Perilous Disk Image Files Arrive on Your Email Inbox and Plant Malware
- Actors are increasingly relying on the use of malicious image files because they are easy to work with.
- These files can be auto-mounted by Windows, run scripts, and plant powerful RAT tools on newly allocated memory.
- Users are advised to refrain from downloading torrent cracks or opening email attachments that come out of nowhere.
Researchers at CrowdStrike have noticed and recorded the rise of a special type of a phishing campaign that has been active throughout 2019 and entered 2020 with impetus. Cybercriminals have figured that utilizing disk image files like “.ISO” and “.IMG” is a very effective method of dropping RATs (remote access Trojans) and malware in general. This is because Windows is offering to load these files and mount them as virtual disks automatically, so the compromising process gets simpler and more “user-friendly,” if you like.
Source: CrowdStrike Blog
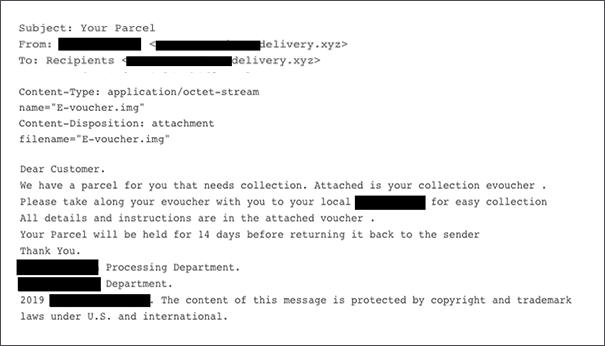
It all starts with social engineering as usual, so the victim receives an email that supposedly concerns the delivery of a post item to them. The attachment that comes with the phishing mail is a small disk image file, typically around 2MB. Watchful users would normally query why such a small file needs to be bundled as a disk image, as these files are usually in the range of several hundreds of MBs and even a few GBs. The suspicion should grow even more when mounting the image that follows the double-clicking of the file unveils an “e-Voucher” that ends with the “.exe” filename extension, although the icon is a “PDF” type.
Source: CrowdStrike Blog
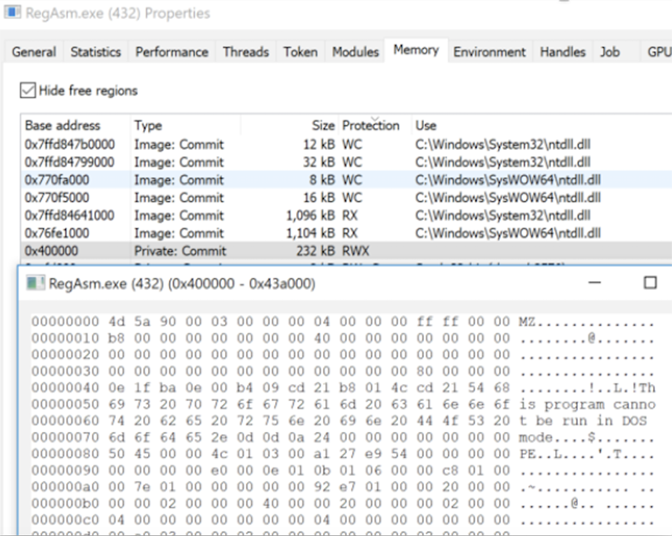
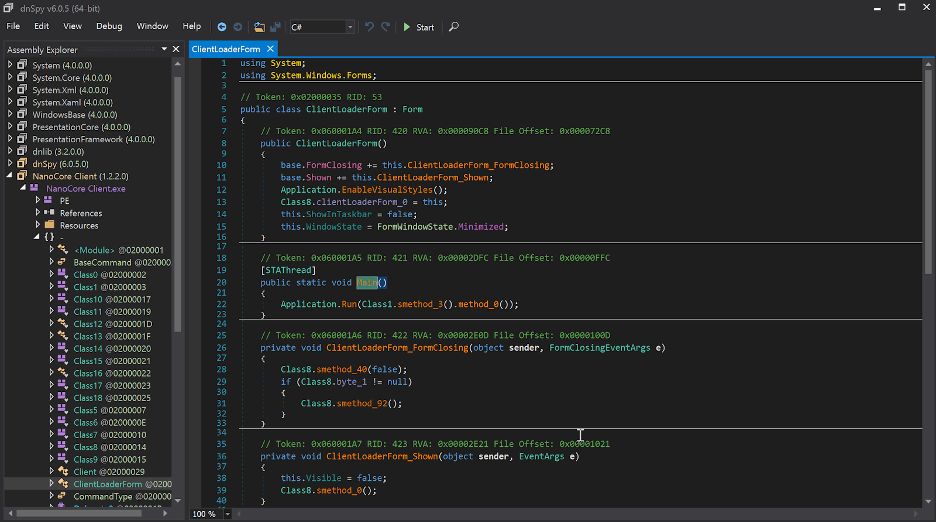
If the voucher file is opened, a set of malicious scripts that automate Windows GUI tasks are run, eventually loading the NanoCore RAT, or the Warzone RAT, or AgentTesla, or AZORult. The CrowdStrike team has noticed an AutoIT script that is obfuscated, and which uses three individual resources after decrypting them with “CryptDeriveKey.” Next, the script is allocating enough memory space for the dropping of the decrypted payload, and then writes it in the region through “WriteProcessMemory.” The malware is eventually dropped to “C:\Users\username\PasswordOnWakeSettingFlyout\DataExchangeHost.exe,” while its persistence is created by planting a URL shortcut in the Windows StartUp folder.
Source: CrowdStrike Blog
If you have stepped on this trap, unmount the malicious virtual drive from your system immediately, run a registry cleaner tool, and remove the payload from the directory mentioned above. Also, go to Windows Settings, choose Apps, and then search for the StartUp list. There, locate the malicious URL entry and disable it. In about 70% of the cases, these image files reach you through phishing emails, but in 30% of the time, they are hiding inside cracks downloaded from torrent websites. Also, there can be different phishing messages and themes, so treat everything with care.