Magecart Skimming Actors Now Target Hotel Booking Mobile Sites
- Two large hotel chains have had their payment webpages compromised by card skimming scripts.
- The Magecart campaign is based on the injection of code in a module of their website developer.
- The actors are using their own custom fake payment form to steal the credit card data directly.
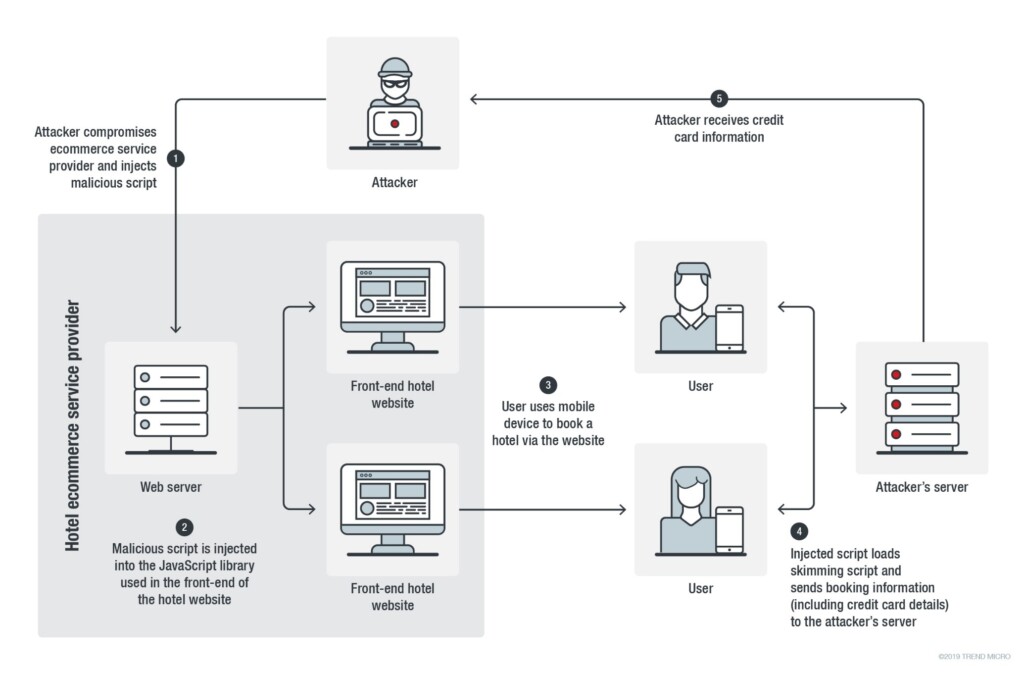
According to a Trend Micro Security Intelligence report, there’s a new Magecart skimming campaign that targets people who try to book hotel rooms via mobile websites. Trend Micro researchers have found that two hotel websites belonging to two different chains have been infected with JavaScript code that loads a remote script on their payment webpage. The discovery was made in September, while the malicious script was found to have been injected on August 9, 2019. The script link downloaded another script when using Android or iOS devices, eventually loading a credit card skimmer that steals the customer’s payment information.
Source: blog.trendmicro.com
Both hotels have had their websites built by a firm called “Roomleader”, and it was one of this company’s modules that was compromised by the Magecart actors. This means that the campaign is based on a production chain flaw and that there must be a lot more hotel chains affected besides the two that were discovered by Trend Micro. Even if the problem was contained only on the two chains, it would still be an extensive one since the first one has 107 hotels in 14 countries and the other has 73 hotels in 14 countries.
