security vendor to analyze the malware is Cylance, who believe that hacktivism could be the motivation behind these recent attacks. Security experts at Cylance revealed that the KONNI attacks could be linked to the DarkHotel APT campaign which was first uncovered by Kaspersky Lab. The DarkHotel APT campaign was responsible for stealing customer data from luxury hotels.
Cylance Threat Guidance Manager Kevin Finnigin revealed “[Konni] essentially is a still evolving, full-featured RAT,". The company's analysis suggests that additional capabilities are probably under development.”
The new KONNI payload is used to target victims in Eurasia and Southeast Asia. The targets are politically motivated, and the attacks by the payload are designed to compromise infrastructure of 'deliver and command' controls.
Security researchers have been unable to trace the source of the campaigns despite the unknown threat being prevalent for three years now. The new iteration of KONNI’s latest attack took place right after the North Korean government tested an Intercontinental Ballistic Missile (IBM) capable of reaching the United States.
What do you think about the new KONNI malware? Let us know in the comments below. Also, don’t forget to follow us on Facebook and Twitter. Thanks!