Lazarus Using a New Mac Backdoor to Target Korean Users
- Researchers discover a new backdoor sample that is deployed by the notorious North Korean hackers.
- The backdoor targets high-profile Mac users and can steal various forms of data from the host.
- Lazarus continues to be very active, pushing more sophisticated tools in the wild and targeting mainly Korean users.
According to a report by Trend Micro, the notorious North Korean group of hackers “Lazarus” is using a new Mac backdoor (Nukesped) against Korean users. The cybercriminal group is deploying infected Microsoft Excel documents to push the backdoor to their targets. The element that gave away the origin of the particular backdoor is the similarity of the macro that is used in the malicious document with a previous sample that can be confidently connected to the Lazarus group.
The content of the Excel file concerns a psychological test that involves various questions for the recipient. The file is asking for the activation of the macros in the victim’s office suite, supposedly to make it possible for its integrated algorithms to run as required and calculate the complex results of the test. If the recipient is convinced and falls for it, the macro will run a PowerShell script that connects to three individual C&C servers that belong to the Lazarus infrastructure.
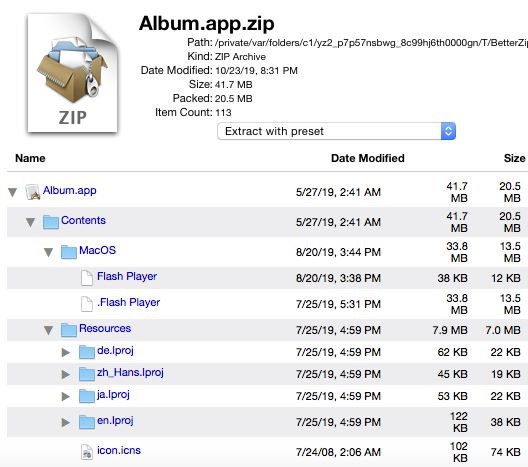
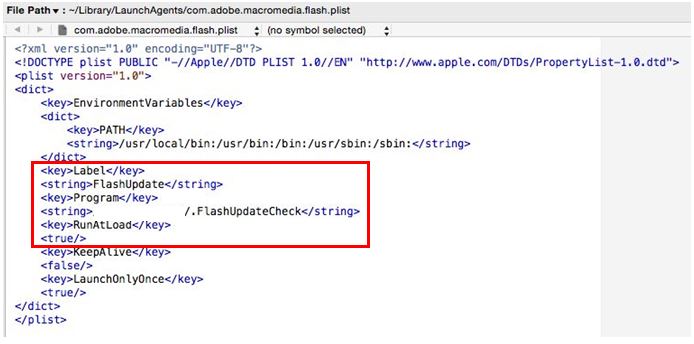
Apart from this sample, the team analyzed another one that is basically a Mac app bundle containing two Flash Player packages, a real one, and a decoy. When the user attempts to execute either, the legitimate installer is launched while the malicious executable runs in the background and creates the same backdoor as the one that is planted by the Excel document. The actors have also managed to incorporate a persistence mechanism, installing it on “~/Library/Launchagents/com.adobe.macromedia.plist”.
Source: Trend Micro
So, what does this “Nukesped” backdoor do? It can retrieve information about the host, check the backdoor configuration, update C2 and backdoor configuration, terminate processes, set sleep, upload or download a file, and execute shell commands. This opens up great infiltration and exploitation potential for the Lazarus group, who are mainly targeting high-profile individuals and not just any Mac user out there.
Source: Trend Micro
Remember, Lazarus is believed to be state-supported, helping in the funding of the North Korean nuclear weapons program by stealing money and information from key organizations. The United States has already imposed sanctions against the group, as they are confident about their ties with North Korea’s intelligence agency. In January, we covered a story involving the Lazarus group with the compromising of Chilean ATMs by malware. Then again in September, they were accused of doing something similar against various financial institutions in India. All that said, Lazarus is a very active actor who will continue to strengthen and perfect their exploitation methods in the future.
Do you have anything to comment on the above? Feel free to share your thoughts with us in the section down below, or on our socials, on Facebook and Twitter.