How Long Does It Take for Actors to Find an Unsecured Database?
- How many times per day do hackers access unprotected databases, and how long does it take them to be discovered?
- Researchers have set up a honeypot that answers the above questions and provides more details like what the actors are trying to do.
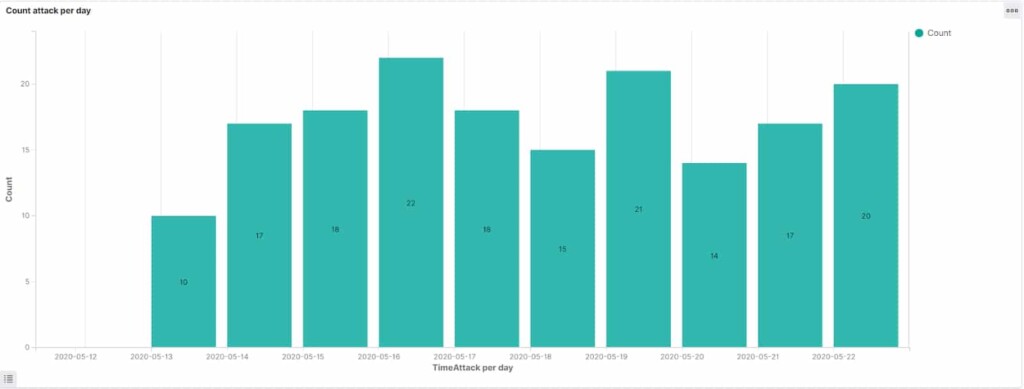
- The honeypot was accessed by 175 people in 11 days, averaging 18 times per day and reaching a max of 22.
Security researchers conduct interesting experiments every once in a while that provide useful insight around a disputed matter. The topic of unprotected databases occupies sections on infosec news websites on a daily basis. Very often, we are bound to reproduce contestable beliefs like that of hackers who do not have enough time to access an unsecured instance. The research team of Comparitech has set up an unprotected database honeypot to see how quickly it would get detected by malicious actors and how many would access it in a day.
So, Bob Diachenko and his team set up a simulated Elasticsearch instance and populated it with fake user data on May 11, 2020. After just eight hours, the first attack was underway. Two actors accessed it just one minute after Shodan indexed the instance on May 16, 2020. Then, on May 21, 2020, the indexing from BinaryEdge came, and the attacks reached a peak of 22 within a single day. In total, during the first eleven days that the database was freely accessible online, 175 unauthorized requests were made, which gives us an average of 18 attacks per day.
Source: Comparitech Blog
Of course, some of these requests may have been well-intended, launched by security researchers who are on the lookout for misconfigurations. On May 29, 2020, a malicious bot discovered the honeypot and wiped the contained data while requesting the payment of 0.06 BTC to provide a backup to the owner. This event concluded the experiment in a definitive manner, although the researchers had stopped tracking the attacks days before. Of the 175 access requests, 89 came from the USA, 38 from Romania, and 15 from China. The final blow, though, came from the Netherlands.
As for what the actors attempted to do against the honeypot, some tried to install a cryptomining script by using a known RCE vulnerability (CVE-2015-1427), others ventured to download the data via path traversal attacks (CVE-2015-5531), and one attempted to modify the server configuration to turn off the server’s firewall.
So, there you have it. If you were wondering how long it takes for an unprotected database to be accessed by someone, the answer would be “about eight hours.” As for how many will access it, that would be about 18 people (and bots) per day. Finally, the server's data is unlikely to survive wiping bots for longer than a couple of weeks. In conclusion, the experiment proves that having data online for two, three, or four days and hoping that no one accessed it is entirely illusory.