Crypto-Stealing Python Pack Targeting Raydium and Solana Users Distributed via StackExchange
- Python packages that stole data and crypto from compromised systems targeted Raydium and Solana users.
- Multiple versions able to evade detection were installed together with a backdoor.
- The attacker leveraged the trust of StackExchange users to direct them to the multi-stage malware.
A malicious campaign involving several Python packages deploying malware that stole sensitive data and emptied crypto wallets was observed targeting mainly Radyum and Solana users, a report from Checkmarx says.
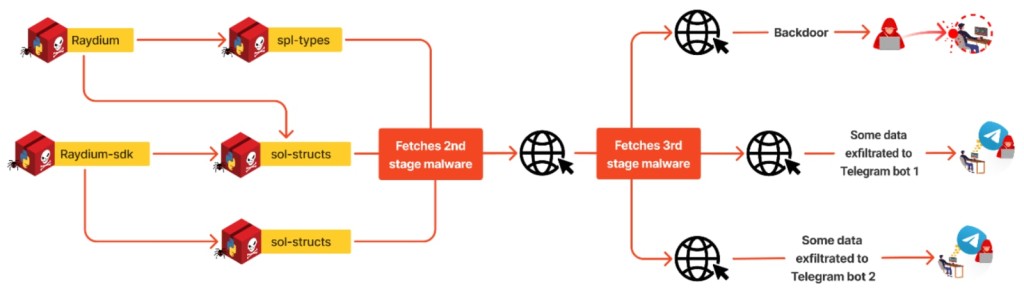
The attacker tricked the users of the Q&A site StackExchange by pretending to offer a useful answer to a thread, which included references to their malicious Python package they called ‘Raydium’ that contained a multi-stage malware with a backdoor component.
The campaign debuted on June 25 with a benign version uploaded to PyPI and deployed multiple malicious versions of the “spl-types” Python package on July 3, targeting cryptocurrency users involved with Raydium and Solana.
The legitimate blockchain-related platform Raydium is an Automated Market Maker (AMM) and liquidity provider built on the Solana blockchain for the Serum Decentralized Exchange (DEX). It does not have an official Python library.
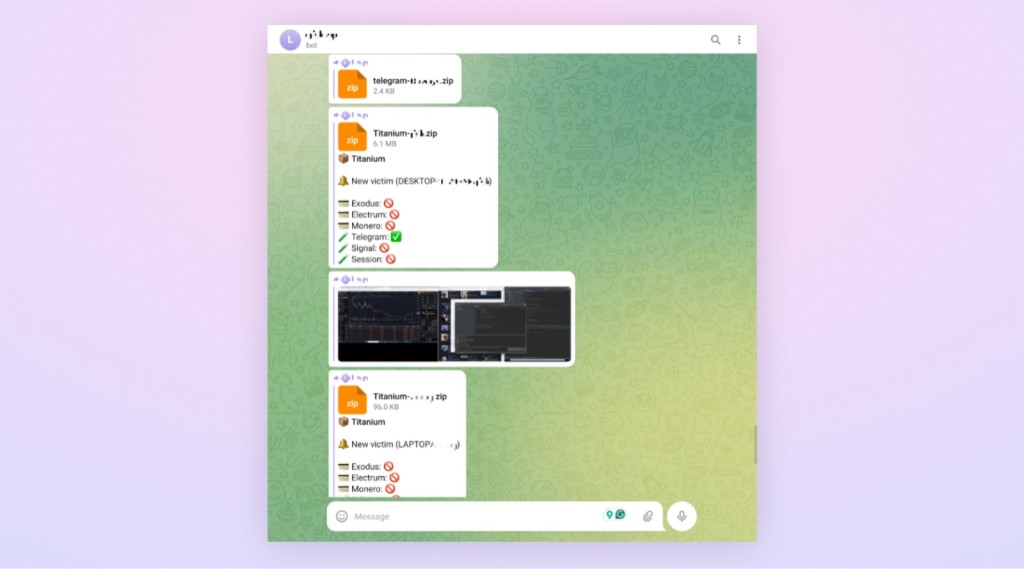
The initial payload downloaded and executed additional scripts from external resources. These scanned the victim’s system for sensitive information, which was then compressed and sent to the attacker’s command and control (C2) server via several Telegram bots.
The init.py file, obfuscated to evade casual inspection, would execute automatically upon installation while also exfiltrating extensive sensitive data and draining crypto wallets.
The attacker stole browser data such as saved credit card information and passwords, cookies, and browsing history and data from messaging applications such as Telegram, Signal, and Session, capturing screenshots of the user’s activities on the system.
The malware also targeted Exodus, Electrum, and Monero wallets, focusing on files containing specific keywords related to cryptocurrencies and other sensitive information, including GitHub recovery codes and BitLocker keys.
Windows Virus and Threat Protection failed to detect the active malware on a victim’s system. A backdoor component in the malware granted the attacker persistent remote access to victims’ systems.
Recently, hackers were seen increasingly exploiting YouTube channels for crypto scams and deploying info-stealers like Vidar via fake tutorials about popular software like After Effects, ads for crypto giveaways, and more.