Indian Government Emails Found Wandering on the Dark Web
- Hundreds of email IDs and plaintext passwords belonging to Indian organizations are available on the dark web.
- The emails may have been shared among crooks for quite some time, but this has just been discovered.
- It is time for crucial government entities to use 2FA, and even better, 2SV physical security keys.
Researcher Sai Krishna Kothapalli has found 3202 email IDs on the dark web, belonging to people working on the Indian government and various organizations of the state. The infosec expert has been collecting data from dumps on the dark web for the past four years, creating a humongous database of 1.8 billion email IDs and passwords. According to him, approximately 85% of the passwords he holds are in plain text form, while others have been dehashed by hackers throughout the years. After analyzing this trove of data, Kothapalli recently found some ending with “.gov.in”.
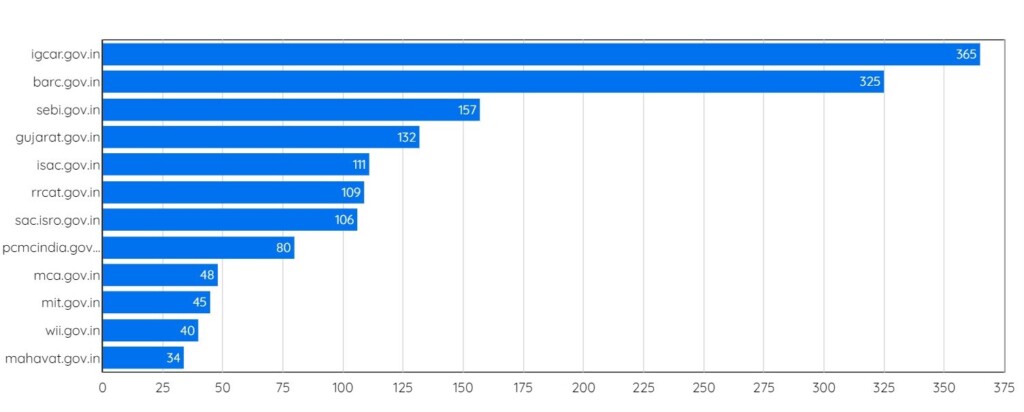
The 365 email IDs belong to employees of the ‘Indira Gandhi Centre for Atomic Research’. Trailing just behind is the ‘Bhabha Atomic Research Centre’ with 325 email IDs. In third place, there is the ‘Securities and Exchange Board of India’ with 157 emails. In total, the 3202 emails belonging to 12 entities, as shown in the graph below.
The researcher tried to correlate his findings with the "Have I Been Pwned" service and found no entries there, so this was a fresh discovery. The conclusion that he drew was that this data must be the product of a targeted phishing campaign since there were no recorded breaches. This means that the employees who have had their IDs and passwords stolen could be at risk of having their accounts taken over. The employees could have changed their passwords in the meantime, but the chances of stuffing attacks against other accounts belonging to the same people remain high.
The researcher is still investigating the data and is in the process of contacting the governmental organizations to alert them about his findings. He points out that when he started investigating this, he was approached by someone who posed as an NDTV reporter. After additional research, he discovered that the email accounts used to contact him had been compromised in the previous months and that the news from back in the time attributed this to North Korean hackers.
The North Korean hackers sent hacking emails to the former chairman of the Atomic Energy Commission of India(AECI) and the Secretary to the Government of India and the Director of the Bhabha Atomic Research Centre(BARC). pic.twitter.com/UCv01aCq2X
— IssueMakersLab (@issuemakerslab) November 2, 2019
So, could this all be the work of state-supported actors from North Korea? It’s quite possible, but nothing can be said with certainty until the investigation is concluded. Right now, the important part is to secure the email accounts by resetting the credentials as soon as possible. Also, and as the researcher points out in his report, it is high time for the government and its organizations to adopt two-factor authentication for the email accounts of their employees, or even better, physical security keys.