Hundreds of Millions of Android Devices Still Vulnerable to Fixed Flaw
- Android apps using an outdated version of the Play Core Library are vulnerable to LCE attacks.
- Some of the negligent apps are extremely popular, counting hundreds of millions of users.
- Unfortunately, the flaw is pretty simple and easy to exploit and also widely-known by now.
Even though Google has patched the CVE-2020-8913 since August 2020, there are still quite a few applications that continue to use the vulnerable version of the affected library, thus remaining exploitable. This is according to a CheckPoint report that dives deeper into the problem, warning users and app developers alike.
Some of the most popular applications that remain vulnerable to CVE-2020-8913 in their latest available versions on the Google Play Store are the following:
- Viber 14.1.0.16 – 500 million downloads
- Booking.com 24.8.2 – 100 million downloads
- XRecorder 1.4.0.3 – 100 million downloads
- Moovit 5.56.0.459 – 50 million downloads
- PowerDirector 7.5.0 – 50 million downloads
- IndiaMART 12.7.4 – 10 million downloads
- Microsoft Edge 45.09.4.5083 – 10 million downloads
- Grindr 6.32.0 – 10 million downloads
- OkCupid 47.0.0 – 10 million downloads
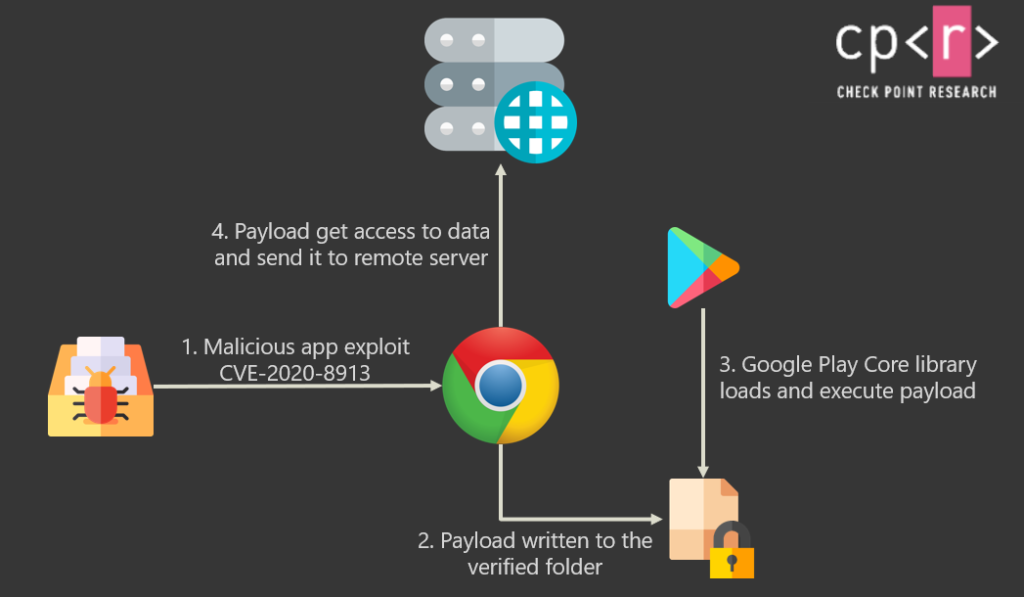
So, what exactly are the above missing? Simply put, they are using an older and unpatched version of the "Google Play Core Library," which is vulnerable to Local-Code-Execution (LCE).
Apps use this library to help them manage incoming data packs, such as additional resources or updates. The impact of the LCE flaw includes code injection that leads to unauthorized access, interception of 2FA codes, messages from IM apps, and stealing of online banking credentials.
It is without a doubt a very severe vulnerability, and as demonstrated in the following video, it’s pretty easy to exploit. The CheckPoint researchers demonstrate how a “hello world” app can call the exported intent in the vulnerable app to push a malicious file into the victim’s device. We should note that the Google Chrome app used in this demonstration is not vulnerable to CVE-2020-8913 in its latest version.
Of course, the Android apps that have not jumped to the patched version of the Google Play Core Library aren’t limited to the above list. CheckPoint has used its “SandBlast Mobile” threat detection tool to estimate how many apps in the Play Store are still vulnerable to LCE attacks by September 2020, and they’ve found that 8% of them were risky. Of those using the particular library, only 48.5% had bumped to the secure version.
Unfortunately for the end-users, there’s nothing they can do about this flaw besides uninstalling the vulnerable apps or using a mobile security solution. The app developers have to fix the problem themselves by using the library’s fixed version, but they are already several months late at that.