New QakBot Campaign Is Showcasing Novel Detection Evasion Techniques
- The QakBot banking trojan has broken its malicious functionality into chunks, and AVs have trouble detecting it.
- The actors are delivering the payload-fetching documents in a compressed archive form instead of a Word file.
- All this helps evade detection, bypass email security checks, and run in the background without generating alerts.
A QakBot/QBot campaign that started a couple of weeks back is showing new ways of evading detection of analysis, so it appears that the author of the widely known and used banking trojan has pushed a fresh version out in the wild. Morphisec researchers have sampled these new variations and give details on what’s changed in a report.
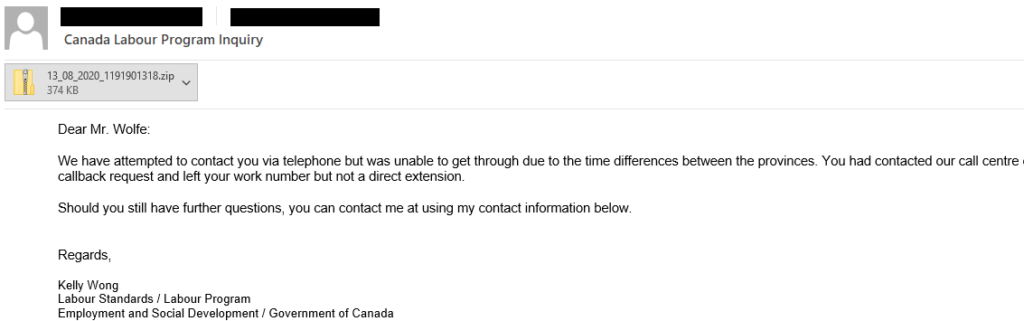
As they say, the method of distribution remains the typical macro-ridden documents that arrive in attached ZIP archives via email messages. These Word files run PowerShell scripts that fetch the QakBot payload from the C2, but this is where following the trodden path ends.
Source: Morphisec Blog
The first new technique that comes with the latest QakBot version is a new “content disarm and reconstruction” (CDR) technology that is meant to help pass through security checks and filters. This is done by ZIPing the malicious document instead of sending it as a Word file, a simple yet very effective method of bypassing email defenses.
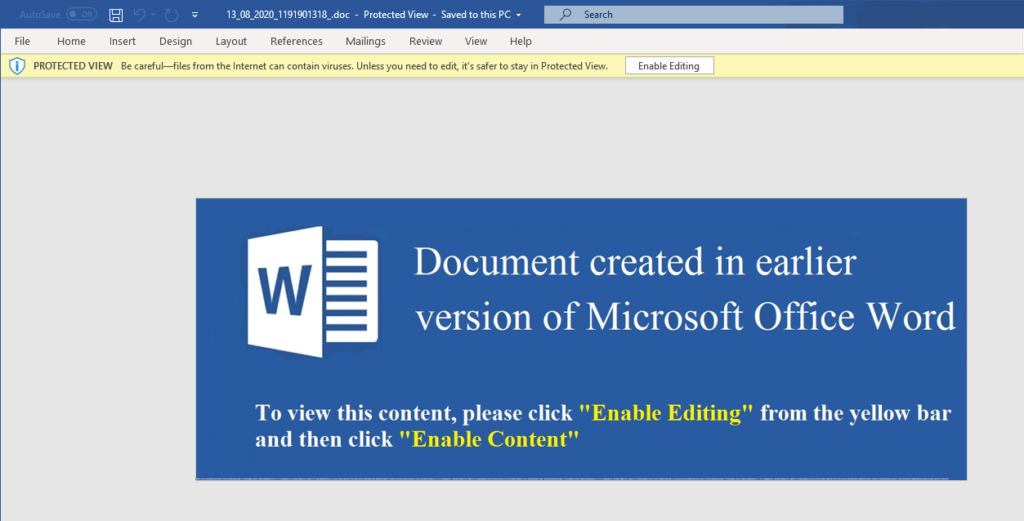
To convince the recipient that they need to enable macros on their Office suite, the actors have added a message that informs them that the document was created on an earlier version of MS Office. Supposedly, the victim needs to “Enable Content” to view it.
