A Global Spam Campaign Is Exploiting the Support to Rights Movements
- Actors are distributing the Trickbot banking trojan via a global spamming campaign that exploits the BLM movement.
- Most of the emails of this campaign are sent to the United States and Canada, but Cyprus is also a target.
- The topics of the messages concern the ongoing human rights protests, and the senders are supposedly state representatives.
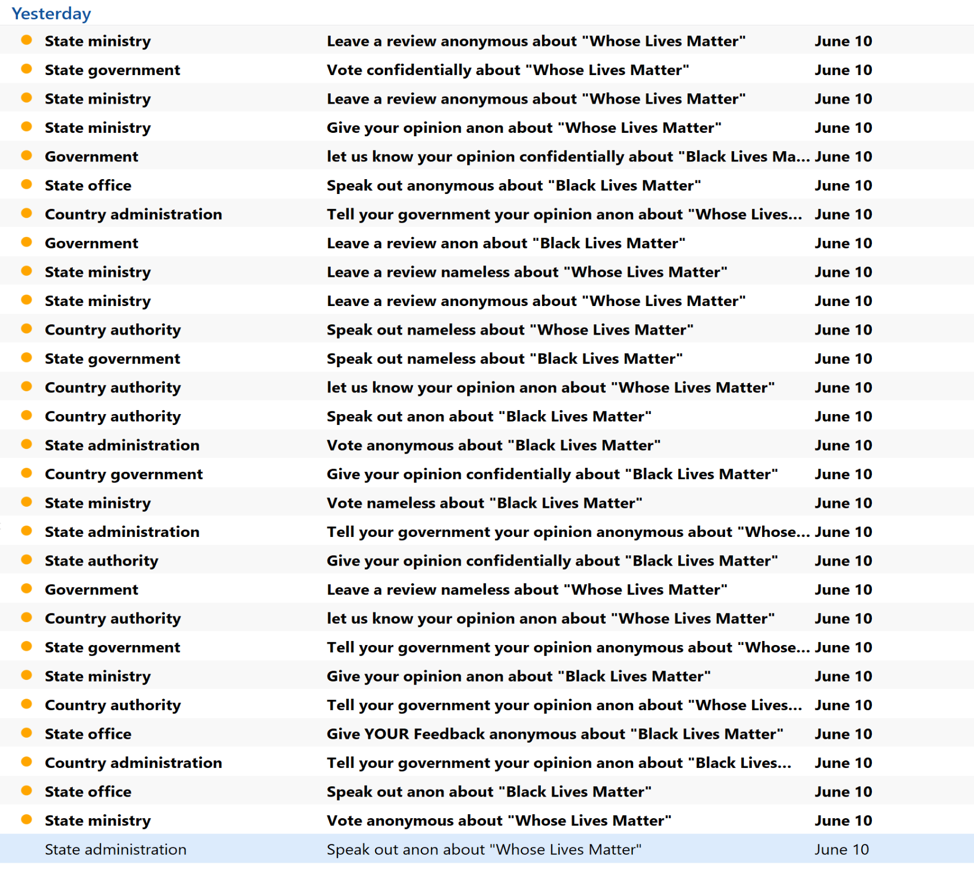
Malicious actors are always on the lookout to exploit whatever is trending, and there’s always something hot in any given period. Researchers from the FortiGuard Labs have noticed a new global spam campaign which is exploiting the “Black Lives Matter” movement, distributing a large number of emails that use relevant subject lines. These messages come with malicious Microsoft Word attachments that the recipient is urged to open and review. The senders are supposedly the “state government”, the “county administration”, a “ministry”, or a state office.
