Iranian Hackers Are Reportedly Weaponizing Published VPN Flaws in Hours
- At least three Iranian APT groups combined forces to launch attacks against corporate networks.
- Named "Fox Kitten," this campaign was based on the exploitation of 1-day VPN flaws.
- The hackers were ready to weaponize vulnerabilities almost as soon as they were published.
During 2019, there have been multiple reports about risky flaws that underpin widely-used corporate VPN tools. Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs were all found to be vulnerable in some way and, in many cases, the associated proof-of-concept (PoC) code was published as well. This only happened after the vendors were given enough time to push fixing updates. However, thousands of systems remained unpatched, so hackers actively searched for them. According to a report by ClearSky, Iranian hackers were identified as the ones who have been leading this exploitation effort, and they were actually engaging in it since 2016.
Source: ClearSky
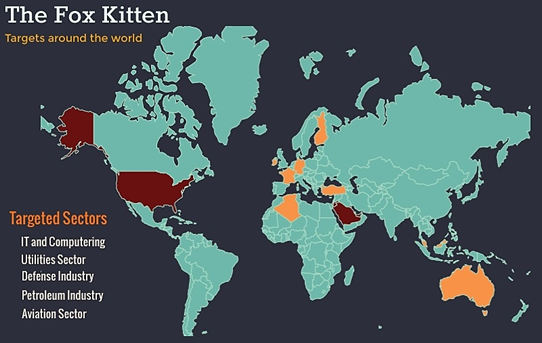
Naming it the "Fox Kitten" campaign, the researchers claim that APT34-OilRig, APT33-Elfin, and APT39-Chafer united their firepower to spread malware strains such as the "ZeroCleare" and "Dustman." These Iranian hacking groups have collaborated to develop and maintain access routes to organizations from around the world, steal crucial data from them, and infect their products to reach more victims through supply-chain attacks. The following map shows which countries were most targeted (red), and which received a relatively lower volume of attacks (yellow). As for the targeted sectors, these were IT, petroleum, utilities, defense, and aviation.
Source: ClearSky
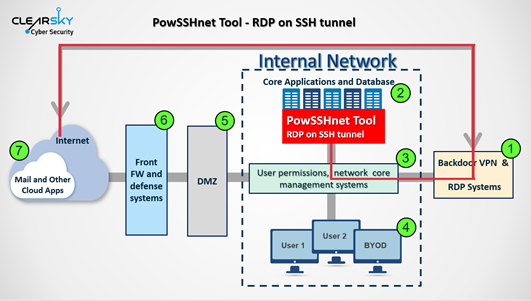
From 2016 and until late 2019, the Iranian hackers succeeded in penetrating corporate networks and stealing information from dozens of critical organizations. The main way inside these networks was via unpatched VPN and RDP services, which indicates that these skillful actors already knew about some of the flaws that were later discovered by white hat hackers. They were actively exploiting them a long time before the VPN makers sent out fixing patches. In most cases, though, they were just ready to exploit vulnerabilities that were published by researchers. For example, the actors managed to weaponize exploits for the Pulse Secure Connect, Global Protect, and the Fortinet FortiOS VPN quickly after DEVCORE’s Meh Chang and Orange Tsai made a relevant presentation at Black Hat USA 2019.
ClearSky reports that Iranian hackers shouldn’t be considered inferior to Russian or Chinese state-supported actors at all. They say that, in fact, they have compelling offensive capabilities, exploiting 1-day flaws in brief periods of time, even in a couple of hours in some cases. Considering this, it means that they remain a menace even for system administrators who act responsibly and apply patches within a couple of days. These actors are always on alert for whatever useful things they can get, and they are professionals, very quick to launch novel attacks when working as a larger team.