Microsoft Is Urgently Warning Users of Zero-Day Flaws Being Exploited
- Microsoft discovered highly malicious targeted activity exploiting zero-day flaws in Windows.
- The tech company has provided three mitigations, but a full fix will arrive in about three weeks.
- The flaws affect all Windows versions, and they are as easy to exploit as previewing a document on Explorer.
Microsoft has released a security advisory to warn users of unpatched zero-day flaws that are being under active exploitation, albeit at a limited scale. The vulnerabilities exist in the way that Microsoft Windows handles a particular font format through the Adobe Type Manager Library. Unfortunately, there are multiple ways to exploit the flaws and open the door to remote code execution. The simplest of all would be to convince the victim to open a document, whereas merely viewing it in the Windows Preview mode would be enough to create successful attack conditions.
The Windows versions that are impacted by this flaw are Windows 10, 8.1, Server 2008, 2012, 2016, 2019, and the unsupported Windows 7. Microsoft is working on a fix to the identified flaws which will arrive on April 14, 2020, with the Patch Tuesday updates. Until then, you may apply the following workarounds.
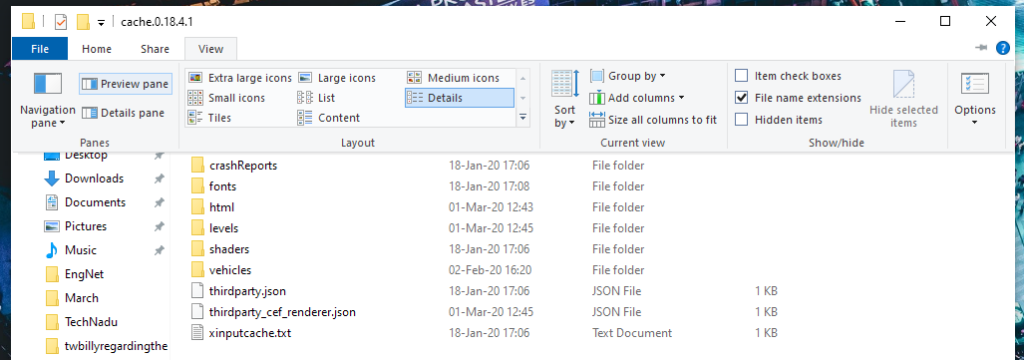
- Disable the Preview Pane and Details Pane in Windows Explorer, and any other file manager that you may be using. This will have an impact on the users’ productivity, but it will prevent the attack from working easily on the target. You may find the relevant setting under View, and disabling the Preview and Details Pane. Alternatively, press "Alt+P."
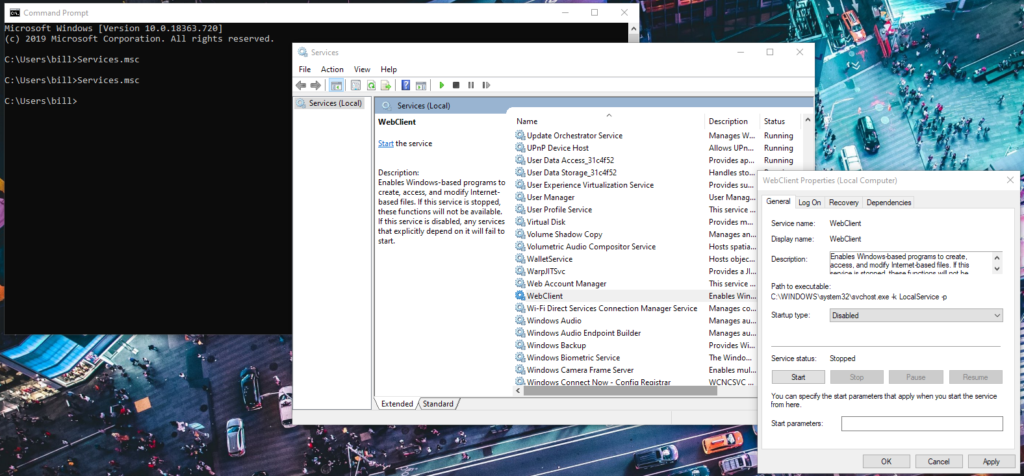
- Disable the Windows WebClient service to prevent any WebDAV-based attacks. Run Services.msc on the command prompt, select “Properties” on the WebClient icon, and set “Startup” to disabled. If the service is currently running, you should stop it.
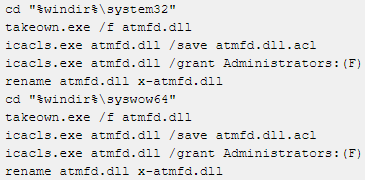
- Disable the Adobe Type Manager Font Driver (ATMDF.dll), or at least rename the file. This will cause problems to third-party applications that need embedded font technology, but it will result in solid risk mitigation. For this, enter the following commands at a command prompt as an admin:
Source: Microsoft
The above mitigations don’t address the full spectrum of potential attack methods, but they will at least make it harder for the attacker to exploit the zero-day bugs. As Microsoft clarifies, activating the “Enhanced Security Configuration” won’t mitigate the flaws, and won’t reduce the attack vectors. Users of Windows 7, Windows Server 2008, or Windows Server 2008 R2 will only receive the security update that addresses the discovered problems if they have a valid ESU license. Finally, Microsoft clarified that the Outlook Preview Pane is not vulnerable to exploitation by malicious documents, so you may leave this active.