Source: Fortinet Blog
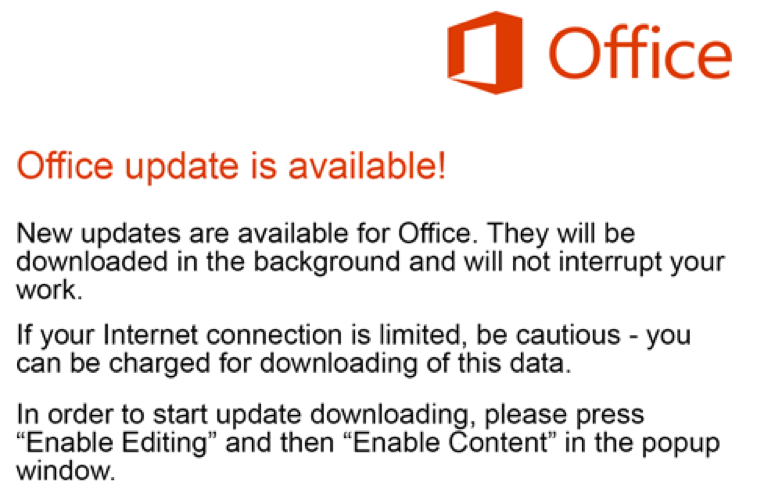
Upon opening the document that’s attached to the email, users are met with a warning message that informs them of new updates that are available for the Office. Supposedly, they need to “Enable Content” to get these updates, but all the actors are trying to do is to convince the users to enable the macros on their suite. If they do it, the document loads a first-stage downloader, then creates a memory region to unpack the actual payload and fetches Trickbot. The malware is then establishing a connection with the C2 infrastructure, and the game is on.
Source: Fortinet Blog
If you have been following the news here, you may remember that Trickbot is one of the most widely used and persistent threats in the spamming world. It is able to steal sensitive Windows Active Directory data, abusing legitimate cloud services to stay undetected, and having the ability to pass through email spam filters by using Google URL redirection techniques. In general, Trickbot is a powerful banking trojan that has many tricks up its sleeve, and global spam campaigners are still opting to use it.
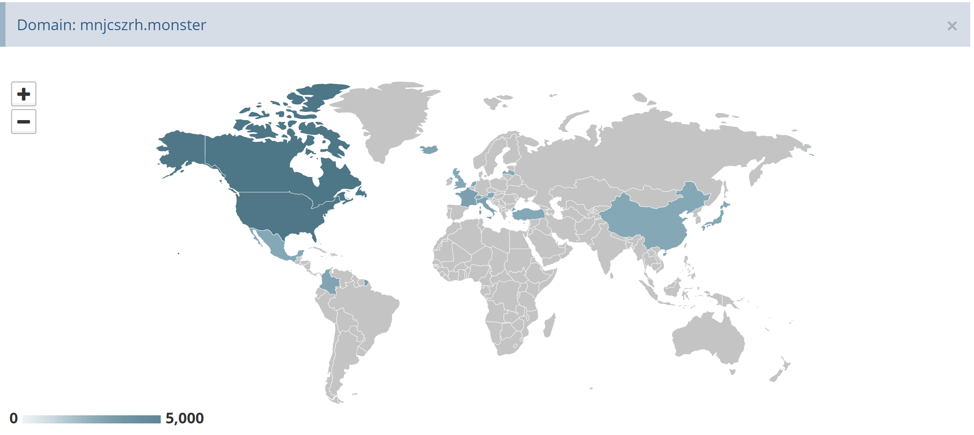
Fortinet noticed the spike in this campaign's activity on June 10, 2020, with targets in the US and Canada receiving the vast majority of the spam volume. France, Cyprus, and Italy are also seeing some activity, although much less. Some spam spreading addresses are also sending messages to targets in Thailand, while others focus on the United Kingdom. Interestingly, Cyprus consistently appears as a target in all cases.
Source: Fortinet Blog
Besides reviewing firewall settings and spam filtering rules, the single and most simple thing you can do to stay safe from threats of this kind is to keep macros on your MS Office suite disabled. Even better, do not download any document attachments that come via unsolicited messages, no matter what's on the subject line of who is supposed to be the sender.