Lazarus Group Continues to Target Cryptocurrency Holders
- The Lazarus hacking group has released a bunch of new malicious crypto-coin transaction tools.
- The group continues to focus on macOS users, but still releases Windows versions of its malware too.
- People are advised to avoid tools named after Cyptian, Union Crypto Trader, WFC Wallet, and JMT Trading.
According to Kaspersky's researcher reports, the notorious North Korean hacking group “Lazarus” is still pretty active and still targets cryptocurrency holders. Last time we checked on the activity of Lazarus was in December when the group was using a new macOS Trojan, going after crypto-coin exchanges again. As it seems, money is still the main target for the group, who have released several pieces of malware that are similar to what was used in the previous operation (codenamed AppleJeus). Kaspersky believes that the author of the new malware strains used the QBitcoinTrader as a basis. Again, the main target is macOS users who are looking to install crypto-coin transaction management tools on their systems.
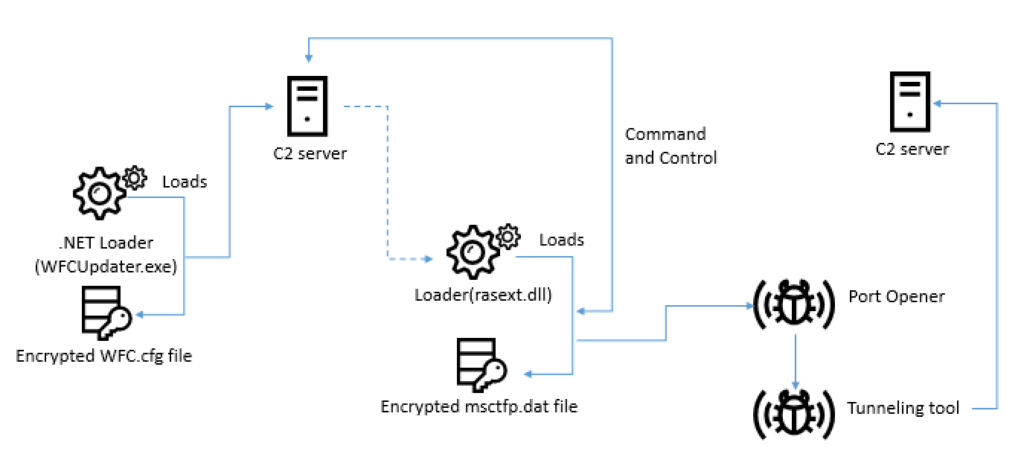
However, Windows users aren’t free of risks either. During their campaign tracking, Kaspersky researchers found a malware installer carrying the name “WFCUpdater.exe”, coming from the fake website “wfcwallet[.]com”. This .NET executable decrypts a configuration file which then carries out the commands of the controller, leading to the fetching and installation of the second-stage payload. From there, the port 6378 is opened in order to accommodate remote tunneling, enabling the remote host can do anything on the victim’s computer.
Source: SecureList
On the macOS, things changed from the “UnionCryptoTrader” tool that was used previously. Lazarus is now promoting their Trojan from the fake website that is named “JMTTrading”, so you should avoid using any tools carrying that name. Instead of the QT framework that was previously used, the malware author is now using Object-C. The other technical details such as the method of encryption, obfuscation, and backdoor functionality remain similar to what we saw previously. As for the infrastructure that is used by the hackers, this remains pretty extensive and is enriched day by day. For now, avoid domains named after Cyptian, Union Crypto Trader, WFC Wallet, and JMT Trading.
Source: SecureList
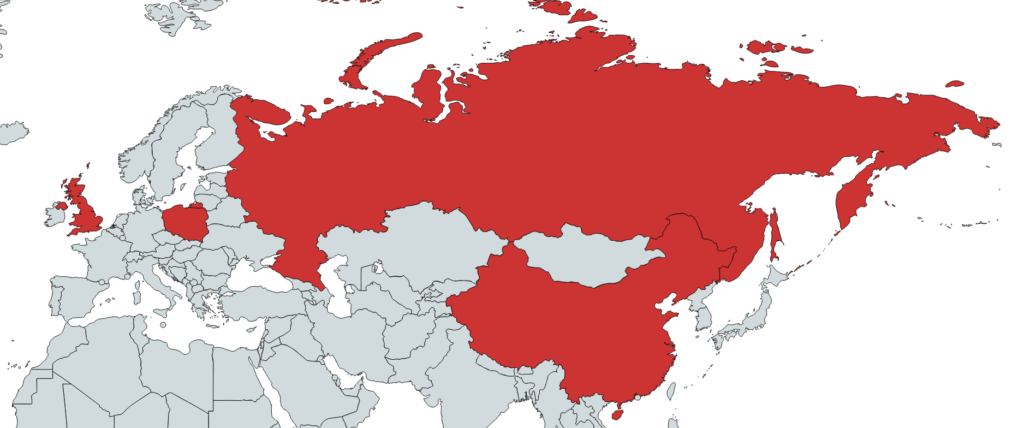
Finally, most of the victims of the latest Lazarus operations are in the UK, Russia, China, and Poland. As explained above, most of these victims are crypto-coin holders, and this is the asset that the hackers are after. That said, this campaign is not dealing with the stealing of information or the interception of communications. Lazarus always needs financial resources to operate, and if the rumors about them aiding the North Korean nuclear programs by stealing money from financial institutions are true, then we shouldn't expect this activity to subside any time soon.
Did you have your crypto stolen by another tool that is not mentioned above? Feel free to share the details with us in the comments down below, or on our socials, on Facebook and Twitter.