Researcher Discovers Major Exposure in the EventBuilder App
- A researcher has discovered an EventBuilder app exposure through a public Azure Blob.
- The data includes full names, email addresses, phone numbers, and answers to questionnaires.
- The mistake could have been avoided easily, but the owners of the data didn’t realize the mixup.
Bob Diachenko has partnered with Clario to uncover a massive exposure in the EventBuilder app, a platform that offers unification and integration potential for various Microsoft products (Teams, Skype, Azure) for the organization of online webinars. In this case, the exposure comes from Microsoft Azure Blob cloud storage instances that contained thousands of CSV/JSON files with details on the webinar registrants.
The data was discovered by using the ‘Grayhat Warfare’ specialized search engine on June 10, 2021, was reported to the EventBuilder team on the same day, and was subsequently addressed.
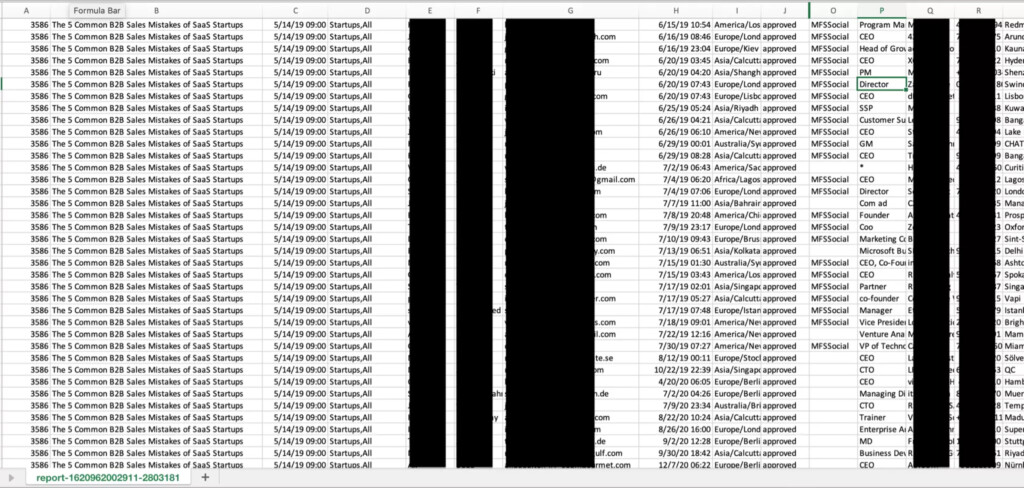
The data that has been exposed includes the following things:
- Full names
- Email addresses
- Company names and position in the company
- Phone numbers
- Questionnaires answered
There is no exact number for the leaked records, but the researcher believes it should be in the hundreds of thousands, based on the file sizes. Here are some samples from the CSV/JSON files that Diachenko and the Clario team accessed during their “expedition.”
Some of the above can be used by hackers for a wide range of malicious purposes, and possibly, they have already been abused. The exposure period is unknown, but these instances were indexed by specialized search engines, so finding them should be a matter of time.
We chatted with Bob Diachenko about this possibility, and the researcher told us that the indexing happened four days before his discovery. It's very likely that the blob was accessible for weeks, possibly even months.
Vectra’s CTO, Oliver Tavakoli, commented for TechNadu:
Indeed, the leaked data was meant to be stored in a partially public space, hosting recorded sessions for link-only access. The mistake was that the organizers of the exposed webinar were putting registrant information into the public blob, which could have easily been avoiding as anyone realizes this is private, sensitive data. The organizers should either have implemented proper access rules and only allow authorized personnel to access that information or not make the system public in the first place.