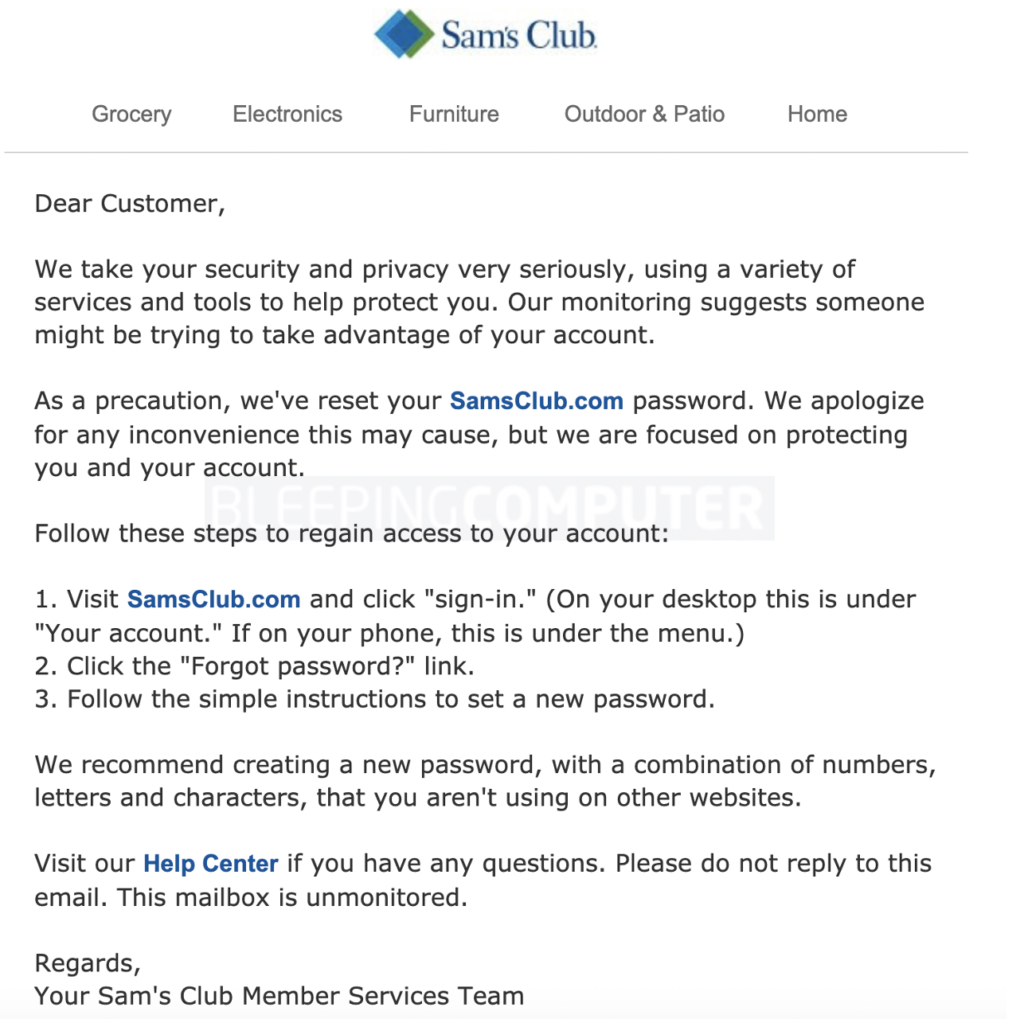
‘Sam’s Club’ Accounts Targeted by Credential Stuffing Actors
- ‘Sam’s Club’ has been dealing with a wave of account takeover attacks for two weeks now.
- The platform has managed to thwart most of them while sending password reset emails to the owners.
- The firm assured its members that there was no security breach, so this must be credential stuffing.
Members of the Walmart-owned retail chain ‘Sam’s Club’ are reporting account hacks, while the platform itself has been sending out automated password reset emails and security notifications over the past two weeks.
Sam’s Club is a membership-only wholesale retail store that operates six hundred locations in the United States, and several warehouses in Mexico, China, and Brazil. Members of the chain need to provide a valid payment method (credit or debit card), a shipping address, and of course, an email address and a password to secure their account.
The ongoing wave of account takeover attacks that has been plaguing Sam’s Club members since last month is most likely the result of credential stuffing attacks. That would be email addresses paired with passwords found in data breaches or stolen from other online platforms.
Related: New Ransomware Campaign Targets Teachers Working Remotely
The victims are most likely using the same password across multiple websites and services, although this hasn’t been confirmed. Thus, there’s still a possibility that this is the result of a phishing campaign that targeted Sam’s Club members specifically.
From their side, Sam’s Club assured the public that there had been no breaches on their systems, and so this is not their fault. Additionally, the company is engaging in proactive password resetting for the accounts where they detect suspicious activity, like access events from new computers or user fingerprint mismatch. This is very positive from the firm’s point, as they may have actually saved quite a lot of accounts from being stolen by hackers.
If you have received a message that looks like the above, make sure that you visit the official website to perform the reset as described in the instructions. We’re only clarifying this detail because malicious actors are known to quickly exploit security events, sending fake reset requests to people, urging them to enter new credentials on a phishing page. These may then be used in new stuffing attacks on platforms where the same email addresses appear.
As for the passwords you should be using on these platforms, there is no exception to always picking a unique, strong, lengthy, and diverse password. Alternatively, set a long, non-sense passphrase. If you are using the same password elsewhere, go ahead and reset it there too, no matter if your account was taken over on Sam’s Club or if the company stopped that action.