New WordPress Malware Can Find and Disable Security Plugins
- A new WordPress malware written in PHP can find and disable security plugins on websites.
- The malware is very persistent and runs continuously to disable any reactivated plugins.
- Only server-level scanners and file integrity alarms can help against this type of threat.
If you rely solely on security plugins to keep your WordPress site safe from external threats, you may want to start doing more. As Sucuri researchers warn, there’s a new PHP malware out there that’s capable of finding and disabling security plugins, essentially left to operate undetected.
The disabling of the plugins takes place immediately while trying to reactivate them from the dashboard only appears to work momentarily. This means that the malware is constantly looking for security plugins and disables them in frequent intervals.
The researchers also point out that this new malware is pretty good at distinguishing between security and non-security plugins, leaving the latter unaffected. In the following GIF, Sucuri demonstrates this on six plugins, the four of which are security-related.
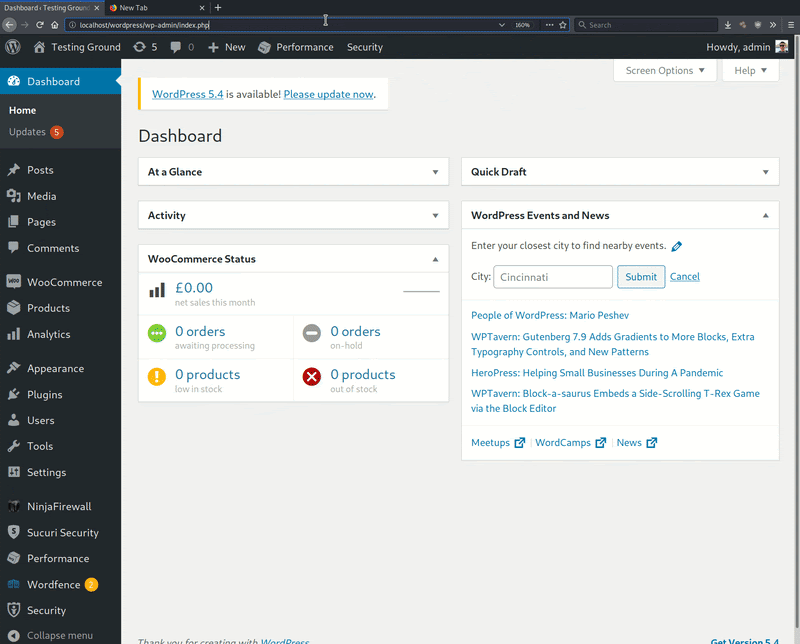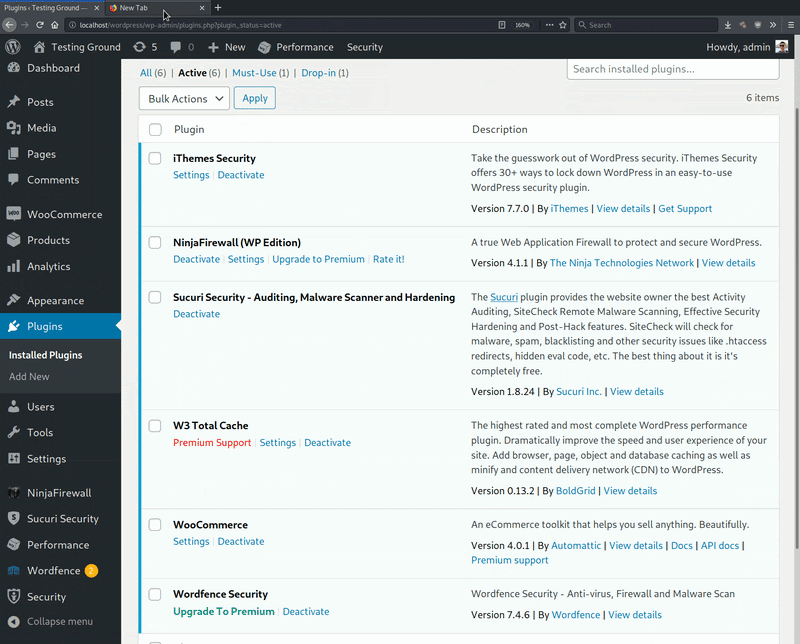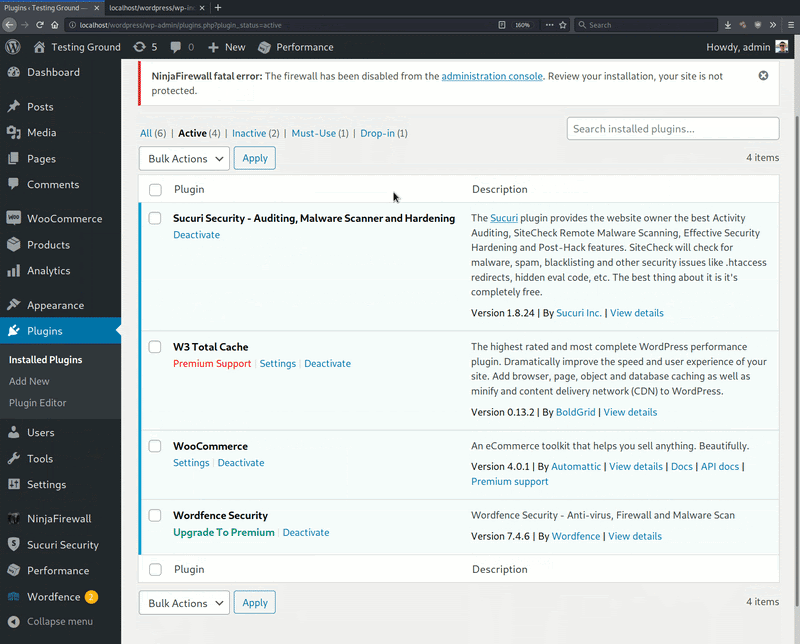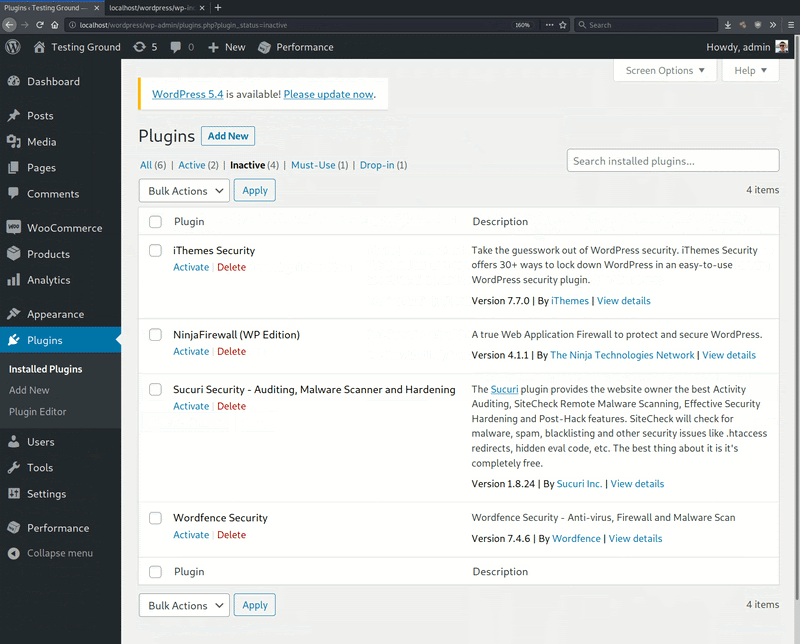
The malware itself attempts to obfuscate its loading step and uses WordPress coding hooks and variables to fiddle with the security plugins without leaving detectable traces.
