Magecart Skimmers Target 201 Campus Stores in the USA and Canada
- A new group of Magecart skimmers called “Mirrorthief” have achieved a blow against PrismRBS.
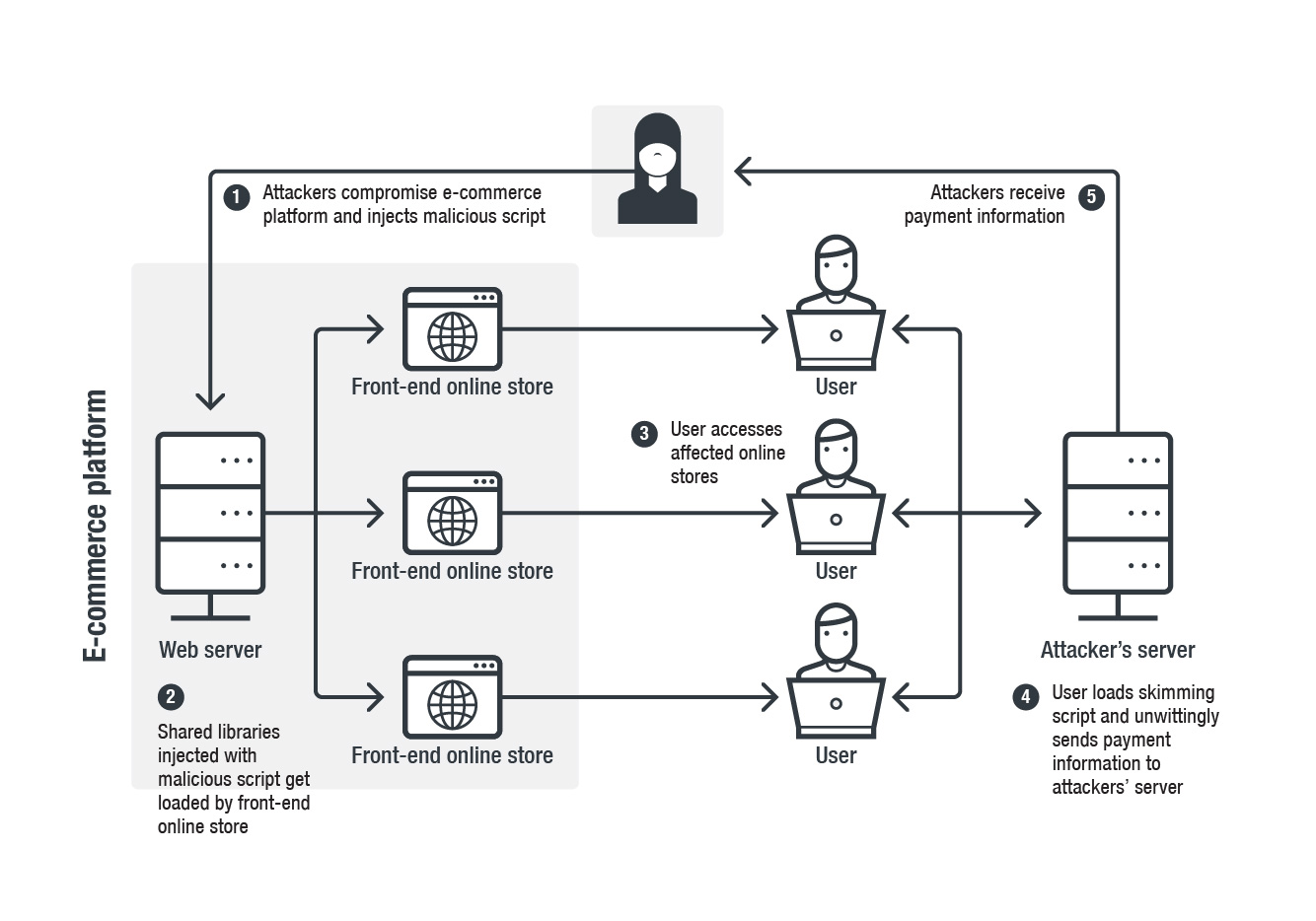
- The hackers compromised the campus-specialized e-commerce platform and infected 201 stores with their script.
