PyPI Attack: Fake ChatGPT & Claude API Delivers JarkaStealer Malware
- Security researchers found malicious packages for AI integration containing infostealer malware in the Python Package Index repository.
- Cybercriminals impersonate ChatGPT and Claude to deploy PyPI attacks that distribute the JarkaStealer malware.
- The infostealer collects web browser data, system information, screenshots, and session tokens for Telegram, Discord, and Steam.
Python developers have been targeted by a new wave of cyber threats that are exploiting the Python Package Index (PyPI) repository. Threat actors are impersonating popular AI tools like ChatGPT and Claude to distribute malicious Python libraries embedding the JarkaStealer malware, according to the latest Kaspersky report.
JarkaStealer serves as a dangerous information-stealing malware targeting web browser data (e.g., saved passwords, cookies, and browsing history), system information (e.g., OS details and hostnames), screenshots, and session tokens for popular applications such as Telegram, Discord, and Steam.
Cybersecurity researchers have uncovered a significant software supply chain attack involving the Python Package Index (PyPI) repository. Malicious packages mimicking widely recognized artificial intelligence (AI) models, OpenAI's ChatGPT, and Anthropic's Claude were used to distribute a sophisticated malware known as JarkaStealer.
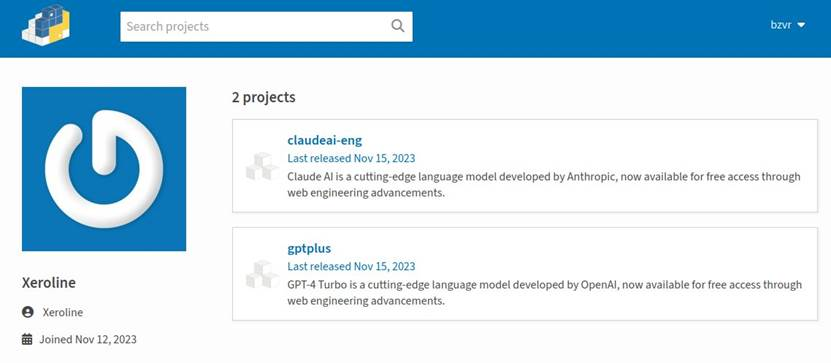
The two rogue libraries, named gptplus and claudeai-eng, were uploaded under the alias "Xeroline" in November 2023. These packages, designed to impersonate the GPT-4 Turbo API and Claude AI API, collectively amassed over 3,500 downloads before being removed from PyPI. While their names and descriptions differed, both packages contained the same malicious payload.
The attack used Base64-encoded data in the “init.py” file. Upon installation, this code downloaded the JarkaStealer malware hosted on a GitHub repository and a Java Runtime Environment (JRE) from Dropbox if Java was not already installed on the machine. The malware, packaged as "JavaUpdater.jar," was then executed.
Once the sensitive data is collected, JarkaStealer compresses the files, transfers them to the attacker's server, and deletes them from the victim's device to minimize detection.
Notably, the malware operates under a Malware-as-a-Service (MaaS) model available via Telegram channels, with prices ranging from $20 to $50. Compounding the threat, its leaked source code on GitHub may allow other malicious actors to perpetuate further attacks.
Download statistics indicate victims spanned geographically diverse regions, including the United States, China, India, France, Germany, and Russia. This highlights the global scale of the PyPI supply chain attack campaign, which has been ongoing for over a year.
"This discovery underscores the persistent risks of software supply chain attacks and highlights the critical need for vigilance when integrating open-source components into development processes," said Kaspersky researcher Leonid Bezvershenko.
In August, a malicious campaign involving several Python packages deploying malware that stole sensitive data and emptied crypto wallets was observed targeting mainly Radyum and Solana users.