Previously Unknown Lazarus Backdoor ‘Vyveva’ Spotted in the Wild
- Researchers managed to sample and analyze a previously undocumented backdoor linked to Lazarus.
- The North Korean APT group has been deploying this malware since at least 2018, but it was detected only recently.
- The backdoor is powerful, supports up to 23 commands, and gives actors several configuration options.
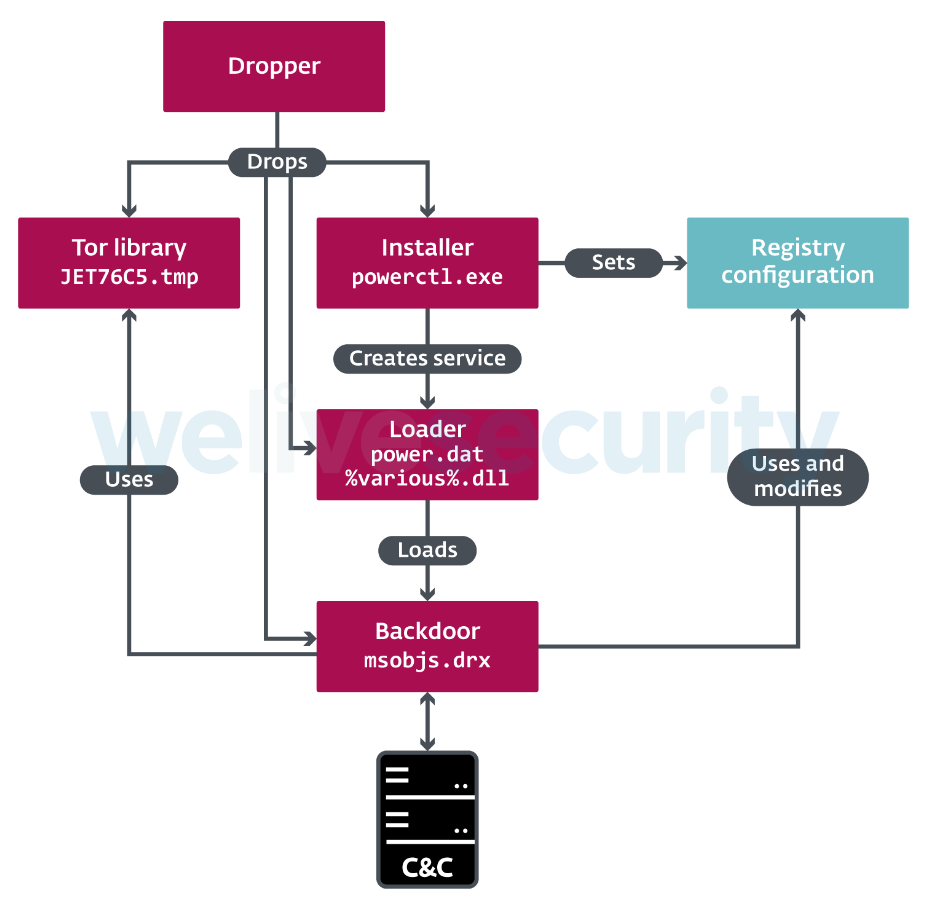
It looks like the North Korean group of actors known as ‘Lazarus’ wasn’t careful enough during their recent operation targeting a freight logistics company in South Africa, as security researchers managed to sample a previously undocumented backdoor used by the hackers. Dubbed ‘Vyveva’ by the ESET team that discovered it, this is a backdoor that has been deployed since at least December 2018, and it still doesn’t have a known initial compromise vector.
The reason why ESET believes that Vyveva is a Lazarus tool is that it has several code similarities to the NukeSped malware, a Mac-specialized backdoor that was predominately used against Korean users. The similarities extend in the code, the use of fake TLS network communication, the command line execution chains, and also the use of encryption and Tor services. All in all, there are several Lazarus hallmarks, so the attribution is pretty confident.
The Vyveva backdoor functionality goes deep and wide, featuring 23 commands, some of which supporting individualized thread execution. The commands are focused on reconnaissance and cyber-espionage, but there are also some “hands-on” tools in there to allow remote file write, copy, creation, and deletion operations. For a full list of all the supported commands, check out ESET’s detailed write-up.
The backdoor also features a switchable watchdog that can monitor for newly connected or disconnected drives and also one other watchdog monitoring user logins and status. While the backdoor connects to the C2 server in fixed intervals of three minutes, these watchdogs can trigger an “out-of-band” connection if something interesting occurs.
Whenever Vyveva needs to send a pack of data back to its masters, it compresses it first using zlib and then encrypts the traffic using XOR and Tor. Other detection evasion techniques include encrypting all strings and components, storing the configuration file in the registry, and creating services that mimick existing processes instead of random stuff.
The existence of Vyveva is yet another example that underlines Lazarus's expertise in creating powerful custom backdoors. The fact that they’ve managed to keep it undetected for over two years is also indicative of their skills. And finally, the reach of the particular APT group never fails to impress, as not even companies in South Africa can consider themselves safe from the North Korean actors.