Malicious Chrome Extensions Steal User Data Through Fake Free VPN Tools
- Massive Malicious Extension Campaign: Attackers ran fake VPN/ad-block extensions with 9M installs, hijacking traffic and stealing browsing data.
- Advanced Stealth & Control Mechanisms: Extensions used remote configs, dynamic code, and proxy manipulation for full user traffic interception.
- Persistent Threat Despite Takedowns: Removed variants kept reappearing, showing weak extension vetting and high user risk.
Security researchers at LayerX Security have uncovered a long-running malicious campaign involving fake VPN and ad-blocking browser extensions that secretly intercept user traffic and steal browsing data. Despite multiple takedowns, the operators behind these extensions continue to revive the campaign with new versions designed to avoid detection.
According to LayerX, the latest wave of malicious extensions currently has more than 31,000 active installations, while earlier versions accumulated over 9 million installs on the Chrome Web Store.
The findings highlight the growing risk posed by browser extensions and how easily threat actors can exploit user trust, especially when promoting “free” privacy tools.
Six Years of Activity Behind a Polished Front
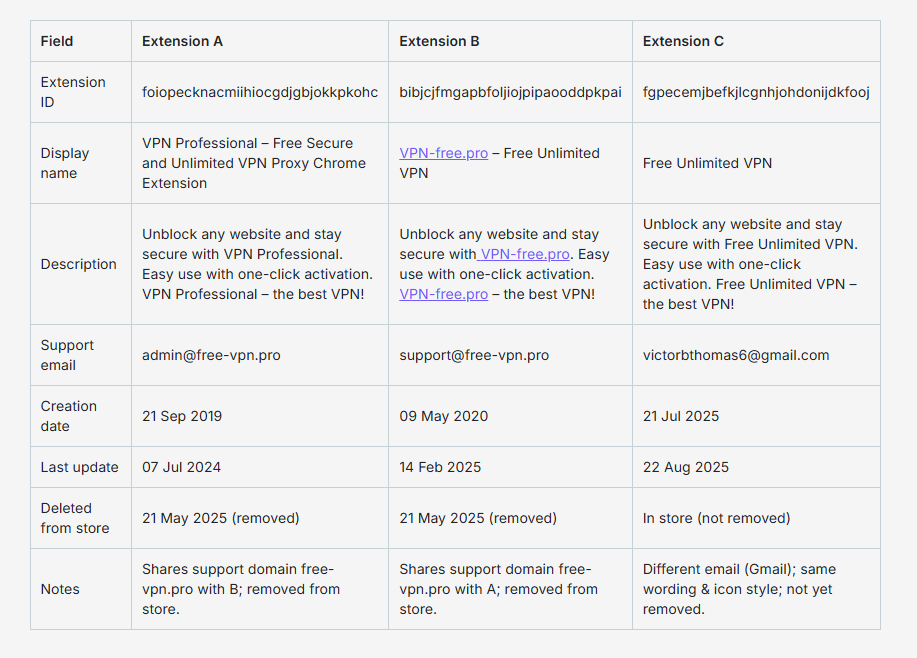
Researchers found that three fake Free VPN Chrome Extensions claiming to be “Free Unlimited VPN” services remained on the Chrome Web Store for nearly six years before they were identified as malicious.
These extensions used professional branding, convincing descriptions, and well-designed icons to appear legitimate. However, underneath, they contained hidden surveillance code capable of collecting user activity.
Two of the VPN extensions were removed in May 2025, but only two months later, a third extension, with almost identical visuals, descriptions, and internal behavior, returned to the store. As of now, this version remains available.
More Than Fake VPNs: Remote-Controlled Traffic Redirectors
LayerX researchers say these weren’t typical VPN tools. Instead, they acted as remote-controlled proxy redirectors, giving attackers control over the victim’s browsing activity.
The extensions downloaded hidden configuration files from attacker-controlled servers and modified browser proxy settings in real time. They also monitored navigation events, allowing them to intercept and redirect traffic as users browsed.
The 2025 version was even more advanced. Among its stealth features:
- Delayed activation to avoid early detection
- Dynamic code downloads executed at runtime
- The ability to disable other proxy extensions
- Hidden update channels
- Minimal forensic traces left behind
With these capabilities, attackers could intercept every page a user visited, collect full browsing histories, gather lists of installed extensions, and route traffic through malicious servers.
Privacy Breach and Ongoing Threats
The malicious extensions regularly collected hashed URLs from users’ browsing sessions and uploaded them to command-and-control servers for profiling. They also scanned installed extensions and intercepted navigation requests to enable targeted phishing, forced redirects, and potential malware downloads.
The campaign used advanced evasion tactics, including:
- Timing-based tricks to avoid sandbox detection
- Clearing browser history entries related to redirects
- A remote self-uninstall feature to hinder analysis
Researchers have identified six more extensions connected to the same threat actors, disguised as ad blockers and music downloaders. This indicates the operation is significantly larger than it first appeared.
What Users and Organizations Should Do
The repeated cycle of takedowns and reappearances shows that reactive measures alone are not enough to stop malicious extensions.
Experts recommend:
- Organizations should adopt continuous extension monitoring, enforce strict extension-install policies, and track behavioral anomalies in real time.
- Users should be cautious with “free” privacy tools, verify developer legitimacy, and routinely check installed extensions for suspicious permissions or unfamiliar names.
LayerX’s discovery of these fake free VPN Chrome Extensions serves as another reminder that browser extensions, often trusted without a second thought, can become powerful surveillance tools in the wrong hands.