- The number of people who had their full credit card details stolen remains unknown.
A report published by Trend Micro registers Magecart skimming activity pointed against 201 online campus stores in the United States (176) and Canada (21). The particular websites were first infected by the malicious script on April 14, with the data-stealing activity going on until the end of the month. The script was planted in the payment checkout pages of the stores, so whatever credit card information was filled out on these pages was also sent to a remote server belonging to the hackers. In all of the compromised campus stores, the e-commerce platform that was deployed is “PrismRBS”.
Image source: blog.trendmicro.com
The actual compromise was made on the PrismWeb platform’s shared JavaScript libraries, a retail business solutions company that specializes in campus retail stores. Unfortunately, PrismWeb didn’t realize the compromise quickly enough, and only thanks to Trend Micro’s notice they took action on April 26. The number of people who had their credit card details (name, number, CVN, expiration date) stolen between April 14 and 26 is currently undetermined.
Right now, PrismWeb is undergoing an investigation, and are notifying the customers that were potentially impacted by the injected code. As they also assured the public: “We are taking steps to further strengthen the security of our systems, including enhanced client-side and back-end monitoring tools and a comprehensive end-to-end audit of our systems. Once our investigation concludes, we will be providing our customers with additional information and guidance.”
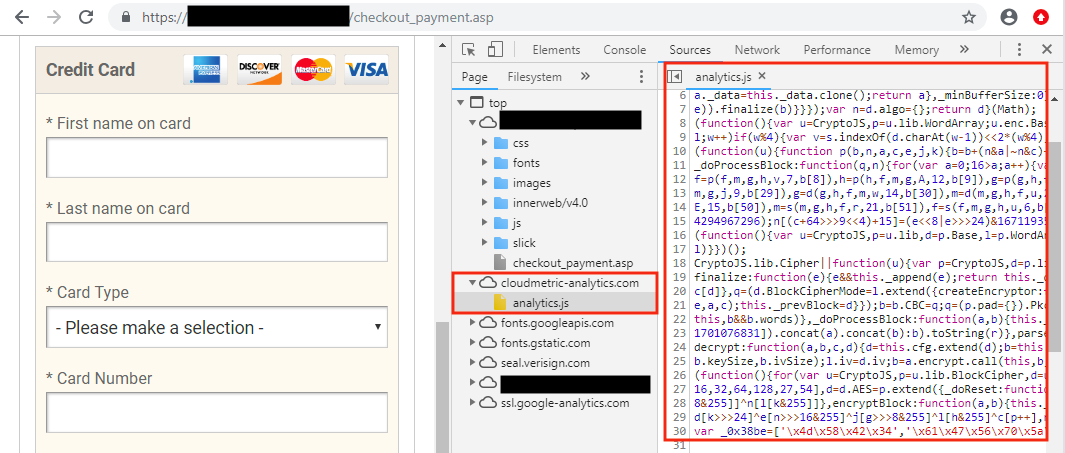
Trend Micro has given the actors the name “Mirrorthief”, as they are using different JavaScript libraries and injection patterns, which means they cannot be identified as one of the previously known Magecart skimming groups. What makes the Mirrorthief stand out is the persistent mimicking of the Google Analytics script. Designed specifically for PrismWeb’s payment page, the particular skimming script collects data only from HTML elements that carry one of the specified IDs on the PrismRBS platform.
Image source: blog.trendmicro.com
To avoid detection, even the domain used by the actors is quite similar to the original Google Analytics domain. Almost all websites use Google Analytics, so this tactic is not new or unique in the world of skimmers. However, Mirrorthief uses their own network infrastructure, so they must be a new Magecart cybercrime group.
Have you made any purchases from US or Canadian campus online stores in April? Did you notice any suspicious activity in the meantime? Let us know in the comments down below, and help us spread the word by sharing this post on Facebook and Twitter.