Hacker Stealing SQL Databases to Extort Online Shop Owners
- There’s a wave of SQL database encryption, stealing, and extortion that is targeting e-commerce websites.
- Actors are requesting about five hundred dollars in ten days, or else they publish the data online.
- The threat actors are possibly selling these databases to others on the dark web, maximizing their profits.
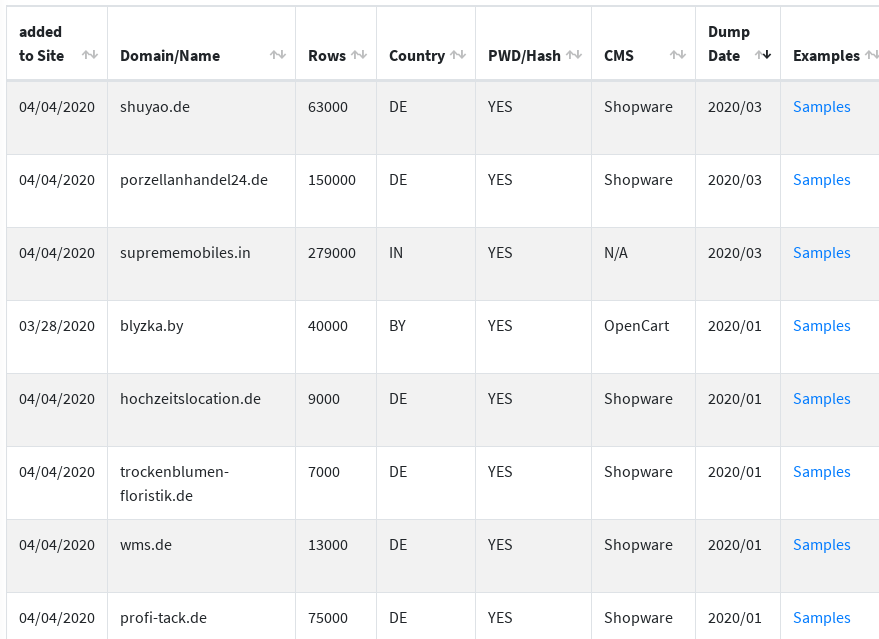
A hacker has stolen at least 31 SQL databases containing 1,620,000 rows of information relating to the customers of online shops. Depending on the store, the rows may reveal full names, usernames, email addresses, MD5 hashed passwords, dates of birth, physical addresses, gender, account status, history, and more. The threat actor is offering samples of the data from each of the extorted e-commerce websites to prove the validity of the data and ramp up the pressure that is exerted on the database owners. As reflected in the below screenshot, most of the databases belong to German online ships, but the hacker sells data from all over the world.
Source: Bleeping Computer
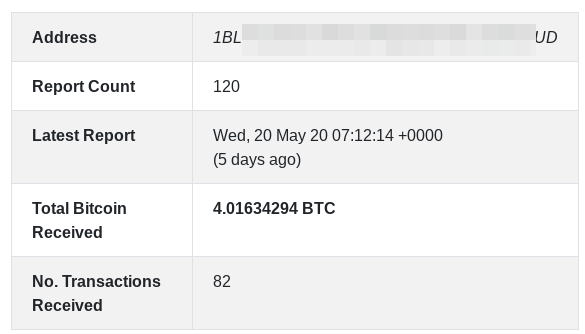
If the owners of the compromised e-commerce website want to recover the database (which is encrypted as a result of the attack) and also to avoid having its contents leaked online, they are prompted to pay 0.06 BTC ($534) to the actor’s address within ten days from the security breach and the planting of the notification message. The actor has already received a total of 5.8 BTC ($51,620), which corresponds to about 97 transactions. At least this is the amount revealed from the wallets that are known to belong to the actor. The most recent payment occurred last week, so the actor is still actively extorting e-commerce websites.
Source: Bleeping Computer
Security experts believe that the hacker is simply taking advantage of unsecured servers that are indexed by specialized search engines and are accessible without needing a password. This is something that we have been seeing for quite a long time now, and it continues to be a thing well into 2020. The compromised stores use various e-commerce platforms (Shopware, JTL-Shop, PrestaShop, OpenCart, Magento v1, and v2), so the attacks can’t be the result of exploiting a vulnerability on a particular platform.
These attacks were very popular back in 2017, but security researchers have noticed a resurge since the beginning of this year. Potentially, hackers are targeting e-commerce websites because of the wave of new businesses hopping onto online platforms for the first time, as a response to the closure of the physical shops that was brought by the COVID-19 situation. Possibly, the crooks are maximizing their profits by selling the stolen data to other actors anyway, no matter if the victim pays the ransom or not. This leaves the regular customers/users in the worst possible position, as always.