Tupperware Website Got Infected With Magecart Skimmers
- The checkout page on “tupperware.com” has been infected with card-stealing skimmers.
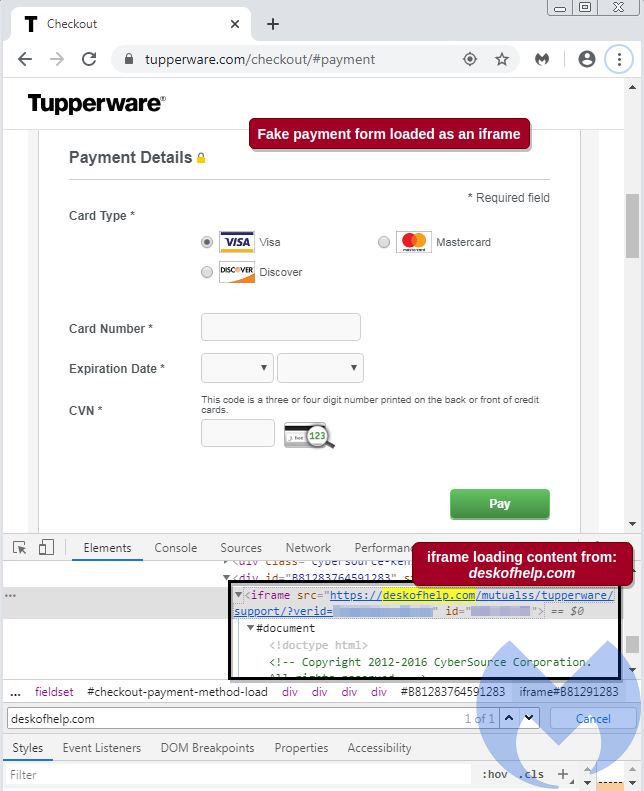
- The victims were urged to enter their payment details on a spoofed payment form loaded by a malicious image.
- The Magecart skimmer remained operational on the popular website for at least five days.
Researchers working for Malwarebytes have found card data-stealing skimmers on the online shop of “Tupperware,” one of the most widely known and trusted kitchen and household products makers. The discovery happened on March 20, 2020, and the researchers attempted to notify Tupperware of the risk. While they tried to reach the company via emails, phone calls, Twitter, and Linkedin, no representative answered them. It means that “tupperware.com,” a website that receives prodigious amounts of user traffic, remained a risk for its visitors, as the skimmer kept running on the checkout page, collecting customer payment data and card details.
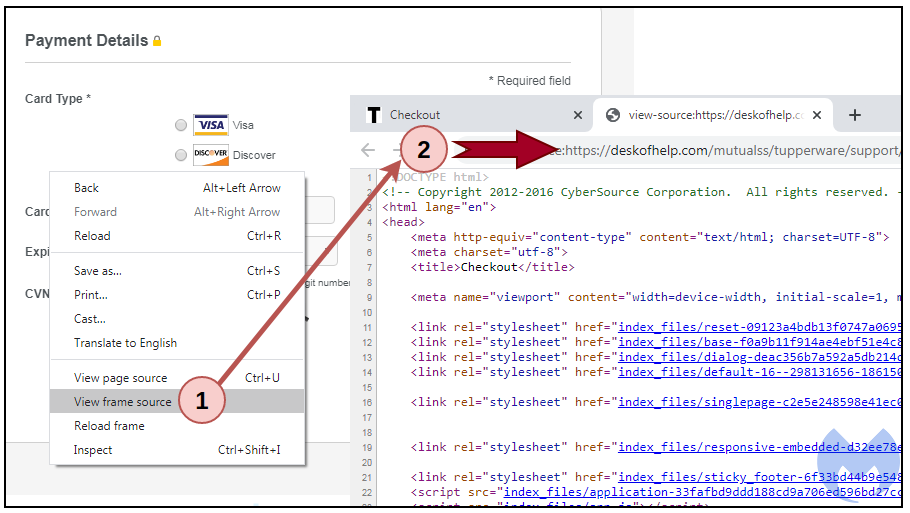
More specifically, the actors managed to plant a script that loads an iframe container displaying a spoofed checkout page. There, the victims enter their first and last name, billing address, telephone number, credit card number, expiration date, and the CVV safety code, and everything is sent directly to the Magecart actors. The researchers noticed that the domain that receives this data was created on March 9, 2020, it is registered to a Russian email address, and it resides on a server were numerous phishing websites are also hosted.
Source: Malwarebytes blog
Even if someone went through the trouble of inspecting the HTML source code of the Tupperware checkout page, they wouldn’t see the skimmer. It is because the malicious snippet is loaded dynamically in the Document Object Model. One giveaway of the form being fake is the fact that there has been no implementation of localization for different languages. The Tupperware website supports other languages besides English, so the payment form should not be limited to English only. While this might save clients that use different languages, most of the Tupperware traffic comes from the United States, so the skimmer could work well with the majority.
Source: Malwarebytes blog
Once the victims enter their payment data onto the spoofed form, they get a fake “session time-out” error and will be redirected to the legitimate payment form. Then, they will enter their data again, thinking that the system wasn’t active the last time, and they eventually complete their order. Another interesting aspect that reflects the priggery of the actors is that they also planted a steganographic PNG image resembling a FAQ icon, which loads silently on “tupperware.com.” In the hidden code, there’s an encoded JavaScript snippet, which is eventually acting as the loader of the rogue iframe.
Source: Malwarebytes blog
After all that, and with Malwarebytes and Sucuri adding protection measures for the Tupperware website, the malicious JavaScript code and the PNG file were removed on 03/25 at 1:45 PM PT. The time of the initial infection remains unknown, so if you’ve bought something from that website, make sure to monitor your account activity and immediately report any fraudulent charges to your card issuer.