“Oski Stealer” Is a Widely-Used Cheap Yet Powerful Malware
- The “Oski Stealer” is getting more popular, as it’s a bargain for what it can do.
- The malware appears to be of Russian origin, and it’s mainly used by actors of the associated countries.
- Oski can steal sensitive information and credentials from over 60 different applications.
There’s a piece of malware that has created some frenzy on the Russian parts of the dark web named “Oski Stealer.” The credential-stealing malware first appeared in November 2019, so it’s not exactly new, but its continual development and low price have placed it very high in popularity. More specifically, it goes for sale between $70 and $100 and offers a galore of info-stealing capabilities to its masters.
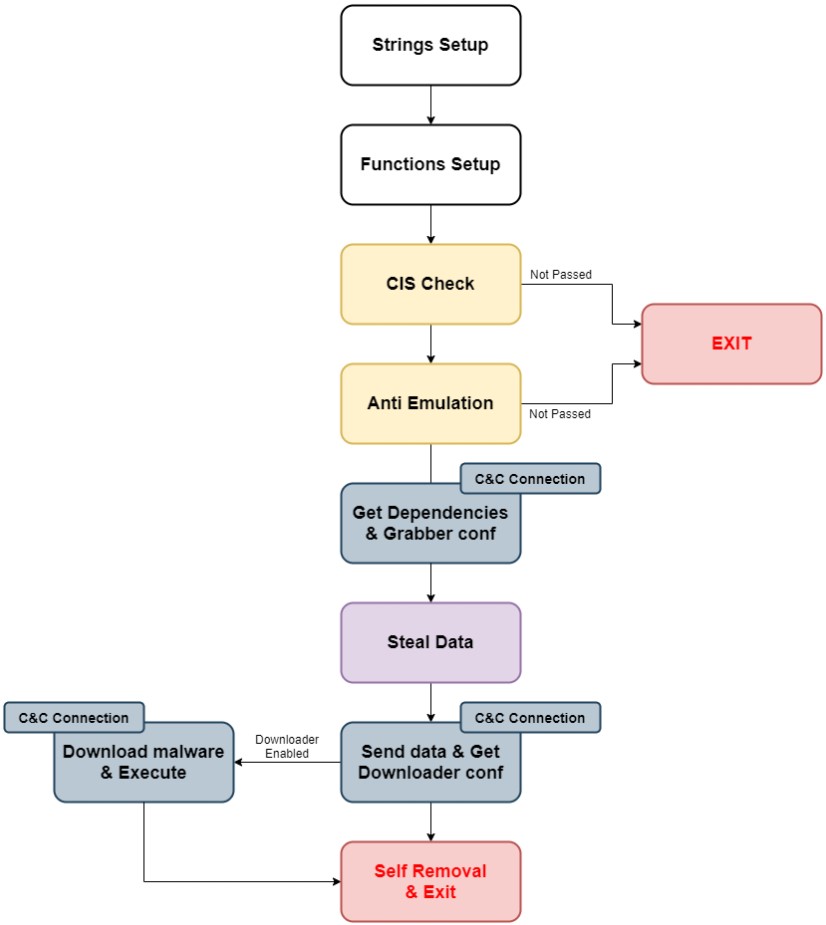
Researchers at ‘CyberArk’ have analyzed the latest malware samples they could get their hands on and report on the full list of Oski’s capabilities. Written in C++, the malware can steal the following things:
- Login credentials from different applications
- Browser information (cookies, autofill data, and credit cards)
- Crypto wallets
- System information
- Capture Screenshots
- Different user files
The code of the malware is clean and indicates that the author is knowledgeable, ensuring reliable operation. However, Oski doesn’t have any sophisticated obfuscation, anti-analysis, or anti-debugging tricks under its sleeve yet, but this can always be added later. The fact that the code basis is neatly done creates the setting to work on this tool further and add more features in the future.
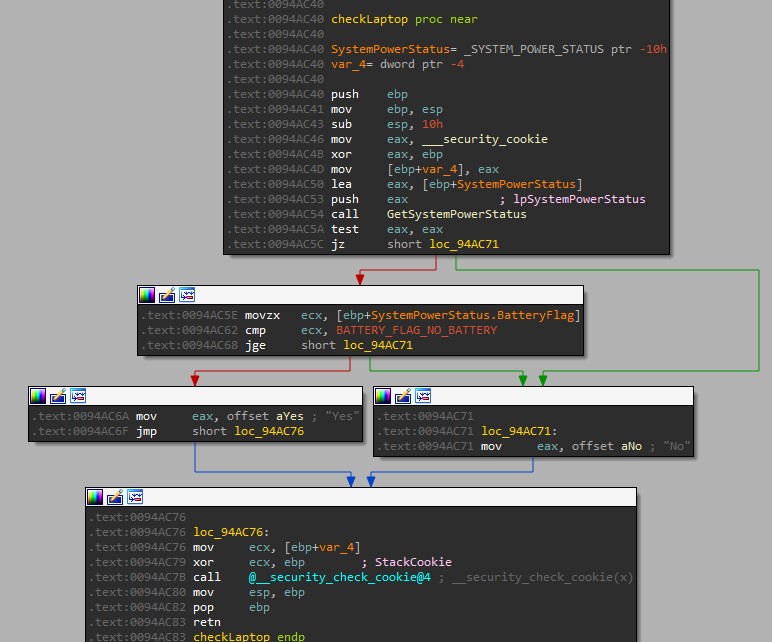
Oski checks the system’s language ID, and if it’s set to Russia, Belarus, Kazakhstan, Uzbekistan, Ukraine, or Azerbaijan, it quits. This tells us something about the origin and the authors of the malware.
If the infected machine uses any other language, the stealer sets up its working environment by downloading seven DLLs from the C2 server and saving them on its ‘ProgramData’ folder. This is the same place where the stolen data is stored before it gets exfiltrated.
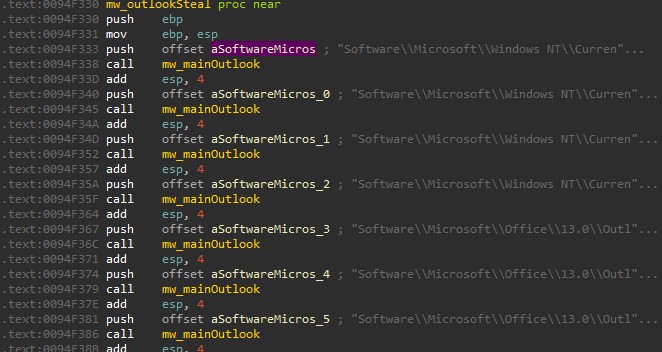
The malware is so valuable in the hands of the threat actors because it is so versatile. It can steal data from over 60 different applications, ranging from web browsers, email clients, and desktop cryptocurrency wallets.
The screenshot capture functionality makes the collection of information from non-supported apps possible too, so if you’re dealing with an Oski infection, nothing can be considered safe or “out of reach.”
One solid way to protect yourself from info-stealers is to enable and use MFA wherever that’s possible. Even if a hacker has your valid credentials, the MFA step will stop them from gaining access to your accounts. As for how to prevent an Oski infection in the first place, you can start by avoiding software downloads from obscure and shady corners of the net.