Gamers Targeted with Lua-Based Malware Disguised as Cheating Script Engines
- A sophisticated Lua-based malware campaign was seen leveraging people’s interest in game cheats.
- The hackers host and distribute malicious payloads through malicious GitHub ZIP archives.
- Infostealers are also part of the deployed malware once the target systems are compromised.
Users seeking game cheats have become targets of a sophisticated malware campaign. The attackers are enticing gamers to download a Lua-based malware by masquerading it as legitimate cheating script engines, according to a new Morphisec security report.
This malware, which has been detected globally, leverages the popularity of Lua gaming engine extensions among student gamers.
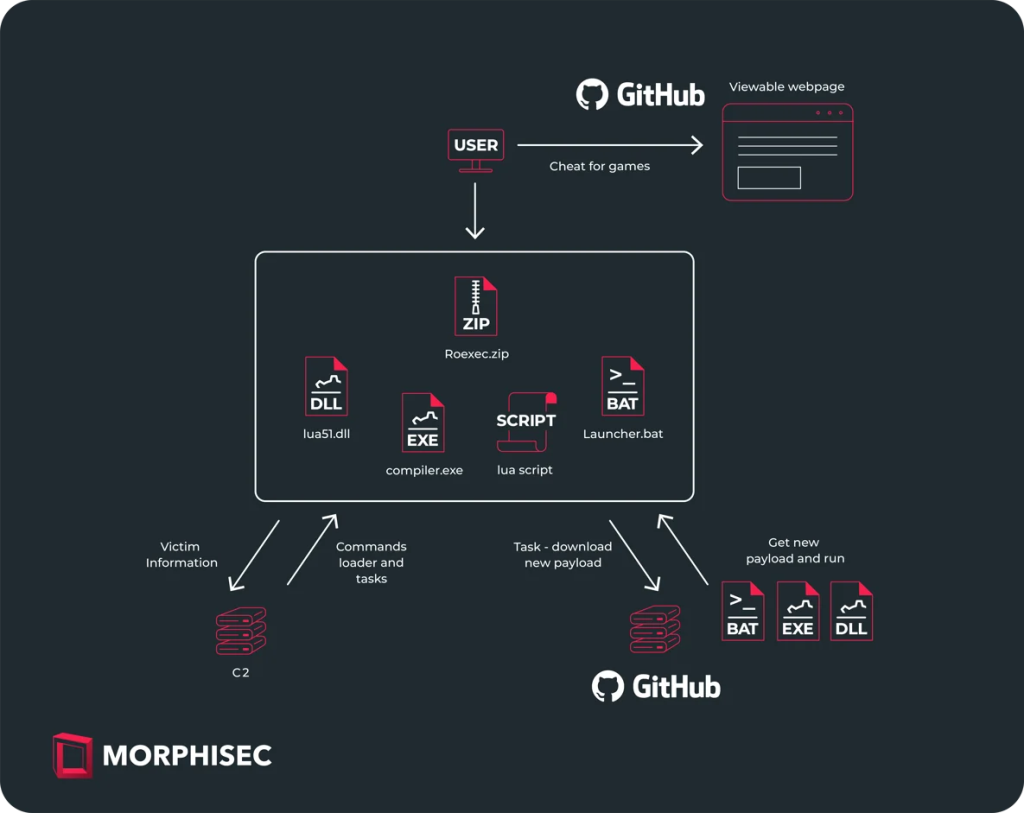
Originally documented by OALabs in March 2024, the campaign uses a Lua-written malware loader. The attackers exploit quirks in GitHub's platform to host and distribute malicious payloads through booby-trapped ZIP archives.
GitHub has actively disabled user accounts and content that violate its Acceptable Use Policies, prohibiting hosting content supporting unlawful activities, including malware distribution.
The recent analysis highlights a shift in the malware's delivery mechanism, as threat actors are now deploying obfuscated Lua scripts rather than compiled Lua bytecode to reduce detection risks. The infection vector remains unchanged, with users directed to fake websites hosting malicious archives.
The ZIP archive typically includes a Lua compiler, a runtime interpreter DLL, an obfuscated Lua script, and a batch file to execute the script. The malicious Lua script establishes a connection with a command and control (C2) server, facilitating persistent system compromise or the deployment of additional payloads like the Redone Stealer.
Infostealers continue to rise in prominence, with harvested credentials often sold on the Dark Web. The RedLine information stealer, in particular, has a significant market presence.
Recent reports from Kaspersky reveal parallel campaigns targeting users searching for pirated software, distributing the SilentCryptoMiner via AutoIt compiled binaries. These attacks have predominantly targeted regions, including Russia, Belarus, and India.
The cybersecurity landscape indicates a growing trend of malware distributed through unconventional channels, such as encrypted messaging apps and video platforms, often masked as cryptocurrency-related content.