Microsoft Warns About the Evolution of the ‘Phorpiex’ Worm
- ‘Phorpiex’ is evolving to carry more dangerous payloads and target even more countries.
- The operators of the botnet have recently made an effort to refresh their infrastructure.
- The particular worm has been around for over a decade, but it’s still a valuable tool for crooks.
It’s been a while since we last discussed anything that had to do with ‘Phorpiex,’ an enduring old-school botnet that spreads on infected systems like a worm. Microsoft has posted a blog today, warning about the recent developments in the project, which make the botnet quite a lot more dangerous and far-reaching. As Microsoft’s telemetry data shows, Phorpiex is now contracted by various ransomware gangs, like the highly successful Avaddon, and is spreading to a lot more countries than before.
Although the tactics, techniques, and code of the Phorpiex botnet remained unchanged all these years, even after thorough white-hat analysis, the authors are now making an effort to refresh their C2 and jump to DGA (domain generation algorithm) instead of relying upon static domains. The distribution of the bot takes place via a variety of means, including hiding it inside freeware, executables, attaching it on phishing emails, propagating it on instant messaging platforms, and the old-time classic, lacing USB drives.
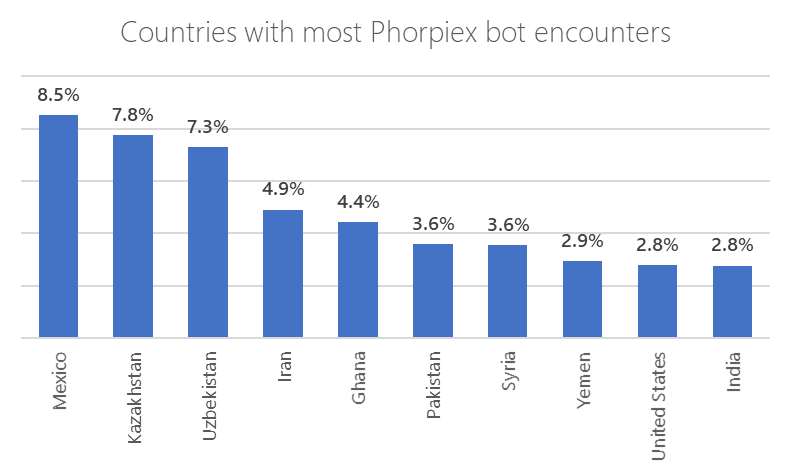
Microsoft reports that the most affected countries are Mexico, Kazakhstan, Uzbekistan, Iran, Ghana, Pakistan, Syria, Yemen, the United States, and India.
Another aspect of Phorpiex that was added at a later stage is the utilization of the XMRIG miner to monetize the hosts. The trick is done by fetching masqueraded modules that even checked for signs of VM environment before they went on with the mining. A few months ago, Phorpiex started delivering Ethereum miners that scheduled tasks labeled as “WindowsUpdates.”
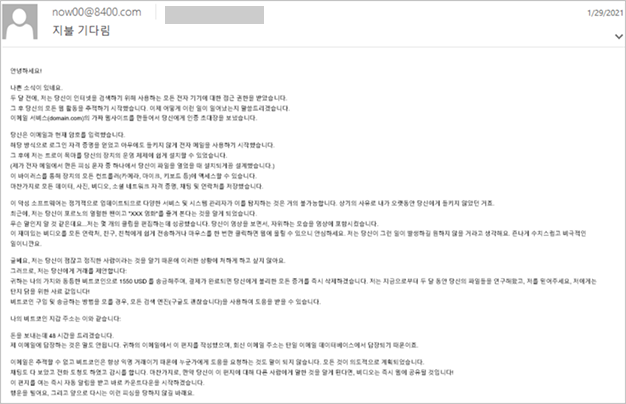
In addition to all that, Phorpiex is also engaging in the extortion schemes space, sending out BEC (business email compromise) messages. Microsoft gives an example in the Korean language, indicative of the widespread operation of the botnet.
By analyzing large volumes of Phorpiex emails, Microsoft’s researchers were able to discern some common characteristics that are tell-tale signs:
- Spoofed sender domain, sender username, and sender display name
- Sender domain of 4 random digits
- Sender username using a generic name with a variety of numbers
- Subjects or lures referencing singular names, heights, and weights, surveillance
- Body of the message often referencing dating services or extortion material for ransom
- Presence of Bitcoin, DASH, Etherium, or other cryptocurrency wallets
- ZIP files or other file types purporting to be images such as JPG files or other photo types.
As for the money that Phorpiex makes through extortion, some wallets that were monitored lately indicate that the average amount asked is $950, and the actors are making $13,000 in ten days.