Octalyn Stealer Malware Targets VPN Configurations and Cryptocurrency Wallets
- Cryptocurrency theft: Octalyn Stealer aggressively targets cryptocurrency wallets like Bitcoin, Ethereum, Litecoin, and Monero.
- VPNs targeted: It captures VPN configuration data, browser credentials, and account tokens for social and gaming platforms.
- Why it matters: Its alarming precision and efficiency raise concerns for individuals and organizations alike.
The Octalyn Stealer malware has emerged as a sophisticated tool designed to steal VPN configurations, browser credentials, and cryptocurrency wallet information, leveraging a legitimate forensic toolkit disguise.
Ostensibly a legitimate forensic toolkit, this malware demonstrates advanced data theft capabilities, significant stealth, and robust persistence mechanisms, making it a formidable risk for organizations and individuals in 2025.
How the Octalyn Stealer Malware Works
Octalyn Stealer operates under the guise of an educational research tool, which is openly accessible on GitHub, according to a Cyfirma security report published this week.
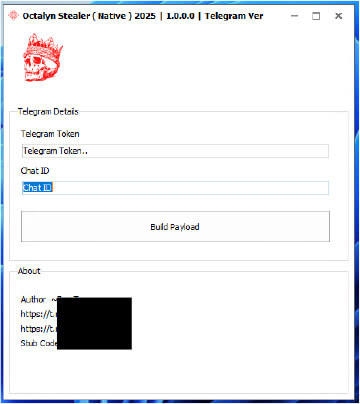
It features a dual-language architecture: a C++ core payload responsible for data theft operations, and a Delphi-based builder interface that simplifies payload creation, requiring only a Telegram bot token and chat ID – which significantly lowers the entry barrier for threat actors.
Once deployed, the Build.exe component acts as a dropper, extracting additional executables into the system’s temporary directory. Execution is silent, leveraging the Windows ShellExecuteA API to avoid user alerts.
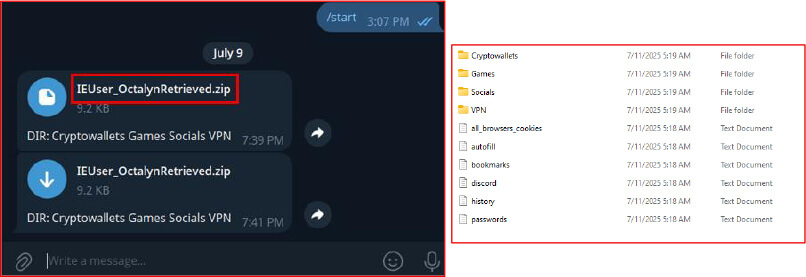
The primary payload creates an organized directory structure for exfiltration. VPN configurations, cryptocurrency wallet data, browser credentials, and other sensitive information are systematically harvested into folders named “Cryptowallets,” “VPN,” “Extensions,” and more.
Targets and Impact
The primary targets of Octalyn Stealer include cryptocurrency wallets across platforms like Bitcoin, Ethereum, Litecoin, and Monero, and it captures wallet addresses, private keys, and seed phrases.
The malware also extracts browser-stored data, including passwords, cookies, and autofill details from Chrome, Edge, and Opera browsers.
With its focus on VPN configuration theft, this malware jeopardizes secure communications and data privacy, particularly for corporate networks and individuals reliant on VPNs for safeguarding sensitive data.
Implications for Cybersecurity
The emergence of Octalyn Stealer marks an evolution in cybersecurity threats for 2025 by masquerading as legitimate software and using tools like GitHub for distribution.
In May, an enhanced version of StealC emerged, as StealC V2 targeted crypto wallets, VPNs, gaming apps, and browsers, while a novel Arcane Stealer strain targeted VPNs and crypto wallets and threatened YouTube and Discord communities in March.