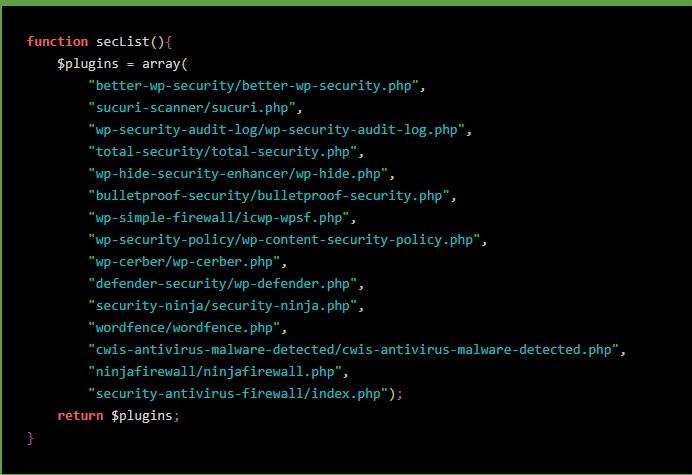
The plugins are scrutinized by a function named “findinSecurity,” which links to a “secList” that serves for the data comparison action. So, there’s a hardcoded list with known security plugins, and if any of them are found on the target website, they are disabled.
Source: Sucuri
The inability to reactivate these plugins is attributed to the fact that the malware is injected on the wp-load.php file. So essentially, the malware is re-running with every WordPress site load. This includes both users and website visitors, so practically, the malware loads all the time.
Related: The Official Facebook Chat Plugin for WordPress Was Vulnerable to Takeover
The only way to deal with this problem is to delete the malware from the website, but in order to do this, one would have to identify its existence in the first place. A solid sign is the inability to activate security plugins.
Additional security and risk mitigation steps that website admins can take include setting up a server-side scanner. Such a tool could scan the website on the server level, so malware code can be detected and unearthed.
Similarly, website file integrity monitors can play a protective role, informing the admins of suspicious changes resulting from malware infection. Whatever you do, don’t rely only on security plugins, as these can only offer the first line of defense, and one at a vulnerable level.