Source: blog.trendmicro.com
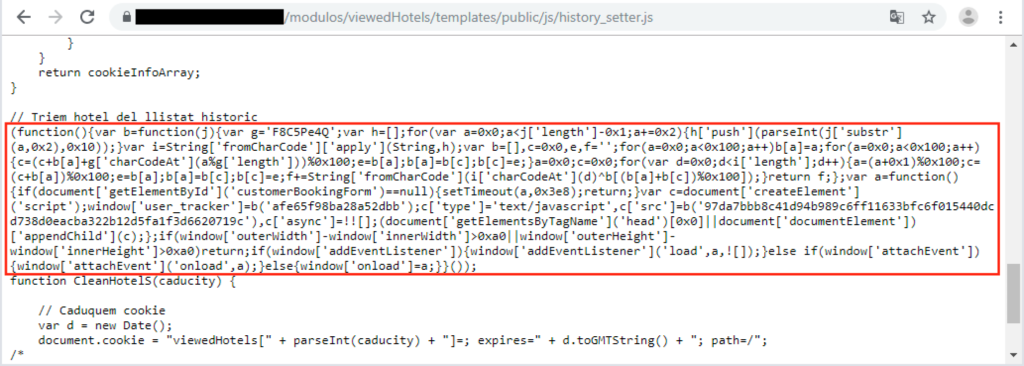
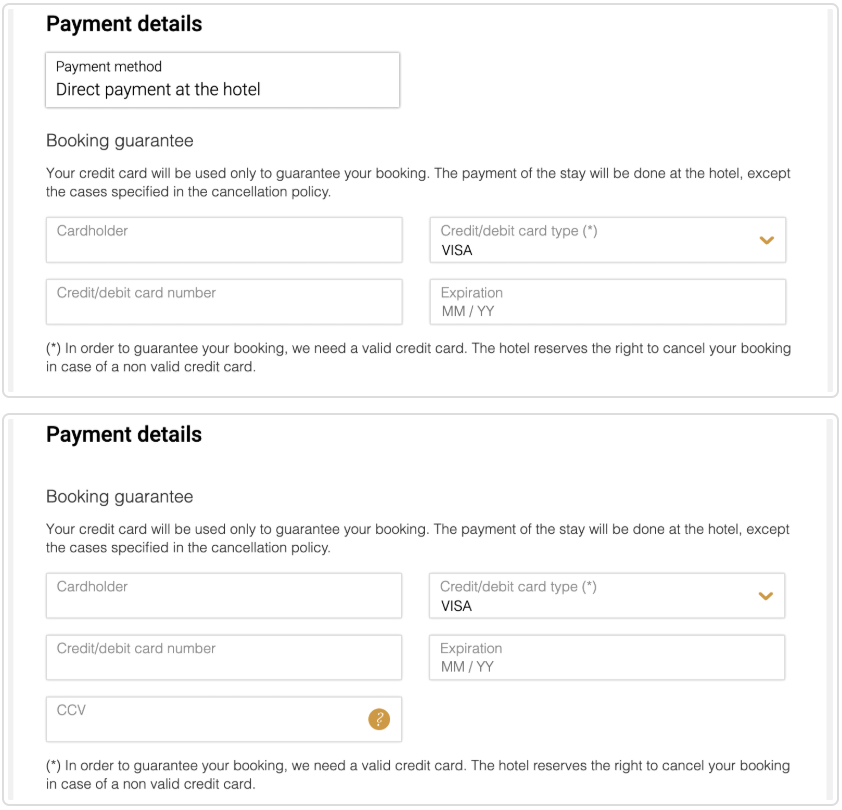
The script checks that it runs on the hotel’s booking webpage, and if it is, it checks that the debugger of the browser is closed. If this prerequisite is met too, it loads another JavaScript from a specified URL and so the skimmer is loaded. The URL that contains the skimmer emulates a Google Tag Manager domain so as to avoid raising suspicions and thus get detected. The skimmer does not just capture what the customer enters on the form but replaces the original credit card form entirely. This is done because hotels may ask you to pay on the desk when you get there, or they may not ask for the CVC number which the actors need. Finally, skimmers don’t work in cases where HTML iframe elements are used, so the exfiltration wouldn’t be possible if the hotel deployed them.
Source: blog.trendmicro.com
The actors have even gone to the trouble of translating their fake form in eight languages, checking what the victim is using on their system and injecting the corresponding form version. This further increases the legitimacy of the fake form and helps to trick the customers. Unfortunately, Trend Micro hasn't revealed which two hotel chains were compromised, so people who made their booking via their mobile websites since August 9 cannot determine if they have had their credit card details stolen or not.
Do you pay online with credit cards, or do you prefer a different payment method? Let us know in the comments down below, or on our socials, on Facebook and Twitter.