Hackers Could Be Listening to Your Conversations Through the Comcast Remote
- Comcast’s remotes were vulnerable to take-over due to a nasty bug in incoming data packet validation.
- Hackers standing up to 20 meters away could activate the remote’s in-built microphone and have the audio beamed to them.
- Users wouldn’t realize a thing, as there would be no indication that something bad is happening other than battery drain.
Remotes that feature microphones to make navigation on streaming and media consumption platforms easier are gradually becoming a ubiquity. Still, as security researchers from Guardicore warn, these devices may constitute a severe privacy liability.
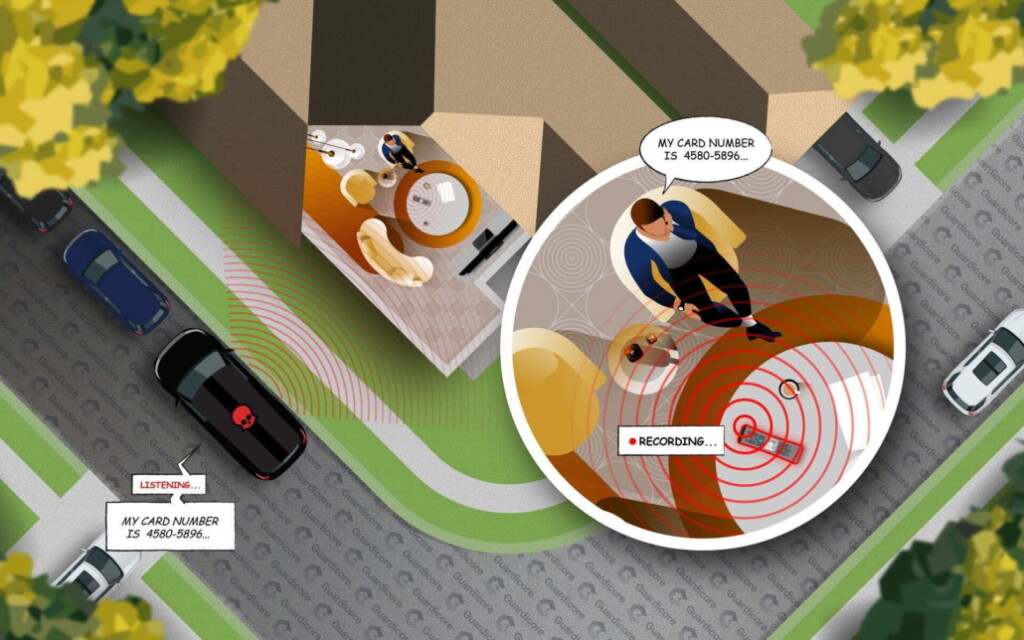
According to the research paper published today, the XR11 voice remote that accompanies the Comcast Xfinity X1 set-top box can be hacked, and someone could spy on the user’s conversations.
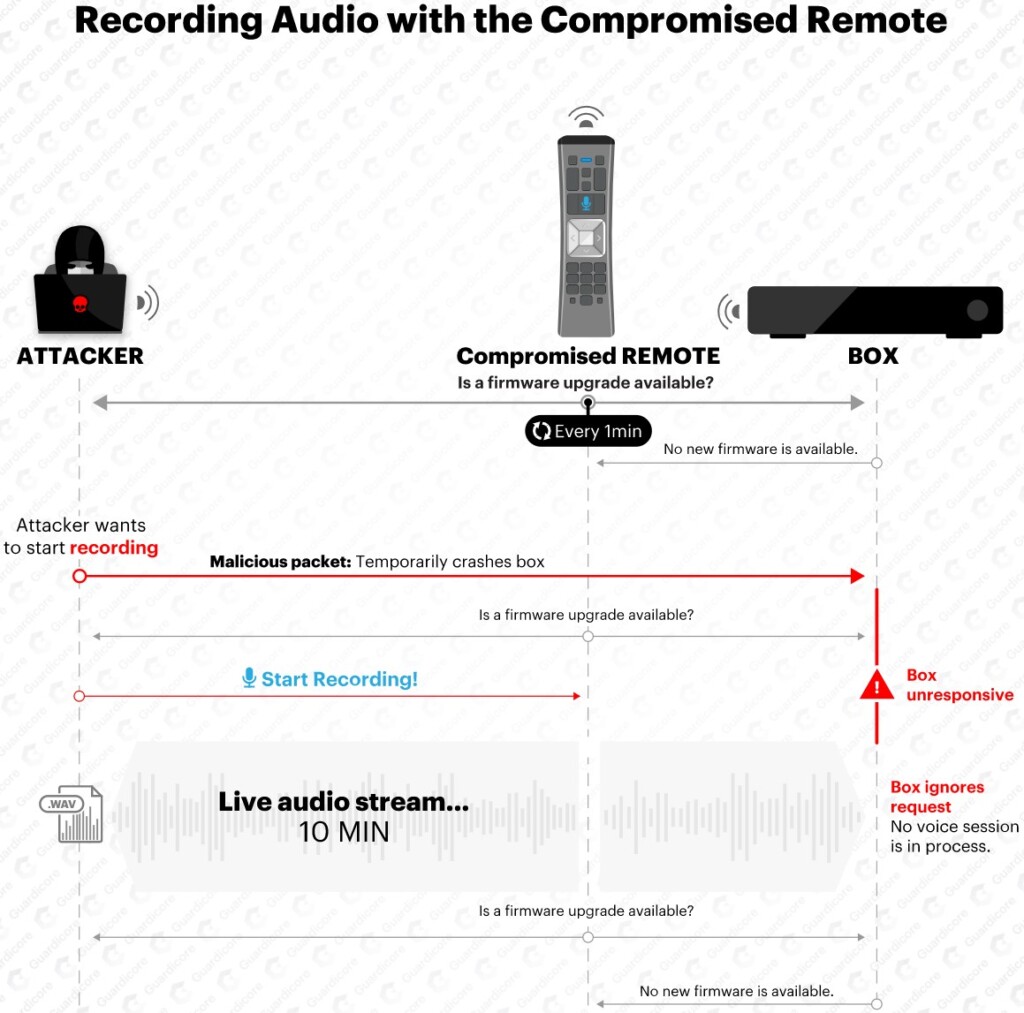
No physical contact or tampering with the device is required, and all that is needed for the take-over is a cheap RF transceiver. The researchers managed to take over a remote using this method and listen to all conversations from the testing room while parked in a car outside the house, almost 20 meters away. For capturing the signals, they used a 16dBi antenna, which is also an inexpensive piece of equipment.
