NoName057(16) Dismantled: Europol Leads Global Crackdown on Pro-Russian Hacktivists Striking NATO Allies
- Operation Eastwood: Global authorities have taken down over 100 servers used for DDoS attacks on various entities.
- Why it matters: The group supports Russian narratives against Ukraine and nations allied with the latter.
- Overall results: Two people were arrested, and seven warrants were issued for Russian nationals.
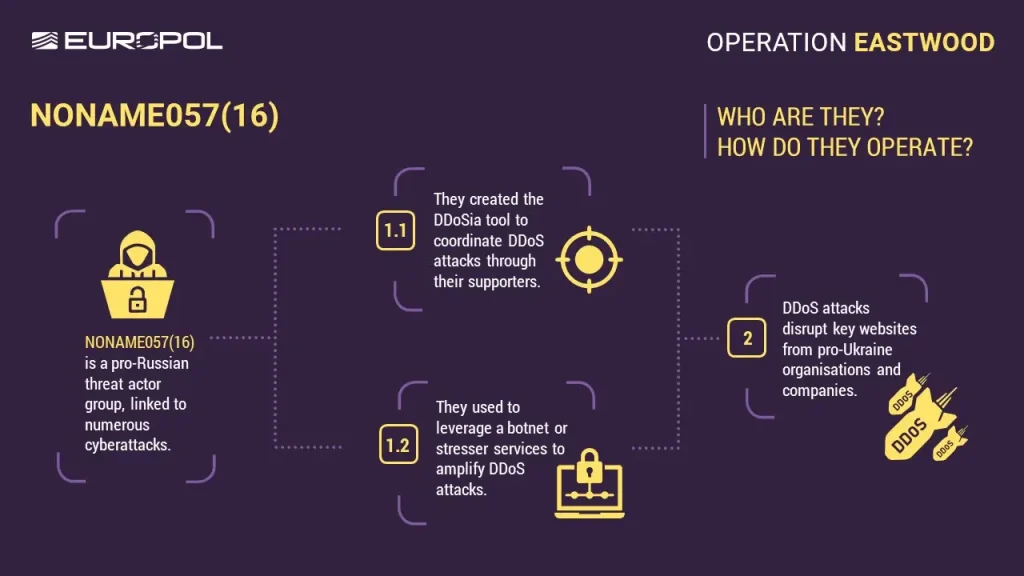
A globally coordinated effort has decimated the infrastructure of the NoName057(16) cybercrime network between July 14 and 17. Described as a pro-Russian network, it has been responsible for Distributed Denial-of-Service (DDoS) attacks linked to ideological motivations.
Spearheaded by Europol and Eurojust, Operation Eastwood saw collaborative actions from law enforcement agencies across 15 nations, including agencies from the United States, Germany, France, Spain, Lithuania, and more.
Scope of Operation Eastwood
Operation Eastwood disrupted over 100 servers globally, while a significant portion of the main infrastructure critical to the network's operations was dismantled, according to the Europol press release.
The initiative resulted in:
- 2 arrests (1 preliminary arrest in France and 1 in Spain)
- 7 arrest warrants issued for Russian nationals
- 24 house searches (2 in Czechia, 1 in France, 3 in Germany, 5 in Italy, 12 in Spain, 1 in Poland)
- 13 individuals questioned (2 in Germany, 1 in France, 4 in Italy, 1 in Poland, 5 in Spain)
- Over 1,000 supporters, 15 of which administrators, were notified of their legal liability via a messaging app
The seven arrest warrants target internationally wanted suspects, of which five are on the EU Most Wanted website. Germany issued six of these arrest warrants, of which two target persons suspected of being the main instigators in the group’s activities.
- MURAVYOV, Andrey; Alias DaZBastaDraw
- LUPIN, Maxim; Alias s3rmax
- EVSTRATOVA, Olga; Alias olechochek, olenka
- BURLAKOV, Mihail Evgeyevich; Alias Ddosator3000, darkklogo
- AVROSIMOW, Andrej Stanislavovich; Alias ponyaska
Last year, three individuals were arrested in Spain in connection with NoName057(16) activities.
Activities of NoName057(16)
NoName057(16) operated without hierarchical leadership and communicated via pro-Russian channels, forums, and chat groups on social media and messaging apps, including Telegram, with volunteers recruiting friends or contacts from gaming or hacking forums.
It's estimated that 4,000 contributors were motivated by ideology and rewards, with recruitment methods involving gamified incentives, leader boards, badges, cryptocurrency payments, and digital accolades.
Network sympathizers relied on automated tools like DDoSia, which they freely hosted on GitHub.
These targeted high-profile organizations, such as government entities, NATO members, and businesses in countries providing aid to Ukraine – and included a collaboration between NoName057(16) and Z-Pentest to attack cities in Poland.
Broader Implications for Cybersecurity
The success of Operation Eastwood signifies a pivotal disruption of NoName057(16)'s campaigns. The network’s reliance on gamified recruitment and decentralized operations showcases evolving tactics in cyber warfare.
Operation Eastwood follows other recent successful operations, as 4 Phobos Ransomware-linked Russians were arrested in a Europol and Eurojust crackdown, and “Manson Market” and related fake online shops were dismantled in a large-scale Europol operation.