Source: Morphisec Blog
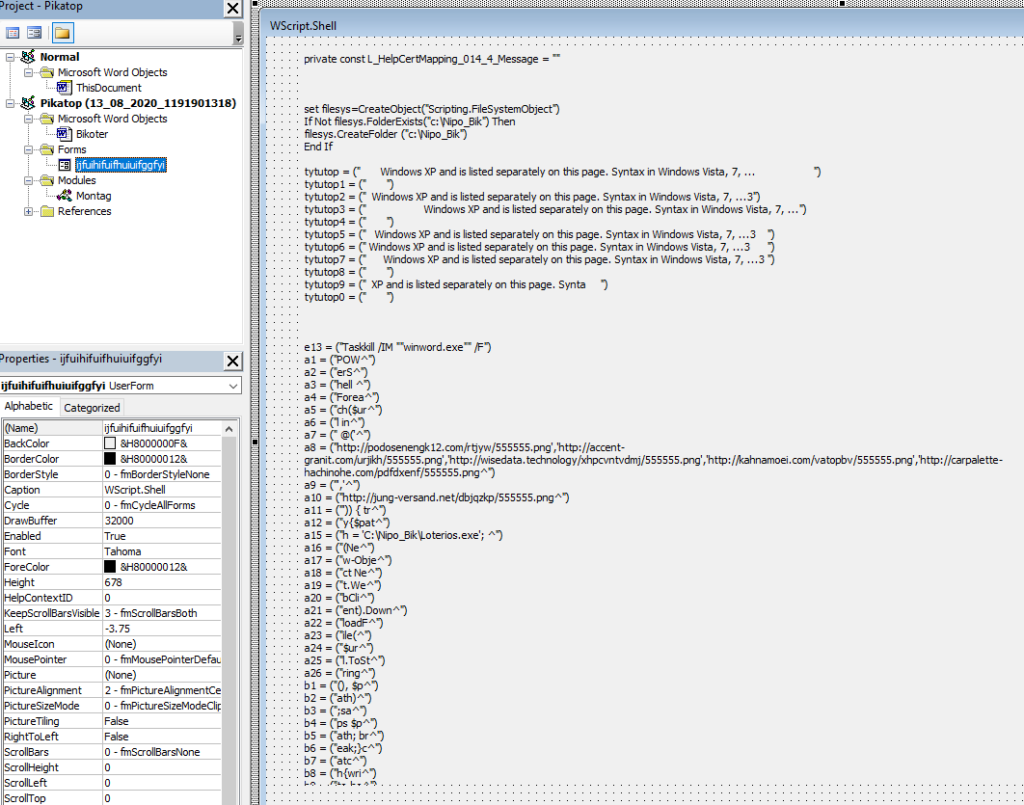
If they do, a series of script executions will result in the fetching and execution of the QakBot payload. Along the way, traces of these consecutive executions are deleted, while the key Visual Basic functions are routed through “explorer.exe” to avoid detection. While all that contributes to the stealthiness and effectiveness of QakBot, using an up-to-date AV tool should be enough to detect the polymorphic banking malware activity.
Morphisec says the distributed behavior and breaking of the functions in smaller chunks makes it more challenging for some AVs to catch the threat. Still, in general, the most reputable tools should work as expected.
Source: Morphisec Blog
The report mentions an uptick in the delivery of QakBot over the last few months, which is understandable considering the fact that it can evade detection. This is a ten-year-old trojan we’re talking about here, but it remains a menace for users since it can steal banking credentials and help actors take over accounts.
If you want to minimize the chance of something like that happening to you, don’t enable macros on your Office suite, don’t download and open documents that arrive via unsolicited emails, and keep your system and AV tools up to date.