Vulnerabilities in Amazon’s Alexa Enable Hackers to Do Various Nasty Stuff
- Researchers figure ways to inject code in Amazon’s sub-domains, essentially gaining control of Alexa’s account configurations.
- A hacker could exploit the flaws to add or remove skills, access the user’s voice history, and steal PII.
- Amazon has fixed the reported issues, but this is another example of the risks that come with IoT deployment.
Amazon’s intelligent virtual assistant known as “Alexa,” which lives inside many hundred million IoTs around the globe, has been found to be vulnerable to a set of flaws. Researchers from Check Point have dug deep to unearth flaws in Alexa’s functionality, and they’ve found cross-origin resource sharing (CORS) misconfigurations and cross-site scripting (XSS) vulnerabilities.
These could be exploited to grab the user’s CSRF token and perform actions on the target IoT device with user privileges. The researchers focus particularly on the possibilities that arise from fiddling with the “skills” installed on the device.
“Skills” are like add-ons for Alexa-powered IoTs, enabling users to extend their smart devices’ functionality. From third-party weather apps to configuration utilities for other smart devices connected in the network, “skills” are widely used in the Alexa ecosystem for a multitude of reasons. Domino’s Pizza has a one for ordering, personal trainers have their own skills for fitness sessions, Audible has one for listening to book narrations, Philips Hue lights have a configuring skill, air purifiers, security cams, thermostats, etc., all have skills - so you can get the idea.
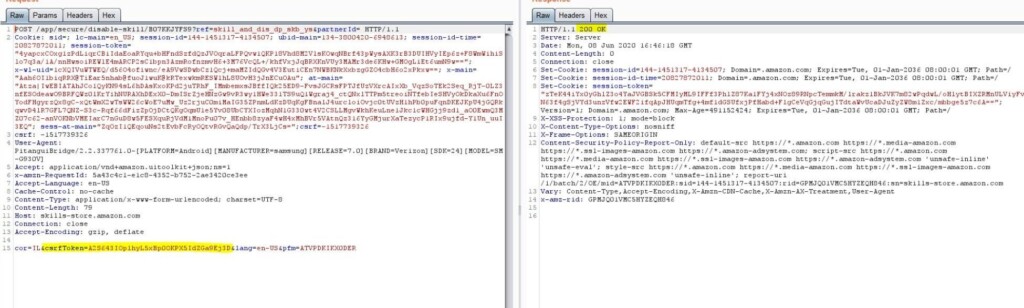
Source: Check Point
By exploiting the above flaws, a hacker could check which skills are installed on the target Alexa account, remove any skills, or even add skills silently.
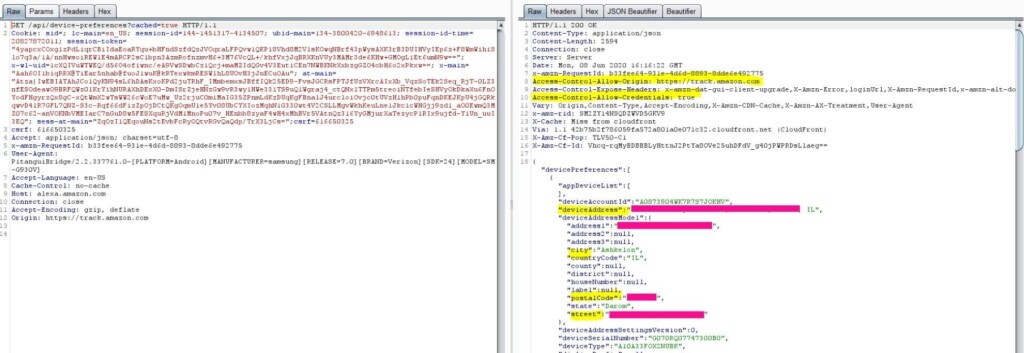
Moreover, the actor would be in a position to access the victim’s voice history and even get whatever personal information is linked with the compromised Alexa account.
The exploit begins with the user being tricked into clicking a malicious link that directs them to amazon.com. There, the attacker injects code and sends an Ajax request with the user’s cookies to “amazon.com/app/secure/your-skills-page” (sub-domain). That would fetch the installed skills list and a valid CSRF token. From there, the malicious actor can do what we described above as if he is the user.
Source: Check Point
Before you start panicking, we should make it clear that Amazon has now fixed the reported vulnerabilities, so the PoC that is shared by Check Point is only meant to demonstrate what was possible until last month. Amazon’s sub-domains are no longer vulnerable to XSS exploits, so the issue has been fixed on the server side. This also means that updating your IoT’s firmware doesn’t matter for this particular flaw.
All that said, you should keep in mind that IoTs are inherently vulnerable, and malicious actors are now spending great amounts of time and effort to find ways to breach them since they can be used as doors to infect other, more critical systems. If you enjoy the aid of AIs like Alexa, keep them connected on a separate, dedicated network from the one that serves your most valuable systems.