RCE Bugs in ‘SHAREit’ App Put 1 Billion Users at Risk of Exploitation
- SHAREit is vulnerable to several RCEs and information disclosure flaws, but the developer isn’t fixing them.
- Researchers have created and publicly shared the proof of concept, so using the app is no longer safe.
- Google hasn’t removed SHAREit from the Play Store yet, as this is one of the most successful tools in the platform.
The ‘SHAREit’ app, which counts over one billion installations on the Google Play Store, is reportedly plagued by a host of RCE (remote code execution) bugs that could be abused by malicious actors to exfiltrate sensitive user data or to execute arbitrary code. The report comes from mobile threat researchers Echo Duan and Jesse Chan, who work at Trend Micro.
The discovered vulnerabilities have already been reported to the vendor. However, the developer has failed to respond even after three months have passed, so the case is now released to the public.
SHAREit is an app that allows users to share files with amazing transfer speed and free of platform-specific limitations. Also, the app features a powerful media player so that users can enjoy videos, movies, music, and pictures right from inside the app. People find it so convenient that it was among the top ten most downloaded mobile apps in 2019.
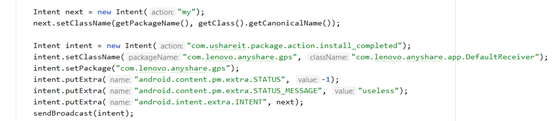
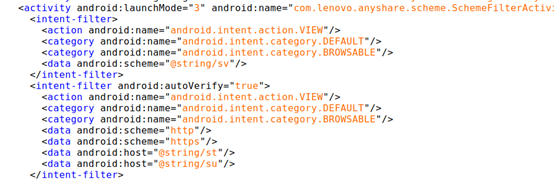
According to the report from the Trend Micro researchers, there’s a way to make any app invoke the broadcast receiver component of SHAREit, essentially tricking the vulnerable app into revealing internal and external activities that should remain hidden at all times. Furthermore, due to an attribute misconfiguration in the “FileProvider” component of the app, any third-party entity can gain temporary read/write access to the data that stems from the content provider. This includes files lying in the data/data/ folder.
The researchers developed a PoC (proof of concept), and they are now sharing it, so if you’re a user of SHAREit, you may want to take several security precautions now. In addition to the above, SHAREit is also vulnerable to crafted vdex/odex files that can potentially lead to code execution events and also has an exploitable link-installation feature that can be abused for installing malware on the target or for limited RCE.
Further digging uncovered that the app itself is following unsafe practices - like fetching APK files via URLs that use the HTTP protocol and also sources that are outside the Google Play Store. This also opens the door to “man-in-the-middle” attacks. In summary, the SHAREit app appears to be vulnerable to multiple flaws, most of which are hard to detect or realize for the victims.
We would suggest either uninstalling SHAREit or keeping it alongside a powerful mobile security solution. Also, Google has received Trend Micro’s reports. Still, the software remains available on the Play Store, probably because just ousting it even temporarily is not the tech giant’s first option when dealing with such popular projects.