Infections of Commodity Malware on macOS on the Rise Again
- Hackers are buying an old but revived macOS malware from the dark web to steal people’s credentials.
- The particular strain has six years of history, was retracted at some point, and now returned possibly through a new developer.
- The refreshed re-selling network is now pretty extensive, even reaching to the clearnet.
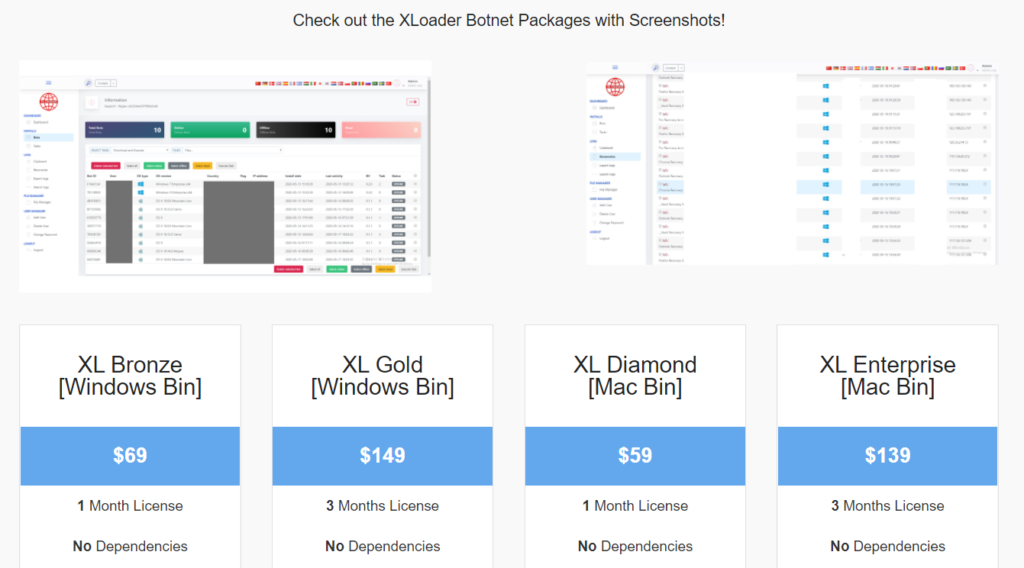
Users of macOS are currently facing a surge in infection of ‘XLoader’ (not to be confused with the Android strain), a commodity malware sold on various dark web locations to anyone wishing to launch attacks against Apple’s OS. The price ranges between $50 and $150, depending on the duration of the reseller's licensing and profit margin. Still, according to the stats presented by Check Point researchers today, the volume of sales is constantly increasing.
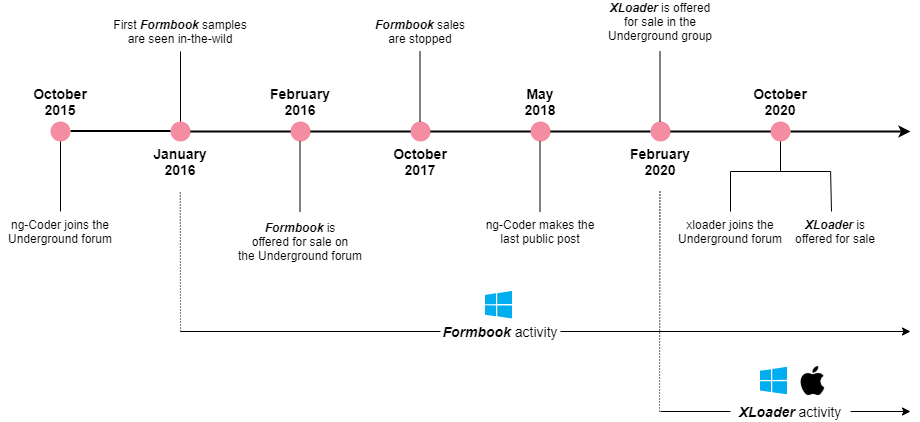
XLoader isn’t really a new malware, but more of a re-spin of a malicious piece of software that first appeared in the wild six years ago, known then as “Formbook.”
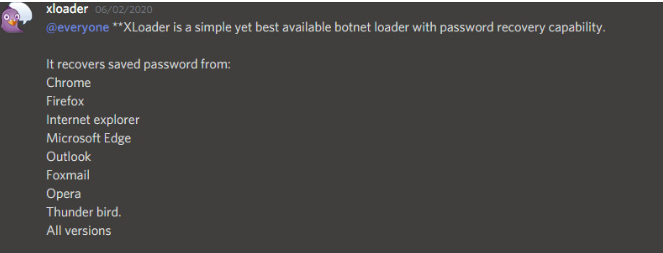
This is an info-stealer that can harvest credentials from web browsers, capture screenshots, monitor keystrokes, and log them for exfiltration to the C2, as well as download and execute additional files from the actors’ infrastructure. All in all, a powerful and versatile tool that can do a lot if left undetected.
In May 2018, the original author of Formbook published a statement saying that their intention was to introduce a simple spyware, not to see the tool being used to support email campaigns. As such, the tool was retracted, and everyone who was using it for purposes outside the intended scope had their license revoked. But those who had it continued using it, albeit linking it to their own servers now.
In February 2020, XLoader appeared on the dark web, advertised as an all-around credentials stealer. By the end of the year, it was being sold on the same forum that was originally selling Formbook, even featuring the exact same price tags for the same licensing package options.
Check Point finds it possible that the original author sold the code to a new developer or a new network of resellers. However, there are some clear signs of the author still being actively involved, at least up to a limited point.
The XLoader grew so popular in 2021 that it got a clearnet site and a seemingly legitimate presentation - offered at a slightly higher cost compared to dark web forums, though. These sites are unlikely to be connected to the original author. Still, they are rather set up and operated by opportunistic actors who are looking to make money by selling something “hot” to anyone interested.
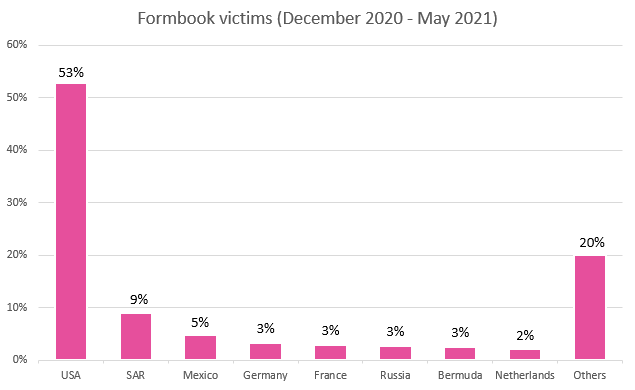
Between December 2020 and June 2021, Check Point logged XLoader presence in at least 69 countries around the world, with most infections targeting US-based systems. From the 90,000 domains used in network communications by the malware, only 1,300 are real C2 servers, which is a trick deployed to fool researchers and their sandbox traps. The remaining domains are all legitimate, which obviously don’t respond to the malicious traffic they receive from XLoader, so this whole approach makes the discrimination between real and fake servers difficult.