The “Palmerworm” Group Has Been Targeting Taiwanese Firms Since Last Summer
- A sophisticated group of hackers has maintained a presence in Taiwanese corporate networks for months.
- The particular actors are using custom backdoors and legit tools maliciously, following living-off-the-land methods.
- Palmerworm could be Chinese and state-supported, but there can be no certain and definitive accusations on that part yet.
“Palmerworm,” also known as “BlackTech,” have been engaging in cyber-espionage since August 2019, using a combination of novel malware tools and standard living-off-the-land methods. According to a detailed report published by Symantec’s Threat Hunter Team, the particular group of actors was interested in compromising financial and media companies in Japan, China, Taiwan, and the United States.
Palmerworm has been around since 2013, so seeing them use custom malware isn’t a surprise. This is a sophisticated, experienced, and capable actor, yet Symantec managed to collect the crumbs left behind. The tools used by Palmerworm in the most recent campaign are backdoors named “Consock,” “Waship,” “Dalwit,” and “Nomri,” all different from samples collected in the past like “Kivars” and “Pled.”
Moreover, the group is using several legitimate tools and utilities like “Putty” (remote access tool), “PSExec” (lateral movement), “SNScan” (network scanning), and “WinRAR” (archiving and file compression). APT groups can take tools like these and utilize them maliciously, which constitutes an integral part of the living-off-the-land approach.
For signing their payloads, Palmerworm uses stolen code-signing certificates, so everything appears legitimate and is unlikely to raise security flags. This is something that this particular group of actors is known for doing from past attacks. Another well-documented activity of BlackTech that also appears in the most recent campaign is to spear-phish the target companies’ employees to gain access to their corporate networks.
The thing that gave away Palmerworm and enabled Symantec to derive a confident attribution is the use of infrastructure that has been previously linked with the group. As for where the group is based and who backs them, this still is a question. Taiwanese officials have recently stated that the Chinese government backs BlackTech and that they are one of the two groups attempting to penetrate the country’s crucial industrial and core administrative organizations.
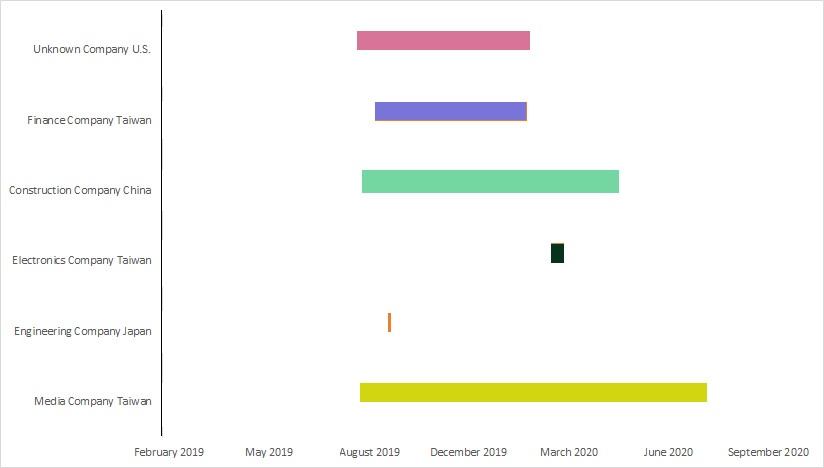
In the recently recorded campaign, the two main targets from Taiwan were a media company and a finance firm. The former remained compromised for more than a full year, while the latter had Palmerworm movement in its network for a couple of months. The third target from Taiwan was an electronics company that was briefly spied upon by the hackers in March 2020.
Source: Symantec
Besides Taiwan, BlackTech maintained a lengthy presence on the networks of a construction company in China and also an unknown company in the United States. An engineering firm in Japan was also fleetingly penetrated.