New Version of the XLoader Malware Comes With More Luring Tricks
- XLoader 6.0 brings new tricks, new code, and more sophisticated deployment methods.
- It all starts with a phishing link inside an unsought SMS message, and it escalates from there.
- The malware is capable of stealing even more information from the device, further supporting its phishing actions.
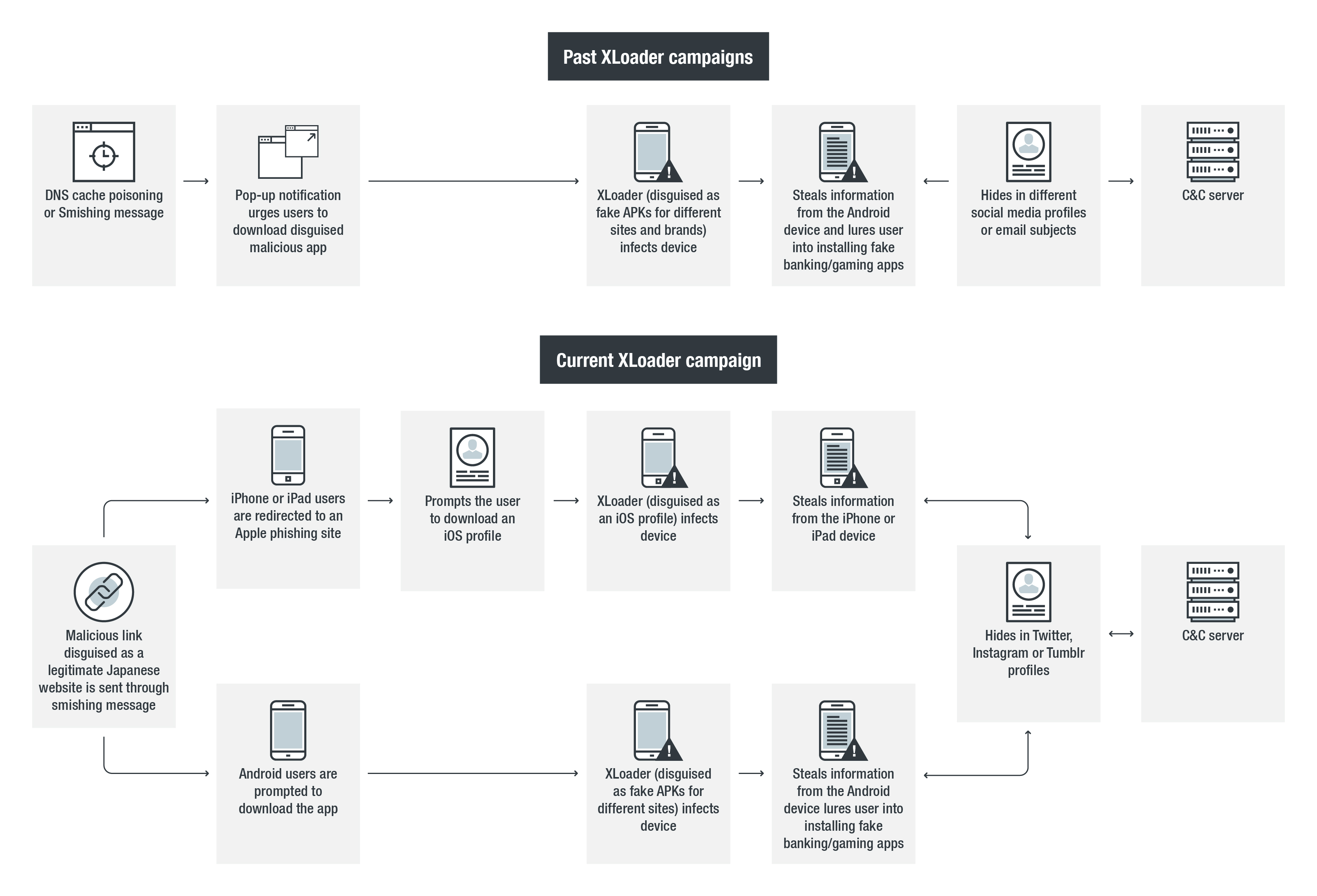
Trend Micro researchers have noticed the circulation of an updated XLoader variant that features new deployment techniques as well as significant changes in its functional code. This new sixth major version is making use of fake websites that mimic those of a Japanese mobile phone operator to trick people into downloading a fake APK (Android application package) which supposedly is a security app. The link to the phony website is sent to the potential victims through an SMS, while the fake APK is nothing else than the XLoader malware.
image source: blog.trendmicro.com
On the condition that the user has enabled the setting to “trust unknown sources” on their Android device, the XLoader APK is installed and then pushes notifications that urge the victim to install a set of fake banking apps. The apparent motive behind this is to trick the user into entering their banking login credentials, so as to send everything to the C&C server. Finally, the malware is also hiding a data-stealing snippet on Twitter, Instagram, and Tumblr, so nothing goes undetected there either. While hiding in social media isn’t something new for XLoader, support for Twitter was added on this latest version.
image source: blog.trendmicro.com
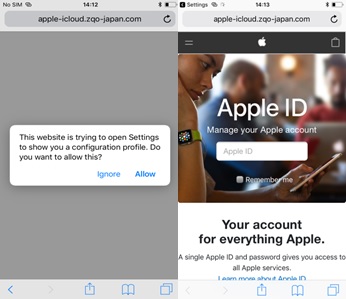
iOS users are not left out of the party, as XLoader uses a different, and dedicated method of infection for them. Instead of a fake app, iOS users are directed to a fake website that prompts them to download a malicious configuration profile (XML file). The trick is to make the website non-functional, and claim that the iOS profile will fix the network problem. Credulous users who believe this will be then directed to a polished Apple phishing site that asks them to enter their Apple ID. Of course, any information that’s inputted here will go directly to the C&C server.
image source: blog.trendmicro.com
In regards to the information exfiltration potential of XLoader 6.0, the malware is now empowered by a new “getPhoneState” command that enables it to collect info such as: the Unique device identifier (UDID), International Mobile Equipment Identity (IMEI), Integrated Circuit Card ID (ICCID), Mobile equipment identifier (MEID), Version number, and the Product number. The version of the iOS, in particular, is a crucial piece of information that allows XLoader to adjust its configuration profile installation process accordingly.
Trend Micro researchers warn that while version 6.0 is currently under extensive deployment, version 7.0 is already out there, luring users by posing as a South Korean pornography app. This goes to show that successful and especially nasty malware tools like the XLoader are expected to continue evolving throughout 2019. Until this malware is nullified, you should not download APKs and iOS profiles from untrusted sources, refrain from clicking on links contained in unsolicited SMS messages and use some kind of a mobile security product.
Have you had any previous adverse experience with XLoader? Share the details with the rest in the comments section below, and don’t forget to check our Facebook and Twitter pages for more tech news and stories like this one.