Read More: Vulnerabilities in Amazon’s Alexa Enable Hackers to Do Various Nasty Stuff
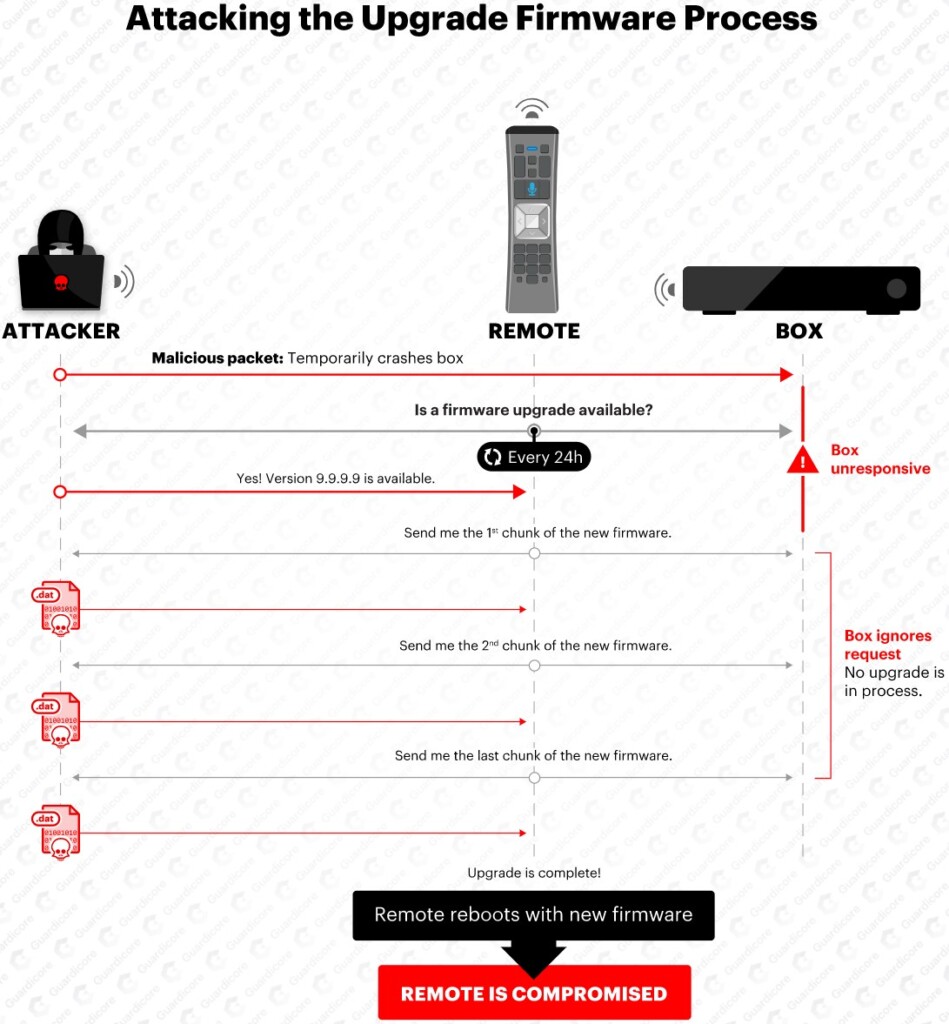
Because the remote uses radio frequency (FR) for communication and not a classic IR blaster, someone could contact it from a distance. Also, this remote supports over-the-air firmware upgrade, so it was made to accept incoming data. Even worse, it doesn’t validate the signatures of these firmware updates, so anyone can send an upgrade package to the device and have it installed without much trouble.
The team reverse-engineered both the firmware and the software and found a vulnerability in the way the remote handles incoming RF data packets. While the remote uses some form of encryption for the incoming packets, finding the key to it wasn’t very hard. The researchers figured that sending RF packets that didn’t have the encryption-activation bit into them didn’t stop them from being accepted by the remote.
So, as long as the attacker is within the remote’s RF range, they can send a new firmware upgrade. The researchers developed a new firmware named “WarezTheRemote,” which allows remote activation of the microphone. Thus, hackers from afar can push the “recording” button and have the remote to broadcast the data back to them. Of course, there are many little steps and details that have to be set correctly for the take-over, but this is the outline of how the attack works.
The devices that are vulnerable to this attack are those running firmware version older than 1.1.4.0. It has been several months since Comcast was informed of this and pushed the update, so make sure that you apply it if you haven’t already. Comcast sees all devices as patched since September 24, but if you haven’t gone online since then, your remote may continue to run a vulnerable firmware version.
This is just an example that highlights a new source of security problems for home IoT devices. We already have multiple microphones “planted” inside our homes, so all it takes for hackers to listen to our conversations is finding a way to take over those.