Nemty Ransomware Evolving to Kill Processes and Services
- Nemty can now kill processes and services and encrypt files that are underuse.
- Examples include virtual box systems and files, Thunderbird emails, and Word files.
- Nemty seems to want to keep a low profile right now, and until it gets powerful enough.
As we have seen recently, Nemty is a popular piece of ransomware, getting deployed in various fraudulent campaigns. While it’s not as “hot” as the “REvil”, aka “Sodin”, aka “Sodinokibi", it still receives development care, evolving into a more powerful tool day by day. As the security researcher and reverse engineer analyst Vitali Kremez reports, there’s a new version of Nemty out there, capable of killing system processes and services. This powerful addition could be the key to finally raising the acceptance rates of Nemty by the “ransomware as a service” community since that’s the main target of its creators after all.
Vitali Kremez reports that in spite of the fact that the Nemty just got upgraded, the version number remains the same. This could be either to trick researchers and protection measures or to designate that the developers have not finished what they are working on yet. Either way, Nemty just got more aggressive and dangerous, and since it’s already in circulation, version numbers don’t make a difference in practice.
Source: bleepingcomputer.com
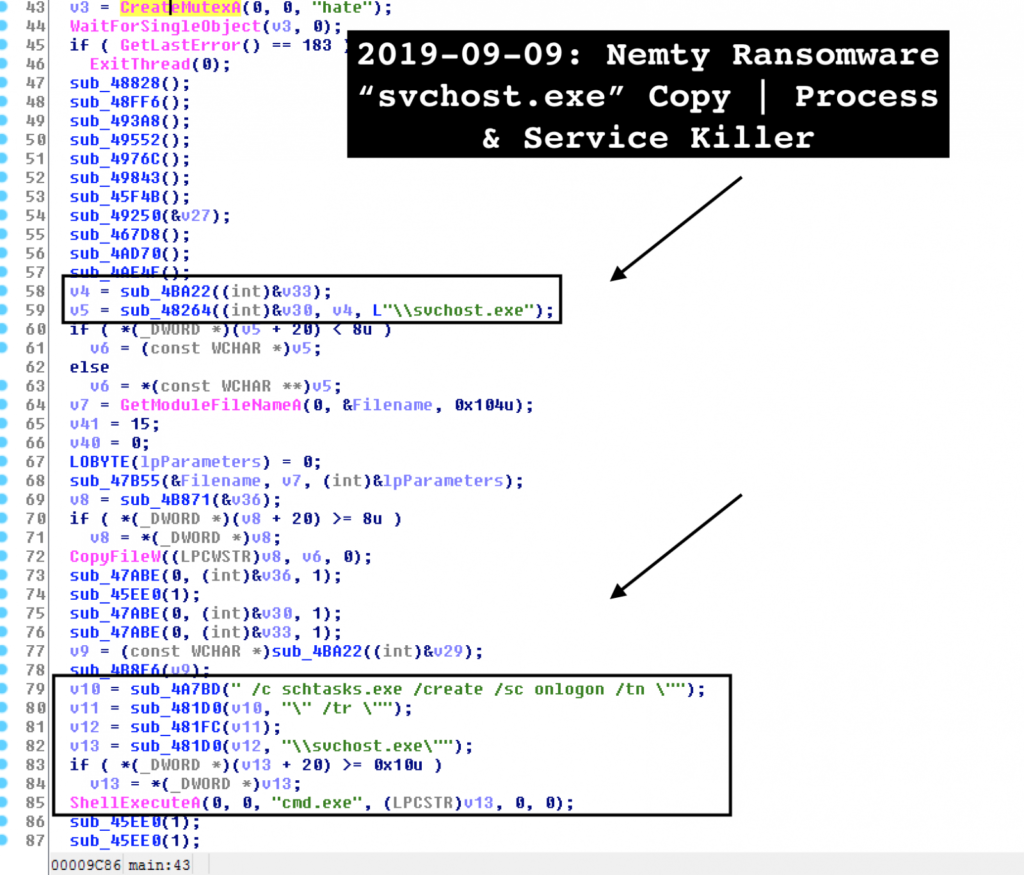
The new code additions make it possible to kill running processes on the victim’s system. What this does is to enable the ransomware to encrypt all files on the host system, including those that are currently in use. The processes that the new Nemty variant targets include MS Word, Excel, Outlook, Mozilla Thunderbird, SQL, and even VirtualBox. This means that if executing a file suddenly shuts down any or all of the above applications, you have probably stepped onto the Nemty trap.
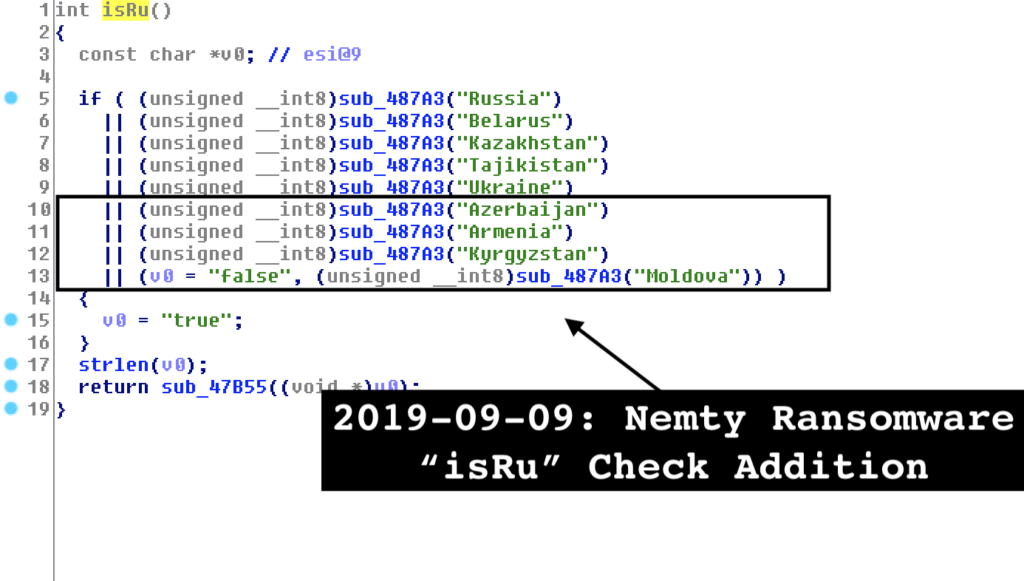
The recent upgrade doesn’t bring only new features, however. Kremez noticed that there are new countries that have been added into the ransomware’s exclusion list, with Azerbaijan, Armenia, Kyrgyzstan, and Moldova joining Ukraine, Tajikistan, Kazakhstan, Belarus, and Russia that were already in the blacklist.
Source: bleepingcomputer.com
As for the distribution of Nemty, last time, we saw that happening through the RIG EK exploit kit. Now, the actors are experimenting with Radio EK, which is targeting a vulnerability in Internet Explorer that Microsoft patched three years old. This is good news for now, as the distribution of the new Nemty cannot be massive. However, this could mean that it's all part of a testing process, trying things out while getting all modules ready, and keeping a low profile in the meantime. Keeping the version number unchanged and using a weak distribution channel are two ways to avoid drawing attention until you’re ready to hit hard.
Have something to comment on the above? Feel free to share your thoughts with us in the comments down below, or on our socials, on Facebook and Twitter.