When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
AZORult Poses as a ProtonVPN Installer and Spreads via Malvertising
- A fake ProtonVPN website is spreading the AZORult trojan on unsuspecting victims.
- The malware is capable of stealing login credentials and crypto coins from locally stored wallets.
- Malvertisers often use a "356-day free VPN" offer as bait, as the demand for this software is on the rise.
Another case of a fake VPN installer sees the light thanks to a report by Kaspersky. This time it involves the AZORult Trojan, which poses as ProtonVPN. AZORult is a powerful stealer that can exfiltrate login credentials, browsing cookies, files from local disks, browser history, and crypto-wallet files. Malicious actors love it for being versatile (it can download additional payloads), cheap (it only costs $100), and for having RAT (remote access) capabilities too. This is why they have been using it in malvertising campaigns for quite a long time now.
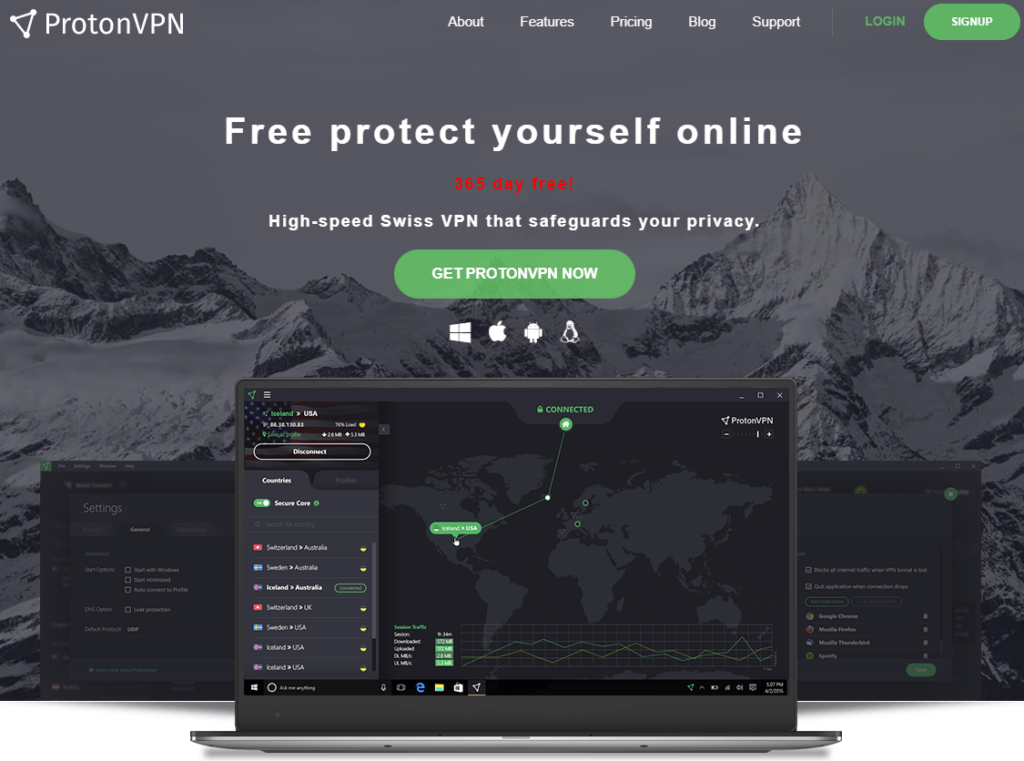
The latest campaign is launched from the ‘protonvpn[.]store’ domain (online at the time of writing), which looks a lot like the real ProtonVPN website, but with the difference of having a message that reads "365 day free!". For those of you who are wondering if that could be a legitimate offer, we assure you that there are no commercial VPN products that have ever given such an extensive trial period. Thus, whenever you happen to stumble upon such a tempting offer, especially one of this magnitude, you may as well pass it without a second thought. If it is too good to be true, sometimes it's best to trust your instinct.
Spoofed ProtonVPN domain
Those who have downloaded the fake ProtonVPN installer got an AZORult botnet implant, which immediately scans the infected system and sends the machine information to the C2 server (‘accounts[.]protonvpn[.]store server’). The next step is stealing data. This involves cookies, email credentials, FileZilla FTP logins and passwords, and also cryptos such as Electrum, Etherium, and Bitcoin that may be stored on local wallets. Even credentials from WinSCP and communication from the Pidgin open-source messaging app are exfiltrated to the actors. Kaspersky has managed to collect the following seven samples of the malware, and you can see their hashes below.
Source: SecureList
As the VPN market grows bigger, malicious actors will continue to target gullible users with fake offers. Back in May 2019, scammers set up a website of a fake VPN product named Pirate Chick, which propagated AZORult as well. That campaign offered three months of free VPN services with no credit card registration required. A little bit later, in August 2019, a fake NordVPN website appeared online featuring a legit-looking domain and a valid SSL certificate. Again, the decoy site lured the visitors flashing a full year of free VPN services, but in reality, all that was on offer was the “Win32.Bolic.2” banking trojan.
That said, if you’re looking for a VPN, it's best you find its real website via a search engine and only download its installer from the official domain.