Popular Turkish Software Site ‘Gezginler’ Appears to Have Been Breached
- A hacker is selling two pretty voluminous user databases belonging to two Turkish sites.
- Neither site has confirmed a data breach, but they both appear to be somewhat outdated.
- The data that is for sale includes email addresses, weakly encrypted passwords, and physical addresses.
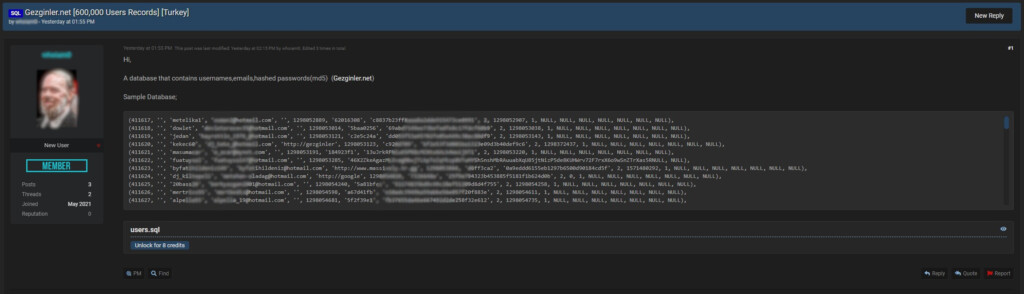
Someone is selling a database containing 600,000 user records that allegedly belong to ‘Gezginler.net’. The records contain usernames, email addresses, and hashed passwords (md5), and the seller is also offering a sample as proof of the database extraction. MD5 is a cryptographic hash function that is nowadays considered insecure, so if you have an account on Gezginler, or if you may be using the same credentials on another website, go ahead and reset your password as soon as possible.
Gezginler, a software download, and online flash games portal, doesn’t appear to be facing any issues. Moreover, they haven’t posted anything about a data breach on their social media channels. As such, we cannot confirm that the data which has appeared on the popular hacking forum does indeed come from Gezginler. We have reached out to the platform, and we will update this post as soon as we hear back.
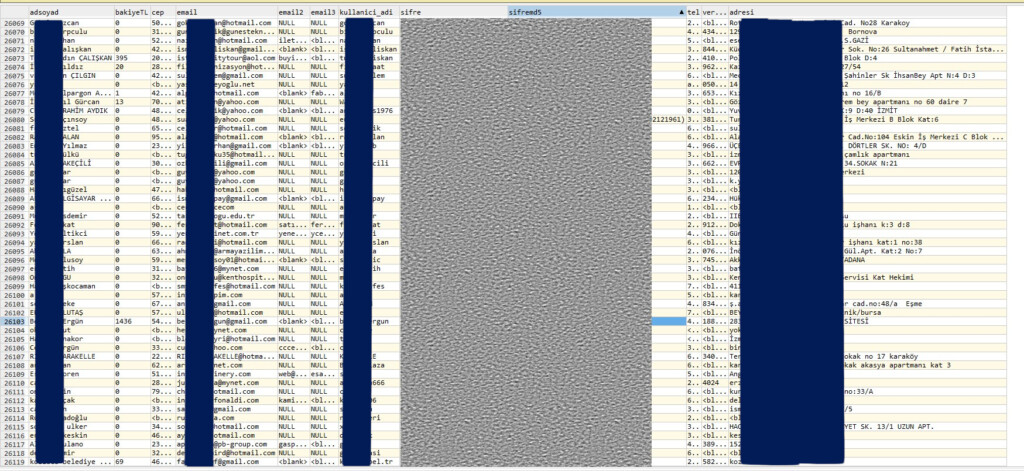
The same forum user who is selling the Gezginler data has also posted another pack of data containing 92,999 user records that are, again, allegedly the result of a database extraction. The victim, in this case, is ‘websahibi.com’, another Turkish site belonging to a hosting and domain services company. The sample screenshot provided as proof shows full names, email addresses, cleartext passwords, telephone numbers, and physical addresses.
Clearly, this particular seller is focused on Turkish platforms, so we may see more databases from websites operating in the country appearing online soon. In the case of Websahibi, we have no confirmation from the company yet, so a data breach hasn’t been verified here either.
SQL database extraction incidents usually rely on the exploitation of an unpatched bug that allows back-end access. Using SQL injection to dump complete databases is a typical approach. Enumeration and extraction actions should be detected and stopped by security tools, but this is not always the case. The two Turkish websites that we see in these listings appear to be outdated, at least in terms of their user interface, so we wouldn’t be surprised if their security isn’t up to par.